IPsec VPN two-factor authentication with FortiToken-200
In this recipe, you will configure two-factor authentication using a FortiToken-200 for IPsec VPN connections.
This recipe assumes that you have already created a user (elainemarley) and a user group (FTK-users). You will add a FortiToken-200 to the FortiGate, assign the token to the user, and add the user to the group. You will then use the Wizard to create an IPsec VPN tunnel that allows FortiToken-200 users to securely access an internal network and the Internet. You will test the setup by having the user access the VPN from a remote device, using FortiClient.
1. Adding the FortiToken
Go to User & Device > FortiTokens and create a new FortiToken.
Set Type to Hard Token and enter the FortiToken's Serial Number into the field provided. Note that the serial number, located on the back of the FortiToken device, is case sensitive and must not be in use elsewhere.

2. Editing the user and assigning the FortiToken
Go to User & Device > User Definition and edit elainemarley.
Select Enable Two-factor Authentication and select the token.
Select Add this user to groups and add the user to FTK-users.

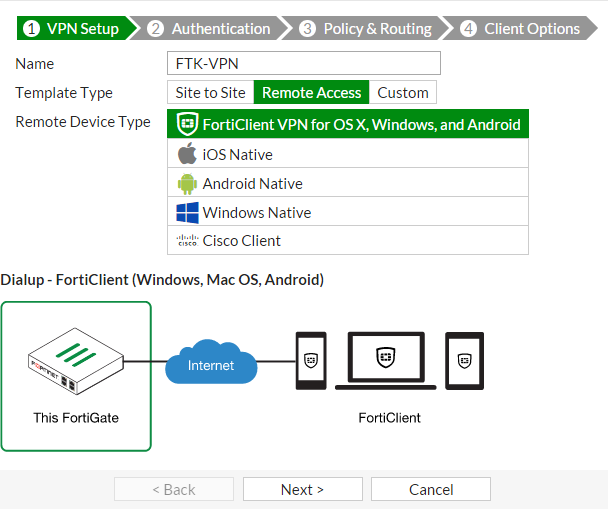
3. Configuring the IPsec VPN using the IPsec VPN Wizard
Go to VPN > IPSec Wizard and create a new IPsec VPN tunnel.
Name the VPN connection (in the example, FTK–VPN).
Select the Remote Access template, set Remote Device Type to FortiClient VPN for OS X, Windows, and Android, and select Next.
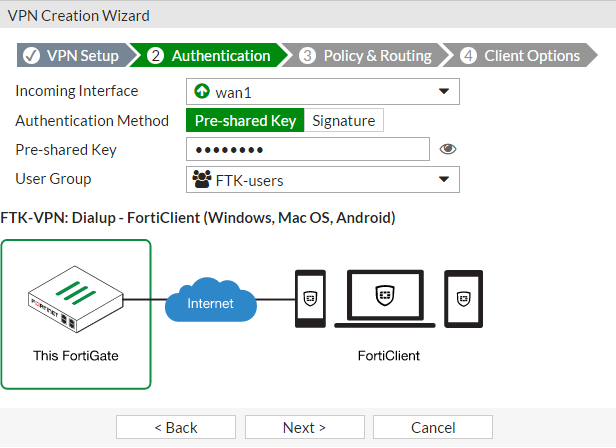
Set the Incoming Interface to the Internet-facing interface (wan1).
Set Authentication Method to Pre-shared Key and enter a pre-shared key.
Select the user group created earlier (FTK-users) and select Next.
Set Local Interface to the internal interface and set Local Address to all.
Enter an IP address range for VPN users in the Client Address Range field. Make sure no other interfaces on the FortiGate are using the same address range. A Subnet Maskshould already be set.
Select Next.

Configure additional Client Options and select Create.

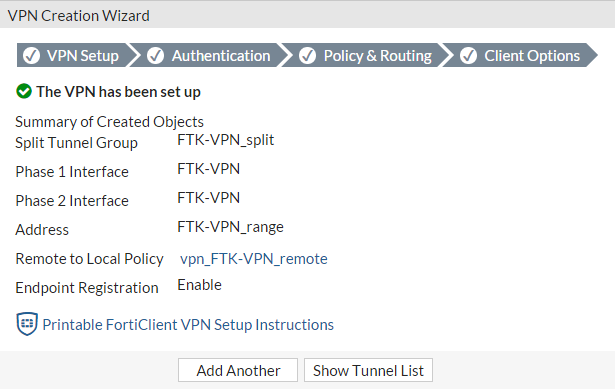
A summary page will appear showing the VPN's configuration.
4. Connecting to the IPsec VPN
On your remote device, open the FortiClient application, go to Remote Access, and add a new connection.
Set VPN Type to IPsec VPN, and enter a Connection Name.
Set Remote Gateway to the IP address of the FortiGate, set Authentication Method to Pre-Shared Key, and enter a Pre-Shared Key.
The key must match the same key entered in the wizard on the FortiGate earlier.
When finished, select Add.

5. Results
Go to Remote Access and attempt to log into the VPN as elainemarley.

You will then be prompted to enter a FortiToken Code. Enter the code and select OK.

The useris now successfully connected to the IPsec VPN FTK-VPN.

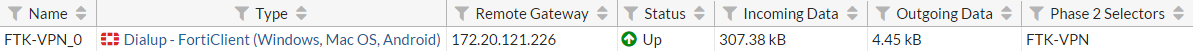
To verify the user's connection, go to FortiView > VPN.

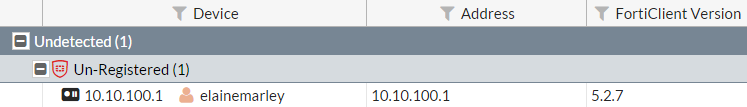
You can also go to Monitor > IPsec Monitor to view the tunnel's status, and Monitor > FortiClient Monitor to view the user and device.