Restricting VPN access to rogue/non-compliant devices with Security Fabric
The following guide provides instructions on configuring the Security Fabric to restrict VPN access to rogue/non-compliant devices using EMS and FortiOS 6.2.3. You can configure this feature with IPsec and SSL VPN. Configuring this feature consists of the following steps:
- Configure a custom hostname and compliance verification rules on EMS.
- Configure the EMS connector in FortiOS.
- Configuring VPN settings:
- Verify the configuration in FortiClient:
This configuration only supports VPN with FortiOS local users. For Active Directory FSSO support, you must use EMS 6.4 and FOS 6.4. See the FortiClient EMS 6.4.3 Administration Guide.
Configuring a custom hostname and compliance verification rules on EMS
To configure a custom hostname and compliance verification rules on EMS:
- In EMS, go to System Settings > Server. In the Custom hostname field, enter a custom hostname.
- Create an administrator as Creating a new administrator user account describes. Enable Restrict Login to Trusted Hosts, and in the Trusted Hosts field, enter the FortiGate/trusted host.
- Create compliance verification rules as Adding a compliance verification rule set describes:
- Create a rule that allows endpoints to access resources. This example creates a rule that applies the AV-Running tag to endpoints that have antivirus software installed and running. You will use the AV-Running in FortiOS dynamic policies at a later step.

- Create a rule that blocks endpoints from accessing resources. This example creates a rule that applies the RED-Alert tag to endpoints that have the risk.txt file present.

- Create a rule that allows endpoints to access resources. This example creates a rule that applies the AV-Running tag to endpoints that have antivirus software installed and running. You will use the AV-Running in FortiOS dynamic policies at a later step.
Configuring the FortiOS-EMS connector
To configure the FortiOS-EMS connector:
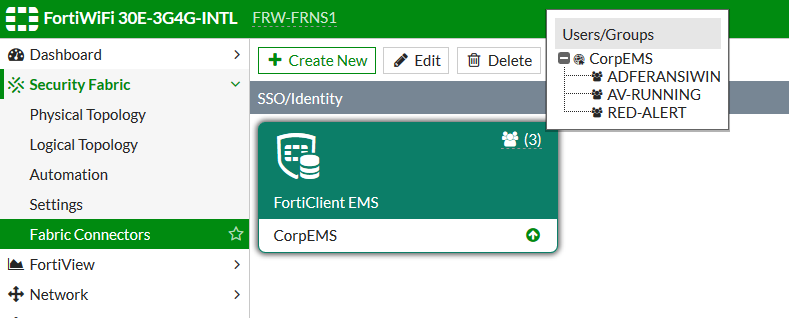
- In FortiOS, go to Security Fabric > Settings. Enable FortiClient Endpoint Management System (EMS), and enter the credentials for the administrator that you created in To configure a custom hostname and compliance verification rules on EMS:. Click Save.
- Go to Security Fabric > Fabric Connectors. Edit the newly created FortiClient EMS connector.
- From the Trusted SSL certificate field, select the desired certificate.
- Click Apply & Refresh, then OK.
- Ensure that the tags that you configured in To configure a custom hostname and compliance verification rules on EMS: are available for the EMS connector.
Configuring VPN settings
To configure FortiOS IPsec VPN settings:
- In FortiOS, go to VPN > IPsec Tunnels.
- Click Create New > IPsec Tunnel.
- On the VPN Setup tab, for Template type, select Remote Access.
- For Remote device type, select Client-based, then FortiClient. Click Next.
- On the Authentication tab, for Authentication method, select Pre-shared Key. Configure the desired preshared key (PSK).
- Configure other fields as desired, then create the tunnel.
- Configure policies:
- Go to Policy & Objects > IP4 Policy.
- Select the VPN IPS policy. Right-click, then select Copy.
- Right-click, then select Paste > Above. Repeat to paste two copies of the policy.
- Edit the top pasted policy to allow endpoint and EMS connection:
- For Destination, select the EMS destination.
- For Service, set to EMS port 8013.
- Set the Action to ACCEPT.
- Enable, then save the policy.

- Edit the second pasted policy to restrict access to high-risk managed endpoints:
- In the Source field, select the tag that you configured to apply to non-compliant endpoints in To configure a custom hostname and compliance verification rules on EMS:.
- Set the Action to DENY.
- Enable, then save the policy.

- Configure the third policy to permit only compliant endpoints to access resources:
- In Source, select the tag that you configured to apply to compliant endpoints in To configure a custom hostname and compliance verification rules on EMS:.
- Set the Action to ALLOW.
- Enable, then save the policy.

- Ensure that the policies are in the correct sequence and enabled.

To configure FortiOS SSL VPN settings:
- In FortiOS, go to VPN > SSL-VPN Settings.
- Configure the Listen on Port and HTTPS port fields as desired.
- Under Authentication/Portal Mapping, select All Other Users/Groups, then select the portal from the Portal dropdown list.
- Click the Apply button.
-
Configure policies:
- FortiOS displays a message that no SSL VPN policies exist. Select to create a new SSL VPN policy using the newly configured settings:
- From the Outgoing Interface dropdown list, select Internal.
- For Source, select the desired users.
- For Destination, select the EMS server.
- Under Service, create a custom service with destination port 8013.
- Enable, then save the policy.

- Select the SSL VPN policy. Right-click, then select Copy.
- Right-click, then select Paste > Below. Repeat to paste two copies of the policy.
- Configure the policies:
- Edit the top pasted policy:
- For Source, select the tag that you configured to apply to non-compliant endpoints in To configure a custom hostname and compliance verification rules on EMS:.
- For Destination, select all.
- For Service, select ALL.
- Set the Action to DENY.
- Enable, then save the policy.

- Edit the second pasted policy:
- In the Source field, select the tag that you configured to apply to compliant endpoints in To configure a custom hostname and compliance verification rules on EMS:.
- For Destination, select all.
- For Service, select ALL.
- Set the Action to ACCEPT.
- Enable, then save the policy.

- Edit the top pasted policy:
- FortiOS displays a message that no SSL VPN policies exist. Select to create a new SSL VPN policy using the newly configured settings:
- Ensure that the policies are sequenced and enabled.

Verifying the configuration in FortiClient
To verify the configuration for IPsec VPN on FortiClient:
- Install FortiClient on an endpoint and ensure that it is connected to EMS.
- Configure and connect to an IPsec VPN tunnel.
- Ensure that EMS and FortiOS apply the correct tags and policies for a compliant endpoint:
- On the user details page, ensure that EMS has applied the appropriate tag. In this example, the AV-Running tag should be applied.

- Ping a device on the network to ensure that it can be reached.
- On the user details page, ensure that EMS has applied the appropriate tag. In this example, the AV-Running tag should be applied.
- Ensure that EMS and FortiOS apply the correct tags and policies for a non-compliant endpoint:
- Change the endpoint condition so that it becomes non-compliant. In this example, that would be creating the risk.txt file on the endpoint. After a few minutes, the ping becomes denied.
- Go to the user details page to ensure that the appropriate tag has been applied. Both tags, in this example RED-Alert and AV-Running, should be applied.

- Ensure that EMS and FortiOS apply the correct tags and policies for a rogue endpoint:
- Delete the risk.txt file, and stop AV services.
- Ensure that the user details page does not display any tags. The endpoint should lose network access.

To verify the configuration for SSL VPN on FortiClient:
- Install FortiClient on an endpoint.
- Configure and connect to an SSL VPN tunnel.
- Ensure that EMS and FortiOS apply the correct tags and policies for a rogue endpoint:
- Ensure that AV services are not running.
- On the user details, ensure that EMS has applied no tags.

- Ping the EMS server. The endpoint should be unable to access internal resources.
- In FortiOS, go to Monitor > Firewall User Monitor. Ensure that there is no tag attribute for the user/device.

- Ensure that EMS and FortiOS apply the correct tags and policies for a compliant endpoint:
- Ensure that AV services are running.
- Go to the user details page to ensure that the appropriate tag has been applied. In this example, only AV-Running should be applied.

- Ping the EMS server again. The endpoint should be able to access internal resources.
- Ensure that EMS and FortiOS apply the correct tags and policies for a non-compliant endpoint:
- Change the endpoint condition so that it becomes non-compliant. In this example, that would be creating the risk.txt file on the endpoint. After a few minutes, the ping becomes denied.
- Go to the user details page to ensure that the appropriate tag has been applied. Both tags, in this example RED-Alert and AV-Running, should be applied.


