Configuring Microsoft Intune integration
Intune integration allows FortiClient (iOS) endpoints to connect to EMS.
To configure integration between Microsoft Intune and FortiClient (iOS):
- In Microsoft Intune, go to Users > All users and select New user. Configure the user as desired. Click Create.
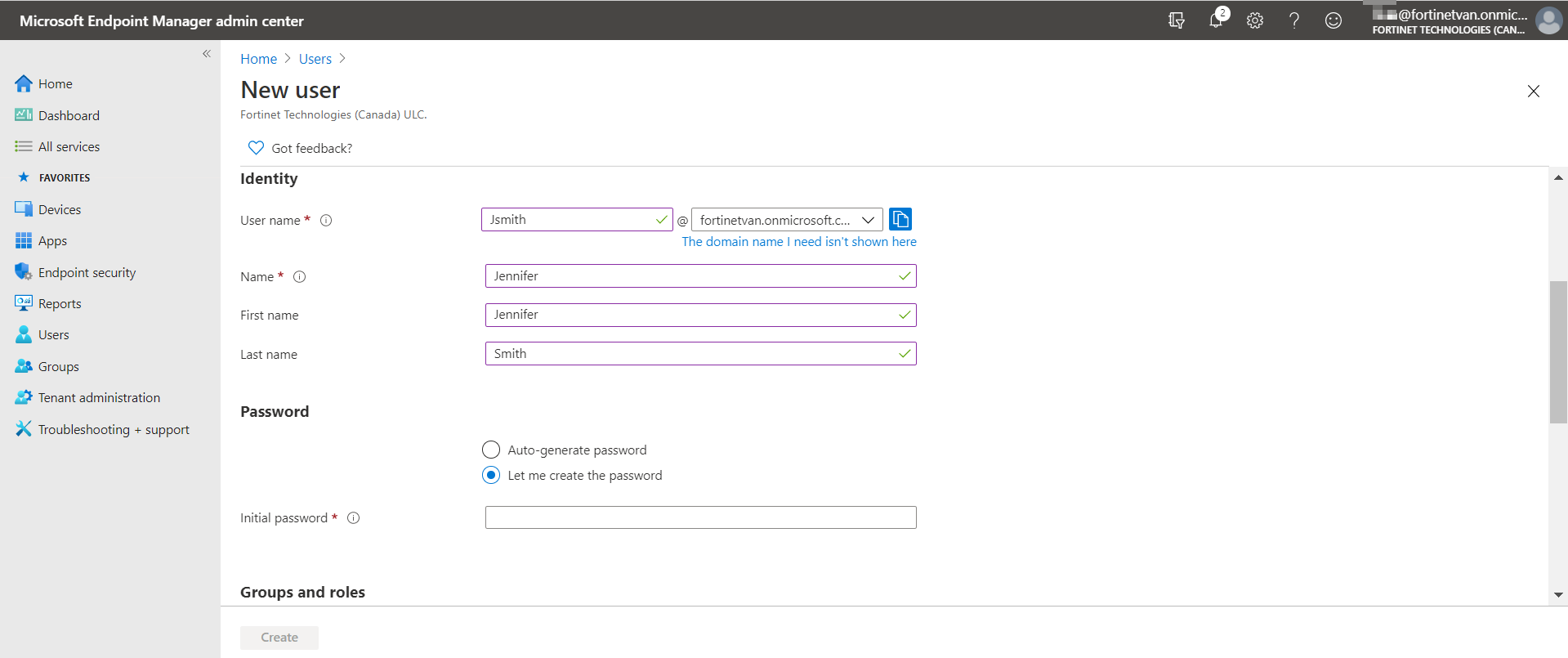
- Select the user that you created, then go to license.
- Under Select licenses, select Enterprise Mobility + Security E3. Under Enterprise Mobility + Security E3, enable Microsoft Intune. Enrolling devices requires the license. Click Save.

- Go to Groups. Select New Group, then configure the group as desired. Click Create.
- Go to the group that you created, then go to Members. Click Add members to add desired members to the group, including the user that you created in step 1.
- Enroll the device to the user:
- Download the Intune Company Portal app from the App Store.
- Enter the user credentials that you configured in step 1 to download and install the profile.

- In Intune, go to Apps > All apps. Click Add, then search for and select FortiClient (iOS) from the public App Store. On the Assignments tab, click Add group, then select the group that you created in step 4.
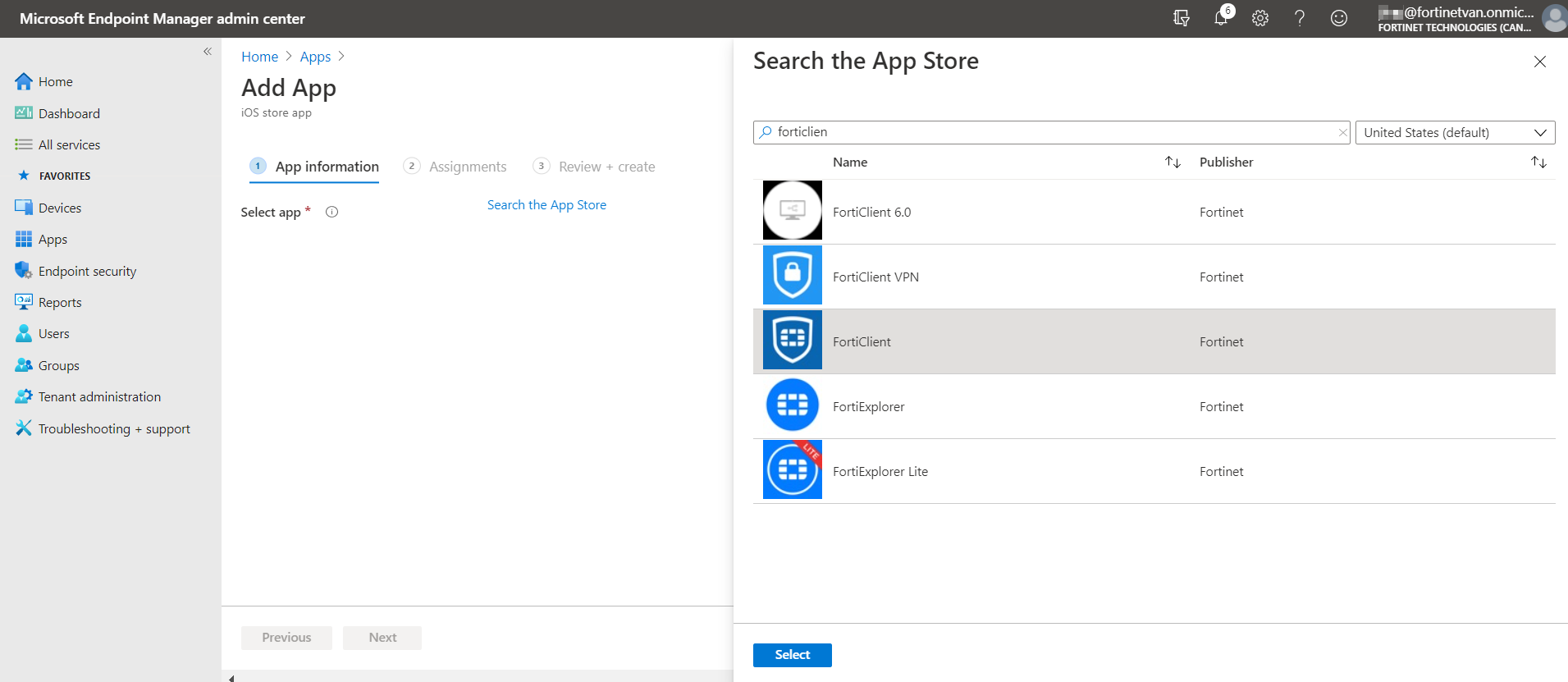
- Create an app configuration policy:
- Go to Apps > App configuration policies, then click Create app configuration policy.
- On the Basics tab, from the Platform dropdown list, select iOS/iPadOS. Click Next.
- On the Settings tab, configure the following:
- From the Configuration settings format dropdown list, select Use configuration designer.
- Under Configuration key, enter keys to allow FortiClient (iOS) to register to and send information to EMS. Intune supports the following keys:
Key
Description
udid
iOS device UDID.
group_tag
This value is used as a group tag for configuration in EMS. EMS uses this value as an installer ID to assign the endpoint to a group. See Group assignment rule types.
cloud_invite_code
FortiClient (iOS) uses this value to connect to FortiClient Cloud. Enter the invite code that you received from FortiClient Cloud.
user_name
FortiClient (iOS) username.
ems_server
EMS IP address or hostname.
ems_port
Port number for FortiClient (iOS) to connect Telemetry to EMS. By default, this is 8013.
ems_key
Telemetry connection key. The EMS administrator may require FortiClient (iOS) to provide this key during connection.

- When FortiClient (iOS) starts on the device, it automatically connects to on-premise EMS or FortiClient Cloud, depending on the configuration.
When the FortiGate is configured to use SSL deep inspection, then the certificate authority (CA) certificate is automatically installed on desktop FortiClient endpoints by FortiClient EMS using an Endpoint Profile. See CA Certificates.
However, for mobile endpoints such as Apple devices running FortiClient iOS, then enterprise mobility management software must be used to install such CA certificates. You can find details on deploying a trusted root certificate such as the CA certificate configured on the FortiGate for SSL deep inspection in Trusted root certificate profiles for Microsoft Intune.

