Importing the IdP certificate and metadata on the FortiAuthenticator
- On the FortiAuthenticator, go to Fortinet SSO Methods > SSO > SAML Authentication and import the IdP metadata and certificate downloaded earlier.
- Select Download SP metadata – this will be uploaded to the Centrify tenant.
- Then go to Fortinet SSO Methods > SSO > FortiGate Filtering and create a new FortiGate filter.
This will automatically fill the IdP fields (as shown in the example). Make sure to select OK to save these changes.


Enter a name and the FortiGate’s wan-interface IP address, and select OK.
Once created, enable Fortinet Single Sign-On (FSSO). Select Create New to create an SSO group filtering object (as shown already created in the example), and select OK to apply all changes.
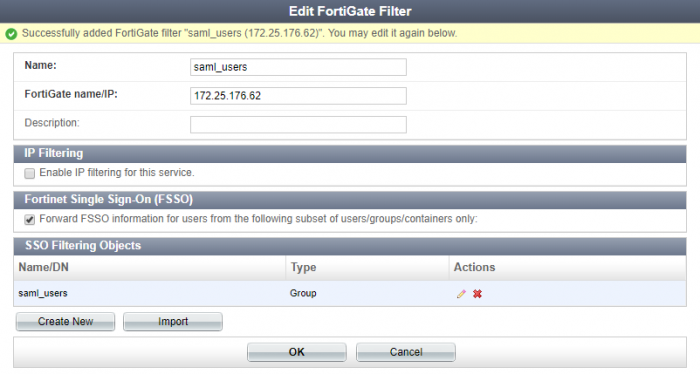
Note that the name entered for the filter must be the same as the group name created for SAML users (saml_users). The two user groups must have the exact same name or SSO information will not be pushed to the FortiGate.

