Provision the remote LDAP server on FortiAuthenticator
Provision the remote LDAP server on FortiAuthenticator
To provision the remote LDAP server:
- In FortiAuthenticator, go to Authentication > Remote Auth. Servers > LDAP, and click Create New.
- In the Create New LDAP Server window, set the following:
- Name: Enter a name, for example azure.fortixpert.com.
- Primary server name/IP: Enter the Secure LDAP IP.
- Bind type: Regular.
- Username/Password: Enter a username and password that can access MS Azure DS to perform directory lookups.
- Base distinguished name: Leave blank.
- In the Query Elements section, set the following:
- Pre-defined templates: Select Microsoft Active Directory and click Apply.
- Force use of administrator account for group membership lookups: Enabled.
- In the Secure Connection section, set the following
- Secure Connection: Enabled.
- Protocol: LDAPS.
- CA Certificate: Select the Root CA certificate for the wildcard certificate that was uploaded to MS Azure to use with the Secure LDAP connector.
- Select the lookup icon next to Base distinguished name. Choose the base DN for your user accounts, for example DC=fortixpert,DC=com. Click OK.

- Click OK to save the remote LDAP server configuration.
To import remote user accounts:
- Go to Authentication > User Management > Remote Users. Confirm LDAP is selected at the top of the page, and click Import.
- Under Import Remote LDAP User, complete the following:
- Remote LDAP Server: Select the Azure remote LDAP server.
- Action: Select Import users, and click Go to view a list of users within your Azure directory.
- Select the users you wish to be able to connect to the wireless network using their Azure based account.
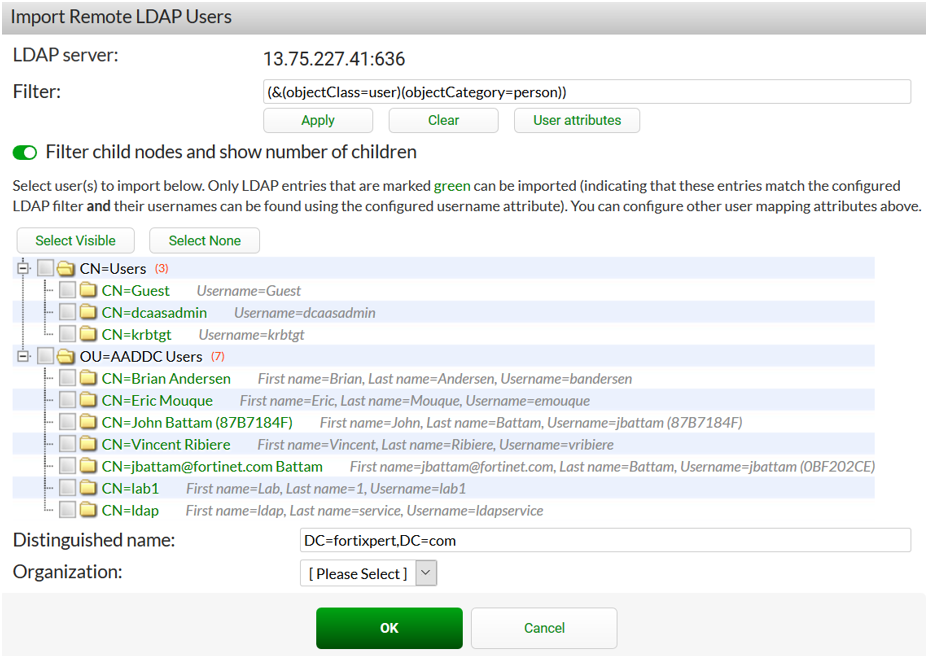
- Click OK.
To set up a remote user sync rule:
- Go to Authentication > User Management > Remote User Sync Rule, and click Create New.
- Under Create New Remote LDAP User Synchronization Rule, set the following:
- Name: Enter a name, for example Azure_Remote_Sync.
- Remote LDAP: Select your Azure remote LDAP server.
- Base distinguished name: This setting can be left as the default, for example DC=fortixpert,DC=com.
- Under Synchronization Attributes, set the following:
- Token-based authentication sync priorities: Enable None.
- Sync every: Select the sync frequency. In production environments, this should be set to 30 minutes or more depending on the number of users being synchronized.
- Sync as: Remote LDAP User.
- User role for new user imports: User.
- Leave all other settings in their default states, and click OK.
To create a new realm:
- Go to Authentication > User Management > Realms, and click Create New.
- Under Create New Realm, set the following:
- Name: Enter the realm name, for example fortixpert.com.
- User source: Select the remote LDAP service from the dropdown box.
- Click OK.
Provision the remote LDAP server on FortiAuthenticator
To provision the remote LDAP server:
- In FortiAuthenticator, go to Authentication > Remote Auth. Servers > LDAP, and click Create New.
- In the Create New LDAP Server window, set the following:
- Name: Enter a name, for example azure.fortixpert.com.
- Primary server name/IP: Enter the Secure LDAP IP.
- Bind type: Regular.
- Username/Password: Enter a username and password that can access MS Azure DS to perform directory lookups.
- Base distinguished name: Leave blank.
- In the Query Elements section, set the following:
- Pre-defined templates: Select Microsoft Active Directory and click Apply.
- Force use of administrator account for group membership lookups: Enabled.
- In the Secure Connection section, set the following
- Secure Connection: Enabled.
- Protocol: LDAPS.
- CA Certificate: Select the Root CA certificate for the wildcard certificate that was uploaded to MS Azure to use with the Secure LDAP connector.
- Select the lookup icon next to Base distinguished name. Choose the base DN for your user accounts, for example DC=fortixpert,DC=com. Click OK.

- Click OK to save the remote LDAP server configuration.
To import remote user accounts:
- Go to Authentication > User Management > Remote Users. Confirm LDAP is selected at the top of the page, and click Import.
- Under Import Remote LDAP User, complete the following:
- Remote LDAP Server: Select the Azure remote LDAP server.
- Action: Select Import users, and click Go to view a list of users within your Azure directory.
- Select the users you wish to be able to connect to the wireless network using their Azure based account.

- Click OK.
To set up a remote user sync rule:
- Go to Authentication > User Management > Remote User Sync Rule, and click Create New.
- Under Create New Remote LDAP User Synchronization Rule, set the following:
- Name: Enter a name, for example Azure_Remote_Sync.
- Remote LDAP: Select your Azure remote LDAP server.
- Base distinguished name: This setting can be left as the default, for example DC=fortixpert,DC=com.
- Under Synchronization Attributes, set the following:
- Token-based authentication sync priorities: Enable None.
- Sync every: Select the sync frequency. In production environments, this should be set to 30 minutes or more depending on the number of users being synchronized.
- Sync as: Remote LDAP User.
- User role for new user imports: User.
- Leave all other settings in their default states, and click OK.
To create a new realm:
- Go to Authentication > User Management > Realms, and click Create New.
- Under Create New Realm, set the following:
- Name: Enter the realm name, for example fortixpert.com.
- User source: Select the remote LDAP service from the dropdown box.
- Click OK.



