Blocking Windows XP traffic
This recipe demonstrates how you can use the Application Control security profile to block web traffic from PCs running Windows NT 5 operating systems, including Windows XP and Windows Server 2003 (includes Windows virtual machines).
When a computer’s operating system lacks vendor support, it becomes a threat to the network because newly discovered exploits will not be patched. Using the FortiGate application control feature, you can restrict these computers from accessing external resources. This recipe will only block web traffic from computers running the designated operating systems. If you wish to block these computers from being on the network entirely, further action will be necessary. However, the logs generated by this recipe can be used to identify the computers you wish to block.

1. Enabling Application Control
Go to System > Feature Select. Under Security Features, enable Application Control.

2. Creating a custom application signature
Go to Security Profiles > Application Control and select View Application Signatures in the upper right-hand corner. Create a new signature with the syntax presented here.
You can copy and paste this text into the Signature field.

F-SBID(--attack_id 8151; --vuln_id 8151; --name "Windows.NT.5.Web.Surfing"; --default_action drop_session; --service HTTP; --protocol tcp; --app_cat 25; --flow from_client; --pattern !"FCT"; --pattern "Windows NT 5.1"; --no_case; --context header; --weight 40; )
The signature will appear at the top of the application list in the Web.Client category.

3. Adding the signature to the default Application Control profile
Go to Security Profiles > Application Control and edit the default policy.
Under Application Overrides, select Add Signatures.

The new signature should appear at the top of the list. If it does not, search for the signature’s name (in the example, block-windows-nt5).
Select the signature, then click on Use Selected Signatures at the bottom of the page.

4. Adding the default profile to a security policy
Go to Policy & Objects > IPv4 Policy and edit the policy that allows connections from the internal network to the Internet.
Under Security Profiles, enable Application Control and use the default profile.

5. Results
When a PC running one of the affected operating systems attempts to connect to the Internet using a browser, a replacement message appears. Because Application Control uses flow-based inspection, if you apply an additional security profile to your traffic that is proxy-based, the connection will simply timeout rather than display the replacement message. Howerver, Application Control will still function.
PCs running other operating systems, including later versions of Windows, are not affected.
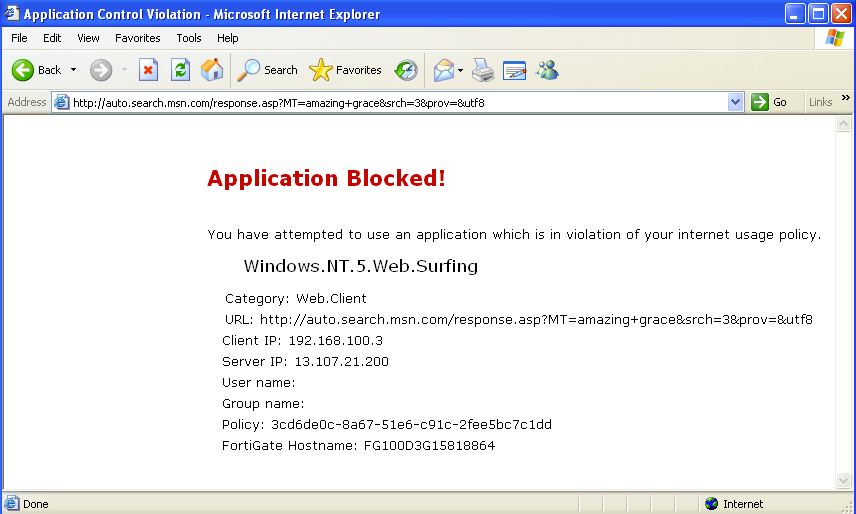
Go to Log & Report > Forward Traffic. Filter the results to show denied traffic.
You will see that the application control signature, Windows.NT.5.Web.Surfing, appears in the Application column and was used to block traffic from PCs running Windows XP (device writer-0735721d).

For further reading, check out Custom Application & IPS Signatures in the FortiOS 5.4 Handbook.

