General settings
FortiAuthenticator units listen for requests from authentication clients and can poll Windows AD servers.
To configure FortiAuthenticator FSSO polling:
- Go to Fortinet SSO Methods > SSO > General to open the Edit SSO Configuration window. The Edit SSO Configuration window contains sections for FortiGate, FSSO, and user group membership.
- In the FortiGate section, configure the following settings:
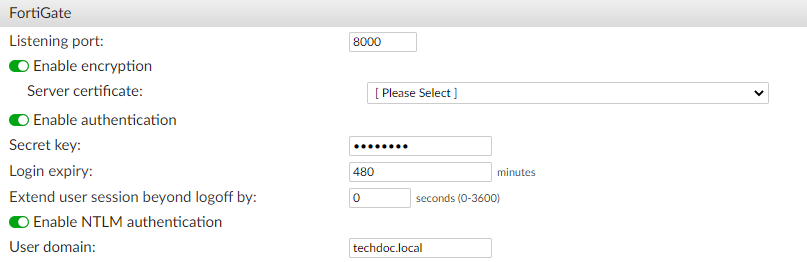
Listening port Leave at 8000 unless your network requires you to change this. Ensure this port is allowed through the firewall. Enable encryption
Enable/disable encryption, then from the dropdown, select a server certificate. See End entities.
Note: When enabled, FortiGates connect over TLS, and FortiAuthenticator uses Fortinet CA-signed certificate as the TLS server certificate.
Enable authentication Select to enable authentication, then enter a secret key, or password, in the Secret key field. Login expiry The length of time, in minutes, that users can remain logged in before the system logs them off automatically. The default is 480 minutes (8 hours). Extend user session beyond logoff by The length of time, in seconds, that a user session is extended after the user logs off, from 0 (default) to 3600 seconds. Enable NTLM authentication Select to enable NTLM authentication, then enter the NETBIOS or DNS name of the domain that the login user belongs to in the User domain field. - In the Fortinet Single Sign-On (FSSO) section, configure the following settings:
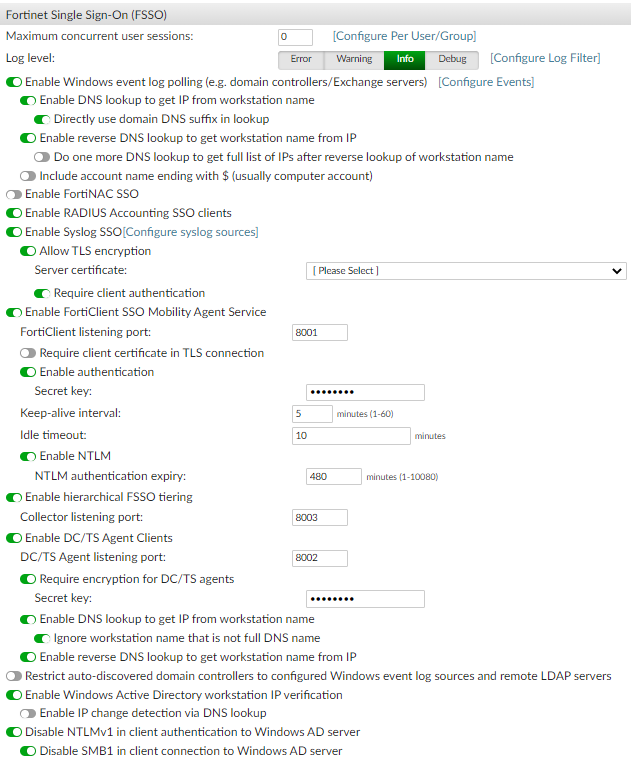
Maximum concurrent user sessions Enter the maximum number of concurrent FSSO login sessions a user is allowed to have. Use 0 for unlimited.
Select Configure Per User/Group to configure the maximum number of concurrent sessions for each user or group. See Fine-grained controls.
Log level Select one of Error, Warning, Info, or Debug as the minimum severity level of events to log.
Select Download all logs to download all FSSO logs to your management computer.
Enable Windows event log polling (e.g. domain controllers/Exchange servers) Select to enable Windows AD polling. This includes polling logon events from devices using Kerberos authentication or from Mac OS X systems.
Select Configure Events to select the Windows security event IDs to use in event log polling. Select from event IDs 528, 540, 672, 673, 674, 680, 4624, 4768, 4769, 4770, and 4776.
Enable DNS lookup to get IP from workstation name Select to use DNS lookup to get IP address information when an event contains only the workstation name. This option is enabled by default. Directly use domain DNS suffix in lookup Select to use the domain DNS suffix when doing a DNS lookup. This option is disabled by default. Enable reverse DNS lookup to get workstation name from IP Select to enable reverse DNS lookup. Reverse DNS lookup is used when an event contains only an IP address and no workstation name. This option is enabled by default. Do one more DNS lookup to get full list of IPs after reverse lookup of workstation name Reverse DNS lookup is used when an event contains only an IP address and no workstation name. After the workstation name is determined, it is used in the DNS lookup again to get more complete IP address information. This is useful in environments where workstations have multiple network interfaces. This option is disabled by default. Include account name ending with $ (usually computer account) Accounts that end in "$" used to exclusively denote computer accounts with no actual user, but in some cases, valid accounts imported from dated systems can feature them. This option is disabled by default. Enable FortiNAC SSO
Select to enable the retrieval of SSO sessions from FortiNAC sources.
Select Edit to choose one or more configured FortiNAC sources to use as SSO sources.
Select Configure FortiNACs to configure FortiNAC sources (under System > Administration > FortiNACs). For more information, see FortiNACs.
Enable Radius Accounting SSO clients Select to enable the detection of users sign-ons and sign-offs from incoming RADIUS accounting (Start, Stop, and Interim-Update) records. Enable Syslog SSO Select to enable Syslog SSO, and configure syslog sources. Allow TLS encryption
Enable to allow TLS encryption.
Server Certificate
From the dropdown, select one of the configured local server certificates.
Require client authentication
Enable to require that the client certificate must be signed by one of the configured local or trusted CA certificates.
Enable FortiClient SSO Mobility Agent Service Select to enable single sign-on (SSO) by clients running FortiClient Endpoint Security. For more information, see FortiClient SSO Mobility Agent. FortiClient listening port Enter the FortiClient listening port number. Require client certificate in TLS connection
Enable to require client certificate in TLS connection. This option is disabled by default.
Enable authentication Select to enable authentication, then enter a secret key, or password, in the Secret key field. Keep-alive interval Enter the duration between keep-alive transmissions, from 1 to 60 minutes. Default is 5 minutes. Idle timeout Enter an amount of time in minutes after which to logoff a user if their status is not updated. The value cannot be lower than the Keep-alive interval value. Enable NTLM Select to enable the NT LAN Manager (NTLM) to allow logon of users who are connected to a domain that does not have the FSSO DC Agent installed. Disable NTLM authentication only if your network does not support NTLM authentication for security or other reasons.
Enter an amount of time after which NTLM authentication expires in the NTLM authentication expiry field, from 1 to 10080 minutes (7 days).
Enable hierarchical FSSO tiering Select to enable hierarchical FSSO tiering. Enter the collector listening port in the Collector listening port field. Enable DC/TS Agent Clients Select to enable clients using DC or TS Agent. Enter the TCP or UDP port in the DC/TS Agent listening port field. Default is 8002.
Require encryption for DC/TS agents
Select to require authentication, then enter a secret key, or password, in the Secret key field.
Note: If this option is enabled, the TCP port is used and the UDP port is disabled. Otherwise, the UDP port is used and the TCP port is disabled.
Enable DNS lookup to get IP from workstation name
Select to use DNS lookup to get IP address information when a client contains only the workstation name. This option is enabled by default.
FortiAuthenticator attempts to obtain the workstation IP address using DNS lookup if the logon request contains only the workstation name. If the initial lookup fails, FortiAuthenticator will retry every 10 seconds for the following 5 minutes.
Ignore workstation name that is not full DNS name
Select if the DNS server does not support a workstation name that is not a full DNS name, otherwise service delay may occur. This option is enabled by default.
Enable reverse DNS lookup to get workstation name from IP
Select to enable reverse DNS lookup. Reverse DNS lookup is used when a client contains only an IP address and no workstation name. This option is enabled by default.
Restrict auto-discovered domain controllers to configured Windows event log sources and remote LDAP servers Select to enable restricting automatically discovered domain controllers to already configured domain controllers only. See Windows event log sources. Enable Windows Active Directory workstation IP verification Select to enable workstation IP verification with Windows Active Directory.
If enabled, select Enable IP change detection via DNS lookup to detect IP changes via DNS lookup.
Disable NTLMv1 in client authentication to Windows AD server Optionally, disable NTLMv1, as NTLMv2 is supported. Disable SMB1 in client connection to Windows AD server
Optionally, disable SMB1.
- In the User Group Membership section, configure the following settings:
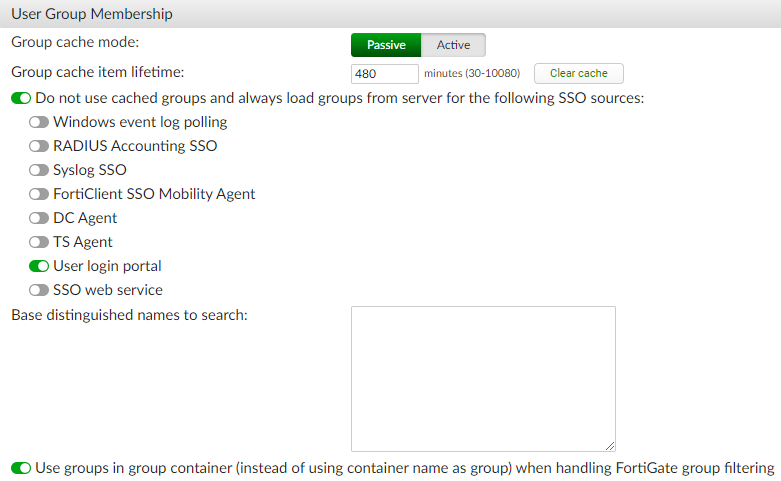
- Select OK to apply the settings.
Configuring FortiGate units for FSSO
Each FortiGate unit that will use FortiAuthenticator to provide Single Sign-On authentication must be configured to use FortiAuthenticator as an SSO server.
To configure SSO authentication on the FortiGate unit:
- On the FortiGate unit, go to Security Fabric > External Connectors and select Create New.
- Select FSSO Agent on Windows AD.
- Enter a name for FortiAuthenticator in the Name field.
- In the Primary FSSO agent field, enter the IP address of FortiAuthenticator.
- In the Password field, enter the secret key that you defined for FortiAuthenticator. See Enable authentication.
- Select OK.
In a few minutes, the FortiGate unit receives a list of user groups from FortiAuthenticator. When you open the server, you can see the list of groups. The groups can be used in identity-based security policies.

