Blocking malicious traffic
This example describes how to use Policy Analyzer MEA to create a policy block that blocks malicious traffic on FortiGates.
When the Policy Analyzer MEA wizard detects malware and applications rated high-risk, you can select the Block Malicious Traffic mode to create a policy block that will block the traffic on the FortiGate. Even though malicious traffic is leaned on a specific port, the policy block generated by Policy Analyzer MEA will block malicious traffic on all FortiGate interfaces.
For example, Policy Analyzer wizard can learn of a high-risk application on source port 1. When you select Block Malicious Traffic mode, Policy Analyzer creates a policy block that blocks high-risk applications for all ports. High-risk applications are not blocked only on the port used to learn traffic.
To block malicious traffic:
- Open Policy Analyzer MEA to access the first step in the wizard.
Policy Analyzer opens, and the first pane of the wizard is displayed. The name of the first pane is 1. Select One device.
- On the 1. Select One device pane, select a FortiGate.

Option
Description
Device Select a managed FortiGate that uses a Security Policy with Learn Mode enabled. Policy package After selecting a FortiGate, the policy package for the selected FortiGate is displayed. FortiAnalyzer status Displays whether logging from FortiGate to FortiAnalyzer is enabled. FortiAnalyzer IP After selecting a FortiGate, the IP address for the FortiAnalyzer that is receiving logs from the selected FortiGate is displayed. - On the 1. Select One device pane, complete the following options to validate credentials for FortiAnalyzer and select a date range of logs to analyze, and then click Next.
Option
Description
FortiAnalyzer username Type the username for the administrator account for FortiAnalyzer.
The administrator account must have JSON API set to a minimum of Read. See also Configuring FortiAnalyzer.
FortiAnalyzer password Type the password for the administrator account. Validate Credentials After typing in the FortiAnalyzer username and password, click Validate Credentials to authenticate access to the logs on FortiAnalyzer. FortiAnalyzer ADOM Available after you validate the username and password for FortiAnalyzer.
Select the ADOM on FortiAnalyzer that contains the logs for the selected FortiGate.
Log date range
Available after you validate the username and password for FortiAnalyzer.
Click the calendar icon to select a date range of logs for analysis.
Policy Analyzer MEA needs to access online logs indexed in the FortiAnalyzer SQL database. Policy Analyzer MEA cannot analyze archived logs. For more information, see the FortiAnalyzer 7.0.2 Administration Guide.
The 2. Select Learning-Mode Policies pane is displayed.
- On the 2. Select Learning-Mode Policies pane, select a Security Policy with Learn Mode enabled, and click Next.
Policies are available for selection when they have Learn Mode enabled and have hit counts.

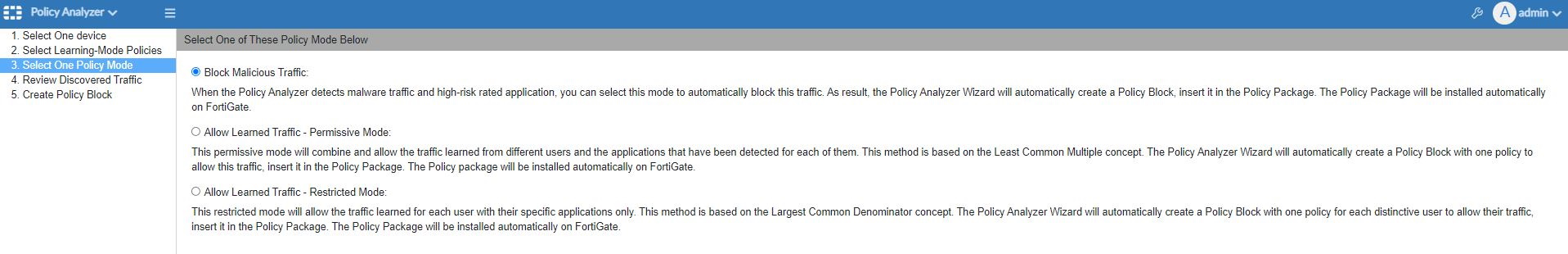
The 3. Select One Policy Mode pane is displayed.
- On the 3. Select One Policy Mode pane, select Block Malicious Traffic, and click Next.
The Review Discovered Traffic pane is displayed.
- On the Review Discovered Traffic pane, review discovered traffic, and click Next.
In the following example, the Top Applications tab shows the high-risk applications in the logs. Click the Top Users, Top Web Categories, and Top Threats tabs to review traffic on those tabs. In the Column Filter box, type a string, and press Enter to filter results.

The Create Policy Block pane is displayed.
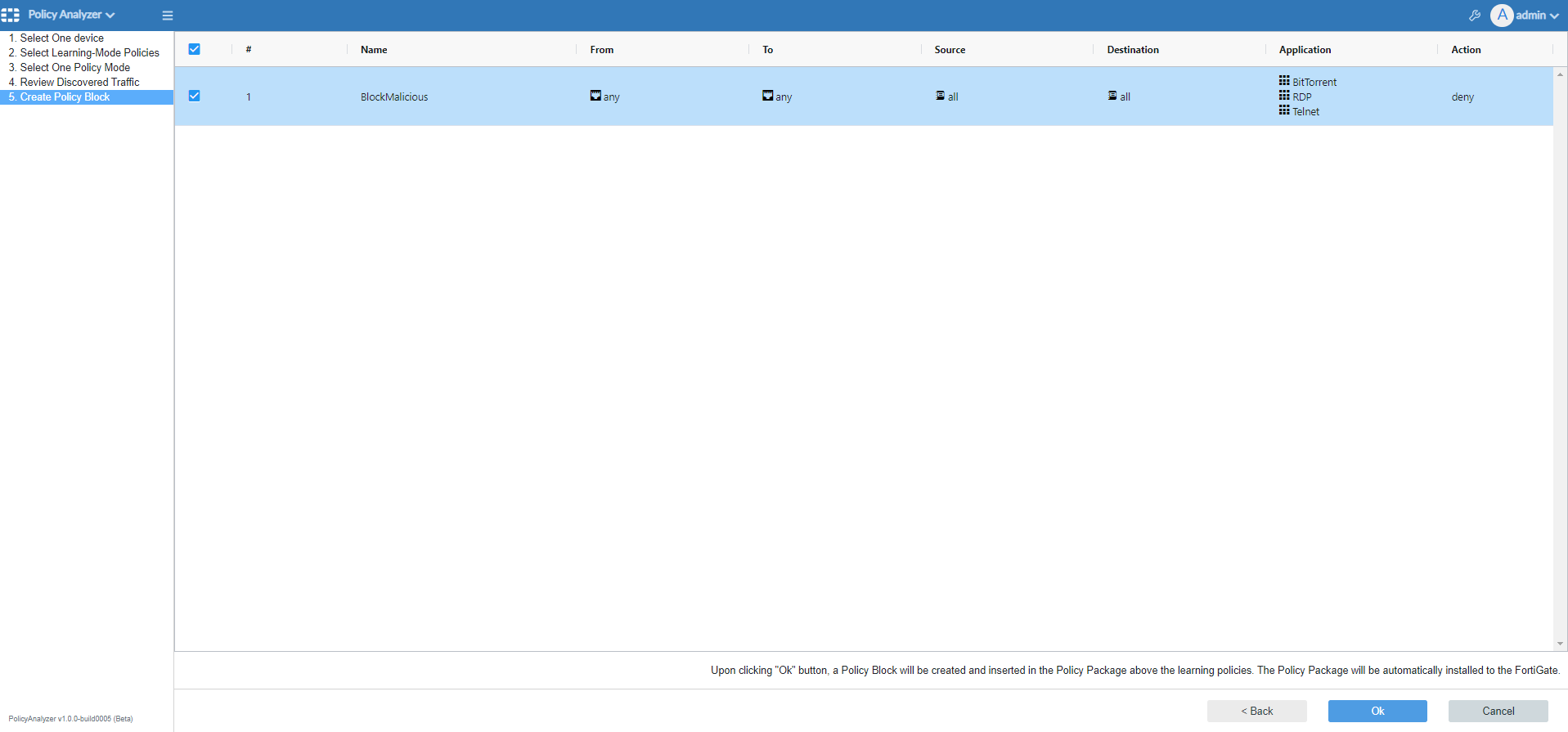
- On the Create Policy Block pane, click OK.
A confirmation dialog box is displayed.

- In the confirmation dialog box, click OK.
Policy Analyzer MEA automatically creates the policy block, inserts the policy block in to the policy package, and the policy package is installed to the FortiGate.

