Deploying auto scaling on AWS
You can deploy FortiWeb-VM to support auto scaling on AWS. This requires a manual deployment incorporating CFT.
Multiple FortiWeb-VM instances can form an auto scaling group (ASG) to provide highly efficient clustering at times of high workloads. FortiWeb-VM instances can be scaled out automatically according to predefined workload levels. When a spike in traffic occurs, the Lambda script is invoked to scale out the ASG by automatically adding FortiWeb-VM instances. Auto scaling is achieved by using FortiWeb-native High Availability (HA) features such as manager -mode, which synchronizes Operating System (OS) configurations across multiple FortiWeb-VM instances at the time of scale-out events.
We support two use cases:
- On-demand only case, in which the autoscaling group only consists of on-demand instances.
- Hybrid case, in which there are a fixed amount of BYOL instances and an autoscaling group that consists of on-demand instances. BYOL instances in the Hybrid case must be FortiWeb 6.3.7 and later versions.
In both cases, you only need to configure on the primary FortiWeb, and the secondary FortiWeb-VMs will automatically synchronize configuration.
The firmware upgrade or downgrade function is not available in hybrid case. If you want to use a different version of FortiWeb-VM, you need to create a new CloudFormation stack.
Before you deploy FortiWeb-VM auto scaling on AWS, it is recommended that you become familiar with the following AWS services. If you are new to AWS, see Getting Started.
- Amazon Elastic Cloud Compute (Amazon EC2)
- Amazon EC2 Auto Scaling
- Amazon VPC
- AWS CloudFormation
- AWS Lambda
- Amazon DynamoDB
- Amazon API Gateway
- Amazon CloudWatch
- Amazon S3
It is expected that DevOps engineers or advanced system administrators who are familiar with the area will deploy auto scaling.
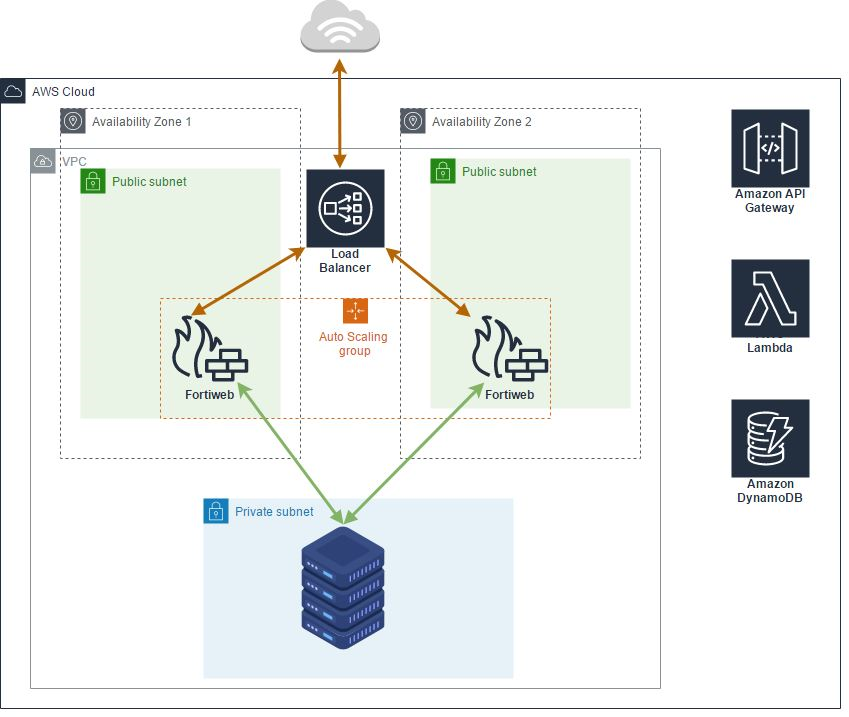
FortiWeb-VM Autoscale for AWS uses AWS CFT to set up the following:
- A highly available architecture that spans two Availability Zones (AZs)
-
An Amazon Virtual Private Cloud (VPC) configured with public and private subnets according to AWS best practices, to provide you with your own virtual network on AWS
- An Internet gateway to allow access to the Internet
- In the public subnets, a FortiWeb-VM host in an ASG complements AWS security groups to provide web filtering and threat detection to protect your services from cyber attacks
- An externally facing network load balancer is created as part of the deployment process.
- An elastic IP to access the master FortiWeb-VM. When the master role is transferred from one instance to another, the EIP will be associated with the new instance at the same time.
- Amazon API Gateway, which acts as a front door by providing a callback URL for the FortiWeb-VM ASG. FortiWeb-VMs use API Gateway to send API calls and to process FortiWeb manager-mode tasks to synchronize configuration across multiple FortiWeb-VM instances at the time of the auto scaling scale-out event. This is currently only for internal use. There is no public access available.
- AWS Lambda, which allows you to run certain scripts and code without provisioning servers. Fortinet provides Lambda scripts for running auto scaling. Lambda functions are used to handle auto scaling, failover management, CFT deployment, and configuration for other related components.
- An Amazon DynamoDB database that uses Fortinet-provided scripts to store information about auto scaling condition states.

