Add AWS Organization
AWS Organization is added through the master account when adding to FortiCNP. Once the master account is added, the sub accounts can be selected to be added to FortiCNP.
There are 3 types of permissions to be granted to FortiCNP to add the AWS organization and the accounts under it. For more details, see AWS Permission and Resource Requirements
Steps to add AWS organization
- From the FortiCNP navigation pane, go to ADMIN > Cloud Accounts, click +Add New.
- Select AWS as the cloud platform, and Add AWS Organization as the method, then click Add New Cloud Account.
- Enter the master AWS Account ID of the AWS organization and give a name for the account, select optional permissions to be granted to FortiCNP as needed.
- In CloudTrail section, select "Yes" to allow FortiCNP to create a CloudTrail for the account, or "No" if you already created one.
- Click Next Step to continue to the next page.
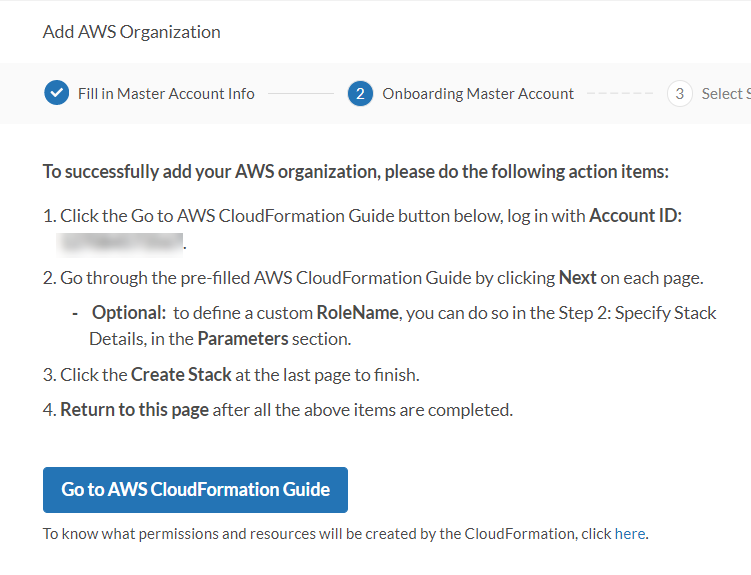
- Click Go to AWS CloudFormation Guide to be re-directed to AWS CloudFormation guide to create stack and cloutrail.
- A new page will pop up with AWS CloudFormation Guide, click Next to go to the next page.
- In Specify stack details page > Parameters section, enter a custom RoleName or use the default RoleName.
- Continue by clicking Next at the bottom of each page until the last page. Click Create Stack to finish.
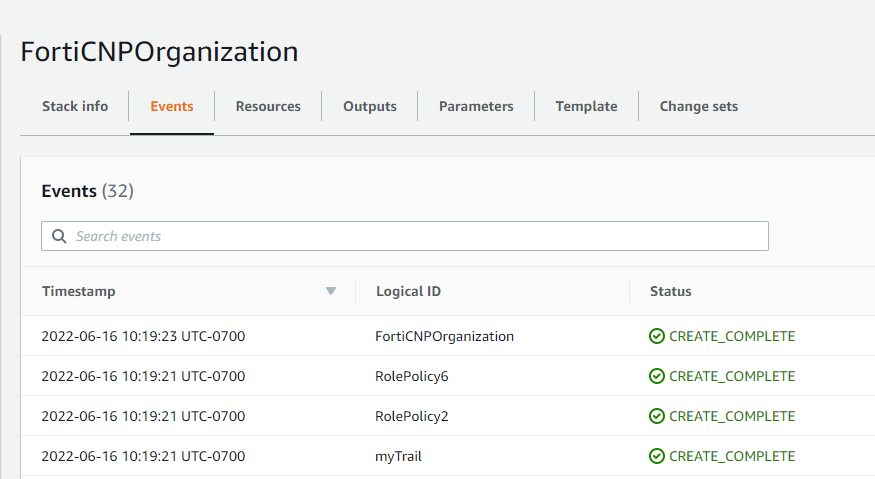
- Refresh the stack creation process of FortiCNPOrganization until the status becomes "CREATE_COMPLETE".
- Go back to FortiCNP add AWS organization page:
- If you used a custom RoleName, select "Yes I defined a custom RoleName.", and enter the custom RoleName.
- If not, select "No, I did NOT define a custom RoleName."

- Click Next Step. FortiCNP will check master account's configuration.
- The check status will show details on the stack configuration, then click Next Step
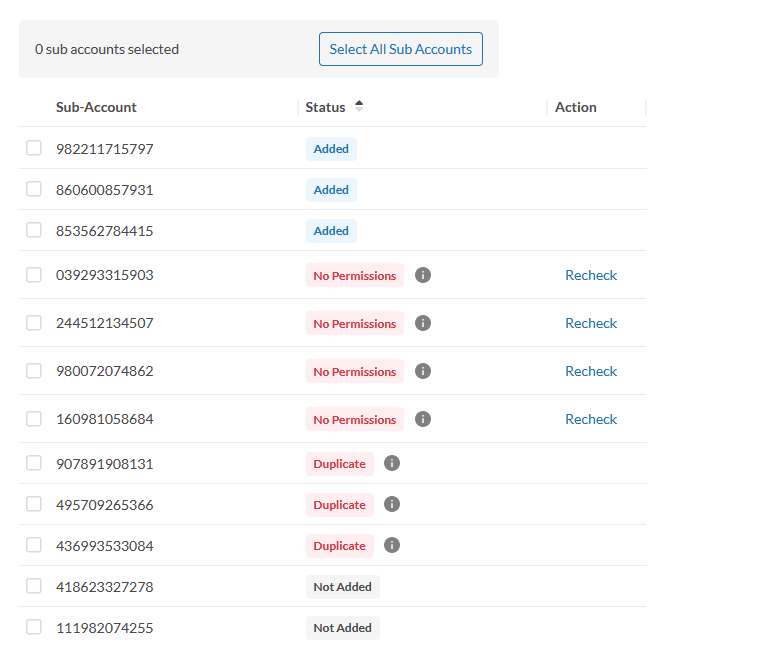
- Select the sub-accounts to be added to the AWS Organization, and click Add AWS Organization. See Add AWS Organization Sub Account Status for more details.
- There are multiple steps here to configure Security Hub Integrations:
- Enable Amazon GuardDuty, Amazon Inspector, and AWS Security Hub in the same region as the master account, and the sub account(s) that you want to receive security findings. The purpose is so that the findings can be shared between sub accounts and the designated account configured for eventbus. For region selection, please use us-west-2 for Global (US) users, and eu-west-1 for EU users. (recommended)
- Choose one account to be the aggregation account where it will receive security findings from other accounts. Follow the guide in AWS Security Hub and EventBridge Configuration to configure only that account.
- Select the aggregation account configured in step b and the aggregation region from step a in the Security Hub Integration page and click Next Step.
For example, if one account have Amazon GuardDuty, Amazon Inspector, and AWS Security Hub enabled in US-West (Oregon), other accounts should do the same.


The AWS Events Bus and Events Rule are configured through the AWS CloudFormation guide, so that the Security Hub can send security findings to the AWS Events bus under the FortiCNP's AWS EventBridge - Click Go To AWS CloudFormation Guide, click Next on each page to create StackSet for AWS security hub integration.
- Go back to FortiCNP add account page, and click Next Step to finish.