About the connector
Fortinet FortiNDR Cloud is a cloud-native network detection and response solution built for the rapid detection of threat activity, investigation of suspicious behavior, proactive hunting for potential risks, and directing a fast and effective response to active threats.
This document provides information about the Fortinet FortiNDR Cloud connector, which facilitates automated interactions, with Fortinet FortiNDR Cloud using FortiSOAR™ playbooks. Add the Fortinet FortiNDR Cloud connector as a step in FortiSOAR™ playbooks and perform automated operations using Fortinet FortiNDR Cloud.
Use the Data Ingestion Wizard to ingest data into FortiSOAR™ by pulling detections from Fortinet FortiNDR Cloud. Currently, "detections" in Fortinet FortiNDR Cloud are mapped to "alerts" in FortiSOAR™. For more information, see the Data Ingestion Support section.
Version information
Connector Version: 1.0.0
FortiSOAR™ Version Tested on: 7.3.2-2150
Fortinet FortiNDR Cloud Version Tested on: 2023.2.1
Authored By: Fortinet
Certified: Yes
Installing the connector
Use the Content Hub to install the connector. For the detailed procedure to install a connector, click here.
You can also use the yum command as a root user to install the connector:
yum install cyops-connector-fortinet-fortindr-cloud
Prerequisites to configuring the connector
- You must have the API token and Account UUID used to access Fortinet FortiNDR Cloud on which you will perform the automated operations.
- The FortiSOAR™ server should have outbound connectivity to port 443 on Fortinet FortiNDR Cloud.
Minimum Permissions Required
Configuring the connector
For the procedure to configure a connector, click here
Configuration parameters
In FortiSOAR™, on the Connectors page, click the Fortinet FortiNDR Cloud connector row (if you are in the Grid view on the Connectors page) and in the Configurations tab enter the required configuration details:
| Parameter |
Description |
| API Token |
Specify the API Token used to access the FortiNDR Cloud APIs and perform the automated operations. |
| Account UUID |
Specify the UUID of the account used to access FortiNDR Cloud and perform the automated operations. |
| Verify SSL |
Specifies whether the SSL certificate for the server is to be verified or not. |
Actions supported by the connector
The following automated operations can be included in playbooks and you can also use the annotations to access operations from FortiSOAR™:
| Function |
Description |
Annotation and Category |
| Get PCAP Tasks |
Retrieves a list of all the PCAP tasks or specific PCAP tasks from FortiNDR Cloud based on the input parameters you have specified. |
get_pcap_tasks
Investigation |
| Download PCAP Task File |
Downloads a specific PCAP task file generated by the specified task from FortiNDR Coud based on the task UUID, and other input parameters you have specified. |
download_pcap_task_file
Investigation |
| Terminate PCAP Task |
Stops a specific, currently running, PCAP task on FortiNDR Cloud based on the task UUID that you have specified. |
terminate_pcap_task
Investigation |
| Delete PCAP Task |
Permanently removes a specific PCAP task and all its associated files from FortiNDR Cloud based on the task UUID that you have specified. |
delete_pcap_task
Investigation |
| Get Sensors List |
Retrieves a list of all sensors or specific sensors from FortiNDR Cloud based on the input parameters that you have specified. |
get_sensors
Investigation |
| Get Telemetry Events |
Retrieves details for all telemetry events or specific telemetry events from FortiNDR Cloud based on the input parameters you have specified. |
get_telemetry_events
Investigation |
| Get Telemetry Bandwidth |
Retrieves details of telemetry bandwidth from FortiNDR Cloud based on the input parameters you have specified. |
get_telemetry_bandwidth
Investigation |
| Get Telemetry Packetstats |
Retrieves details for telemetry packetstats from FortiNDR Cloud based on the input parameters you have specified. |
get_telemetry_packetstats
Investigation |
| Get Entity Tracking |
Retrieves information about an IP address, MAC address, or Host name from FortiNDR Cloud based on the entity type and value and other input parameters you have specified. |
get_entity_tracking
Investigation |
| Get Entity Summary |
Retrieves summary information about an IP address or domain from FortiNDR Cloud based on the IP address or Domain you have specified. |
get_entity_summary
Investigation |
| Get Passive DNS Details |
Retrieves passive DNS information about an IP address or domain from FortiNDR Cloud based on the IP address or Domain and other input parameters you have specified. |
get_entity_pdns
Investigation |
| Get Detections List |
Retrieves a list of all detections or specific detections from FortiNDR Cloud based on the input parameters you have specified. |
get_detections
Investigation |
| Resolve Detection |
Resolves a specific detection on FortiNDR Cloud based on the detection UUID, resolution, and comment (optional) you have specified. |
resolve_detection
Investigation |
| Get Devices with Detection |
Retrieves a list of all devices with detection or specific devices with detection from FortiNDR Cloud based on the account UUID and other input parameters you have specified. |
get_devices_with_detection
Investigation |
| Get Detection Events |
Retrieves a list of all detection events or specific detection events from FortiNDR Cloud based on the detection UUID and other input parameters you have specified. |
get_detection_events
Investigation |
| Get Detection Rule Indicators |
Retrieves a list of all detection rule indicators or specific detection rule indicators from FortiNDR Cloud based on the rule UUID and other input parameters you have specified. |
get_detection_rule_indicators
Investigation |
| Get Detection Rules List |
Retrieves a list of all the detection rules or specific detection rules from FortiNDR Cloud based on the input parameters you have specified. |
get_detection_rules
Investigation |
| Get Detection Rule Details |
Retrieves information for a specific detection rule from FortiNDR Cloud based on the rule UUID and rule account UUID (optional) you have specified. |
get_detection_rules
Investigation |
| Get Detection Rule Events List |
Retrieves a list of all events for a specific detection rule from FortiNDR Cloud based on the rule UUID and other input parameters you have specified. |
get_detection_rule_events
Investigation |
operation: Get PCAP Tasks
Input parameters
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied, and an unfiltered list (of PCAP tasks) is returned.
| Parameter |
Description |
| Task UUID |
Specify the UUID of the task based on which you want to retrieve PCAP tasks from FortiNDR Cloud.
Note: If you specify the Task UUID, then you do not need to specify any other parameters. |
| Sensor ID |
Specify the sensor ID based on which you want to retrieve PCAP tasks from FortiNDR Cloud |
| Created Start DateTime |
Select the DateTime using which you want to filter the result set to only include only those items that have been created after the specified timestamp. |
| Created End DateTime |
Select the DateTime using which you want to filter the result set to only include only those items that have been created before the specified timestamp. |
| Search Text |
Specify the text based on which you want to search for PCAP tasks from FortiNDR Cloud. In this case, this operation returns only those PCAP tasks that contain the specified string in their descriptions or names. |
| Include Hash Files |
Select this checkbox to only return those PCAP tasks that contain Hash files. By default, this option is selected, i.e. set to 'True'. |
| Page Size |
Specify the maximum count of records that you want this operation to fetch from FortiNDR Cloud. By default, this option is set to 100, and you can set a maximum value of 1000. |
| Page Number |
Specify the page from which you want this operation to return results based on the page size. By default, this option is set as '1'. For example, if you set this as '2' and retain the page size as 100, then the operation will return 100 results from the 2nd page. |
Output
The output contains the following populated JSON schema:
Output schema when the "Task UUID" is not specified:
{
"pcaptasks": [
{
"task_uuid": "",
"description": "",
"name": "",
"sensor_ids": [],
"account_code": "",
"bpf": "",
"created_uuid": "",
"updated_uuid": "",
"created_email": "",
"updated_email": "",
"created": "",
"updated": "",
"requested_start_time": "",
"requested_end_time": "",
"actual_start_time": "",
"actual_end_time": "",
"status": "",
"files": [],
"has_files": ""
}
],
"result_count": ""
}
Output schema when the "Task UUID" is not specified:
{
"pcap_task": {
"task_uuid": "",
"description": "",
"name": "",
"sensor_ids": [],
"account_code": "",
"bpf": "",
"created_uuid": "",
"updated_uuid": "",
"created_email": "",
"updated_email": "",
"created": "",
"updated": "",
"requested_start_time": "",
"requested_end_time": "",
"actual_start_time": "",
"actual_end_time": "",
"status": "",
"files": [],
"has_files": ""
}
}
operation: Download PCAP Task File
Input parameters
| Parameter |
Description |
| Task UUID |
Specify the UUID of the task whose associated PCAP task file you want to download from FortiNDR Cloud. |
| File Name |
(Optional) Specify the name of the file that you want to assign to the PCAP task file downloaded from FortiNDR Cloud. |
Output
The output contains a non-dictionary value.
operation: Terminate PCAP Task
Input parameters
| Parameter |
Description |
| Task UUID |
Specify the UUID of the currently running PCAP task that you want to stop on FortiNDR Cloud. |
Output
The output contains the following populated JSON schema:
{
"message": ""
}
operation: Delete PCAP Task
Input parameters
| Parameter |
Description |
| Task UUID |
Specify the UUID of the PCAP task that you want to remove from FortiNDR Cloud. This operation will delete the specific PCAP task and all its associated files from FortiNDR Cloud. |
Output
The output contains the following populated JSON schema:
{
"message": ""
}
operation: Get Sensors List
Input parameters
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied, and an unfiltered list (of sensors) is returned.
| Parameter |
Description |
| Sensor ID |
Specify the UUID of the sensor based on which you want to retrieve the specific sensor from FortiNDR Cloud. |
| Account Code |
Specify the code of the account based on which you want to retrieve sensors from FortiNDR Cloud. |
| Include |
Choose additional parameters (metadata) that you want to include in the results. You can choose one, more than one, or all of the following values: Status or Interfaces. |
Output
The output contains the following populated JSON schema:
{
"result_count": "",
"sensors": [
{
"created": "",
"updated": "",
"disabled": "",
"sensor_id": "",
"account_code": "",
"location": {
"latitude": "",
"longitude": ""
},
"subdivision": "",
"city": "",
"country": "",
"pcap_enabled": "",
"tags": [],
"serial_number": "",
"status": "",
"interfaces": "",
"admin": ""
}
]
}
operation: Get Telemetry Events
Input parameters
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied, and an unfiltered list (of telemetry events) is returned.
| Parameter |
Description |
| Sensor ID |
Specify the ID of the sensor based on which you want to retrieve telemetry events from FortiNDR Cloud. |
| Account Code |
Specify the code of the account based on which you want to retrieve telemetry events from FortiNDR Cloud. |
| Interval |
Choose the interval based on which you want to retrieve telemetry events from FortiNDR Cloud. You can choose between Hour (default) or Day. |
| Start DateTime |
Select the DateTime using which you want to filter the result set to only include only those items that have been created after the specified timestamp.
Note: The default is 1 day ago if you have selected the interval as Hour or 30 days ago if you have selected the interval as Day. |
| End DateTime |
Select the DateTme using which you want to filter the result set to only include only those items that have been created before the specified timestamp. |
| Event Type |
Select the type of telemetry events you want to retrieve from FortiNDR Cloud. You can choose from values such as Flow, DNS, HTTP, SSL, X509, etc. |
| Group By |
Select the criteria that you want to use to group telemetry events retrieved from FortiNDR Cloud. You can choose between Sensor ID or Event Type. |
Output
The output contains the following populated JSON schema:
{
"result_count": "",
"columns": [],
"data": []
}
operation: Get Telemetry Bandwidth
Input parameters
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied.
| Parameter |
Description |
| Account Code |
Specify the code of the account based on which you want to retrieve network telemetry from FortiNDR Cloud. |
| Start DateTime |
Select the DateTime using which you want to filter the result set to only include only those items that have been created after the specified timestamp. |
| End DateTime |
Select the DateTime using which you want to filter the result set to only include only those items that have been created before the specified timestamp. |
| Interval |
Choose the interval based on which you want to retrieve network telemetry from FortiNDR Cloud. You can choose between Day or Month to Day. |
| Latest Month |
Specify this parameter if you want to filter out the network usage telemetry for all days, except the latest day and month_to_date for each month. |
| Sort Order |
Select the sorting order of the result. You can choose between Ascending or Descending (default). |
| Limit |
Specify the maximum number of results, per page, that this operation should return. By default, this option is set as 1000. |
| Offset |
Index of the first item to be returned by this operation. This parameter is useful for pagination and for getting a subset of items. By default, this is set as 0 |
Output
The output contains the following populated JSON schema:
{
"result_count": "",
"total_count": "",
"network_usage": [
{
"account_code": "",
"percentile_bps": "",
"percentile": "",
"interval": "",
"timestamp": ""
}
],
"sort_order": "",
"limit": "",
"offset": ""
}
operation: Get Telemetry Packetstats
Input parameters
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied.
| Parameter |
Description |
| Sensor ID |
Specify the ID of the sensor based on which you want to retrieve telemetry packetstats from FortiNDR Cloud. |
| Interval |
Choose the interval based on which you want to retrieve telemetry packetstats from FortiNDR Cloud. You can choose between Hour (default) or Day. |
| Start DateTime |
Select the DateTime using which you want to filter the result set to only include only those items that have been created after the specified timestamp.
Note: The default is 1 day ago if you have selected the interval as 'Hour' or 30 days ago if you have selected the interval as 'Day'. |
| End DateTime |
Select the DateTime using which you want to filter the result set to only include only those items that have been created before the specified timestamp. |
| Group By |
Select Sensor ID as the criteria to group telemetry packetstats retrieved from FortiNDR Cloud. |
Output
The output contains the following populated JSON schema:
{
"result_count": "",
"columns": "",
"data": [
{
"timestamp": "",
"sensor_id": "",
"account_code": "",
"interface_name": "",
"tx_bytes": "",
"tx_packets": "",
"tx_errors": "",
"rx_bytes": "",
"rx_packets": "",
"rx_errors": "",
"rx_bits_per_second": ""
}
]
}
operation: Get Entity Tracking
Input parameters
| Parameter |
Description |
| Entity Type |
Select the type of entity whose tracking information you want to retrieve from FortiNDR Cloud. You can choose between IP Address (default), MAC Address, or Host Name. |
| Entity Value |
Specify the value of the entity (based on the entity type you have selected) whose tracking information you want to retrieve from FortiNDR Cloud |
| Start DateTime |
(Optional) Select the DateTime using which you want to filter the result set to only include only those items that have been created after the specified timestamp. |
| End DateTime |
(Optional) Select the DateTime using which you want to filter the result set to only include only those items that have been created before the specified timestamp. |
| Limit |
(Optional) Specify the maximum number of results, per page, that this operation should return. By default, this option is set as 100. |
| Offset |
(Optional) Index of the first item to be returned by this operation. This parameter is useful for pagination and for getting a subset of items. By default, this is set as 0. |
Output
The output contains the following populated JSON schema:
{
"entity_tracking_response": {
"limit": "",
"total": "",
"offset": "",
"dhcp_mac_ip_intervals": []
}
}
operation: Get Entity Summary
Input parameters
| Parameter |
Description |
| IP/Domain |
Specify the IP address or Domain for which you want to retrieve summary information from FortiNDR Cloud. |
Output
The output contains the following populated JSON schema:
{
"query_type": "",
"summary": {
"entity": "",
"first_seen": "",
"last_seen": "",
"prevalence_count_internal": "",
"tags": []
}
}
operation: Get Passive DNS Details
Input parameters
| Parameter |
Description |
| IP/Domain |
Specify the IP address Domain based on which you want to retrieve passive DNS details from FortiNDR Cloud. |
| Record Type |
Select the type of record based on which you want to retrieve entity passive DNS details from FortiNDR Cloud. You can choose from the following options: A, AAAA, CNAME, MX, or NS. |
| Start DateTime |
(Optional) Select the DateTime using which you want to filter the result set to only include only those items that have been created after the specified timestamp. |
| End DateTime |
(Optional) Select the DateTime using which you want to filter the result set to only include only those items that have been created before the specified timestamp. |
| Limit |
Specify the maximum number of results, per page, that this operation should return. By default, this option is set as 1000. |
Output
The output contains the following populated JSON schema:
{
"query_type": "",
"result_count": "",
"passivedns": [
{
"resolved": "",
"first_seen": "",
"last_seen": "",
"record_type": "",
"source": "",
"customer_id": "",
"account_uuid": "",
"sensor_id": ""
}
]
}
operation: Get Detections List
Input parameters
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied, and an unfiltered list (of detections) is returned.
| Parameter |
Description |
| Rule UUID |
Specify the UUID of the rule based on which you want to retrieve detections from FortiNDR Cloud. |
| Sensor ID |
Specify the ID of the sensor based on which you want to retrieve detections from FortiNDR Cloud. |
| Status |
Select the status of the detection based on which you want to retrieve detections from FortiNDR Cloud. You can choose one, more than one, or all of the following values: Active (default) or Resolved. |
| Device IP |
Specify the device IP address if you want to include only those detections associated with the specified device IP. |
| Muted |
Select this checkbox if you want this operation to return only those detections that are muted. By default, this option is cleared, i.e., set as 'false'. |
| Muted Device |
Select this checkbox if you want this operation to return only those detections whose associated devices are muted. By default, this option is cleared, i.e., set as 'false'. |
| Muted Rule |
Select this checkbox if you want this operation to return only those detections whose associated rules are muted. By default, this option is cleared, i.e., set as 'false'. |
| Include |
Choose to include verbose data for linked objects in the results. You can choose one, or more than one, or all of the following values: Rules or Indicators. |
| Indicator Value |
Specify an indicator value if you want to include only those detections associated with the specified indicator. |
| Created Start DateTime |
Select the DateTime using which you want to filter the result set to only include only those items that have been created after the specified timestamp. |
| Created End DateTime |
Select the DateTime using which you want to filter the result set to only include only those items that have been created before the specified timestamp. |
| Sort By |
Select the name of the field based on which you want to sort the result (detections) retrieved by this operation. You can choose from the following values: First Seen (default), Last Seen, Status, Device IP, or Indicator Count. |
| Sort Order |
Select the sorting order of the result. You can choose between Ascending or Descending (default). |
| Limit |
Specify the maximum number of results, per page, that this operation should return. By default, this option is set as 100. |
| Offset |
Index of the first item to be returned by this operation. This parameter is useful for pagination and for getting a subset of items. By default, this is set as 0. |
Output
The output contains the following populated JSON schema:
{
"result_count": "",
"total_count": "",
"detections": [
{
"uuid": "",
"rule_uuid": "",
"device_ip": "",
"sensor_id": "",
"account_uuid": "",
"status": "",
"muted_device_uuid": "",
"muted_rule": "",
"muted": "",
"muted_comment": "",
"muted_user_uuid": "",
"muted_timestamp": "",
"resolution_user_uuid": "",
"resolution_timestamp": "",
"resolution": "",
"resolution_comment": "",
"indicators": "",
"event_count": "",
"username": "",
"hostname": "",
"first_seen": "",
"last_seen": "",
"created": "",
"updated": ""
}
],
"sort_by": "",
"sort_order": "",
"offset": "",
"limit": "",
"rules": ""
}
operation: Resolve Detection
Input parameters
| Parameter |
Description |
| Detection UUID |
Specify the UUID of the detection that you want to resolve in FortiNDR Cloud. |
| Resolution |
Select the resolution that you want to assign to the specified detection you want to resolve in FortiNDR Cloud. You can choose from the following values: True Positive Mitigated, True Positive No Action, False Positive, or Unknown |
| Comment |
(Optional) Specify a comment that you want to associate with the specified detection you want to resolve in FortiNDR Cloud. |
Output
The output contains the following populated JSON schema:
{
"message": ""
}
operation: Get Devices with Detection
Input parameters
| Parameter |
Description |
| Account UUID |
Specify the UUID of the account based on which you want to retrieve devices with detections from FortiNDR Cloud. |
| Search |
(Optional) Specify the device IP address if you want to include only those detections associated with the specified device IP. |
| Muted |
(Optional) Select this checkbox if you want this operation to return only those devices with detections that are muted. By default, this option is cleared, i.e., set as 'false'. |
| Muted Device |
(Optional) Select this checkbox if you want this operation to return only those devices with detections whose associated devices are muted. By default, this option is cleared, i.e., set as 'false'. |
| Muted Rule |
(Optional) Select this checkbox if you want this operation to return only those devices with detections whose associated rules are muted. By default, this option is cleared, i.e., set as 'false'. |
| Status |
(Optional) Select the status of the detections based on which you want to retrieve devices with detections from FortiNDR Cloud. You can choose one, more than one, or all of the following values: Active (default) or Resolved. |
| Sort By |
(Optional) Select the name of the field based on which you want to sort the result (devices) retrieved by this operation. You can choose from the following values: Device IP, Detection Count, Last Seen (default), or Threat Score. |
| Sort Order |
(Optional) Select the sorting order of the result. You can choose between Ascending or Descending (default). |
| Limit |
(Optional) Specify the maximum number of results, per page, that this operation should return. By default, this option is set as 100. |
| Offset |
(Optional) Index of the first item to be returned by this operation. This parameter is useful for pagination and for getting a subset of items. By default, this is set as 0. |
Output
The output contains the following populated JSON schema:
{
"result_count": "",
"total_count": "",
"devices": [
{
"account_uuid": "",
"device_ip": "",
"threat_score": "",
"detections_count": "",
"last_seen": ""
}
],
"sort_by": "",
"sort_order": "",
"offset": "",
"limit": ""
}
operation: Get Detection Events
Input parameters
| Parameter |
Description |
| Detection UUID |
Specify the UUID of the detection based on which you want to retrieve events from FortiNDR Cloud. |
| Limit |
(Optional) Specify the maximum number of results, per page, that this operation should return. By default, this option is set as 100. |
| Offset |
(Optional) Index of the first item to be returned by this operation. This parameter is useful for pagination and for getting a subset of items. By default, this is set as 0. |
Output
The output contains the following populated JSON schema:
{
"events": [
{
"event": {
"dst": {
"ip": "",
"asn": {
"asn": "",
"isp": "",
"org": "",
"asn_org": ""
},
"geo": {
"city": "",
"country": "",
"location": "",
"subdivision": ""
},
"pkts": "",
"port": "",
"internal": "",
"ip_bytes": ""
},
"src": {
"ip": "",
"asn": "",
"geo": "",
"pkts": "",
"port": "",
"internal": "",
"ip_bytes": ""
},
"uri": {
"uri": "",
"host": "",
"path": "",
"port": "",
"query": "",
"scheme": "",
"fragment": ""
},
"host": {
"ip": "",
"asn": {
"asn": "",
"isp": "",
"org": "",
"asn_org": ""
},
"geo": {
"city": "",
"country": "",
"location": "",
"subdivision": ""
},
"pkts": "",
"port": "",
"internal": "",
"ip_bytes": ""
},
"uuid": "",
"files": [
{
"md5": "",
"name": "",
"sha1": "",
"bytes": "",
"sha256": "",
"mime_type": ""
}
],
"intel": "",
"method": "",
"source": "",
"flow_id": "",
"headers": {
"accept": "",
"origin": "",
"server": "",
"refresh": "",
"location": "",
"content_md5": "",
"content_type": "",
"x_powered_by": "",
"cookie_length": "",
"proxied_client_ips": ""
},
"proxied": "",
"info_msg": "",
"referrer": "",
"username": "",
"sensor_id": "",
"timestamp": "",
"event_type": "",
"status_msg": "",
"user_agent": "",
"application": "",
"customer_id": "",
"request_len": "",
"status_code": "",
"trans_depth": "",
"geo_distance": "",
"request_mime": "",
"response_len": "",
"request_mimes": "",
"response_mime": "",
"response_mimes": []
},
"rule_uuid": ""
}
],
"total_count": "",
"result_count": ""
}
operation: Get Detection Rule Indicators
Input parameters
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied, and an unfiltered list (of indicators) is returned.
| Parameter |
Description |
| Rule UUID |
Specify the UUID of the rule based on which you want to retrieve indicators from FortiNDR Cloud. |
| Detection Muted |
Select this checkbox if you want this operation to return only those rule indicators whose associated detections are muted. By default, this option is cleared, i.e., set as 'false'. |
| Detection Status |
Select the status of the detection based on which you want to retrieve rule indicators from FortiNDR Cloud. You can choose one, more than one, or all of the following values: Active (default) or Resolved. |
| Sort By |
Specify the name of the field based on which you want to sort the result (indicators) retrieved by this operation. By default, the results are sorted by the count field. |
| Sort Order |
Select the sorting order of the result. You can choose between Ascending or Descending (default) |
| Limit |
Specify the maximum number of results, per page, that this operation should return. By default, this option is set as 100. |
| Offset |
Index of the first item to be returned by this operation. This parameter is useful for pagination and for getting a subset of items. By default, this is set as 0. |
Output
The output contains the following populated JSON schema:
{
"limit": "",
"offset": "",
"sort_by": "",
"sort_order": "",
"rule_counts": [
{
"count": "",
"field": "",
"value": "",
"rule_uuid": ""
}
],
"total_count": "",
"result_count": ""
}
operation: Get Detection Rules List
Input parameters
Note: All the input parameters are optional. However, if you do not specify any parameter, then no filter criterion is applied, and an unfiltered list (of detection rules) is returned.
| Parameter |
Description |
| Rule Account UUID |
Specify the UUID of the rule account only if you want to include sub-objects for the specified account while retrieving detection rules from FortiNDR Cloud. |
| Search By |
Specify the text based on which you want to search for detection rules in FortiNDR Cloud. In this case, this operation returns only those rules that contain the specified string in their name or category. |
| Has Detection |
Select this checkbox to only return those rules that have unmuted or unresolved detections. By default, this option is cleared, i.e., set as 'false'. |
| Detection Device IP |
Specify the device IP address if you want to include only those rules with detections for the specified IP. Associated detections are determined by the has_detections parameter. |
| Indicator Value |
Specify the case-insensitive prefix to be used for searching indicators that are related to the rules you want to retrieve from FortiNDR Cloud. |
| Severity |
Select the severity based on which you want to retrieve detection rules from FortiNDR Cloud. You can choose one, more than one, or all of the following values: Low, Moderate, or High. |
| Confidence |
Select the confidence based on which you want to retrieve detection rules from FortiNDR Cloud. You can choose one, more than one, or all of the following values: Low, Moderate, or High. |
| Category |
Select the category based on which you want to retrieve detection rules from FortiNDR Cloud. You can choose one, or more than one, or all of the values such as Attack:Command and Control, Attack:Exploitation, PUA:Adware, etc. |
| Include Muted Rules |
Select this checkbox if you want this operation to return only those rules that are muted by the specified account. |
| Enabled |
Select this checkbox to only return those rules that are enabled. By default, this option is cleared, i.e., set as 'false'. |
| Sort By |
Select the name of the field based on which you want to sort the result (rules) retrieved by this operation. You can choose from the following values: Created, Updated (default), Detections, Severity, Confidence, Category, Last Seen, or Detections Muted. |
| Sort Order |
Select the sorting order of the result. You can choose between Ascending or Descending (default). |
| Limit |
Specify the maximum number of results, per page, that this operation should return. By default, this option is set as 100. |
| Offset |
Index of the first item to be returned by this operation. This parameter is useful for pagination and for getting a subset of items. By default, this is set as 0. |
Output
The output contains the following populated JSON schema:
{
"result_count": "",
"total_count": "",
"active_rule_count": "",
"enabled_rule_count": "",
"rules": [
{
"uuid": "",
"account_uuid": "",
"shared_account_uuids": "",
"run_account_uuids": "",
"name": "",
"category": "",
"query_signature": "",
"description": "",
"severity": "",
"confidence": "",
"auto_resolution_minutes": "",
"enabled": "",
"created_user_uuid": "",
"created": "",
"updated_user_uuid": "",
"updated": "",
"critical_updated": "",
"primary_attack_id": "",
"secondary_attack_id": "",
"specificity": "",
"rule_accounts": [
{
"account_uuid": "",
"query_filter": "",
"muted": "",
"muted_comment": "",
"muted_user_uuid": "",
"muted_timestamp": "",
"detection_count": "",
"detection_muted_count": "",
"detection_resolved_count": "",
"first_seen": "",
"last_seen": ""
}
],
"device_ip_fields": [],
"indicator_fields": [],
"source_excludes": []
}
],
"accounts": [
{
"uuid": "",
"name": ""
}
],
"sort_by": "",
"sort_order": "",
"offset": "",
"limit": ""
}
operation: Get Detection Rule Details
Input parameters
| Parameter |
Description |
| Rule UUID |
Specify the UUID of the rule based on which you want to retrieve the detection rule details from FortiNDR Cloud.
Note: The response of the "Get Detection Rules List" action contains the UUID of a rule. |
| Rule Account UUID |
(Optional) Specify the UUID of the rule account only if you want to include sub-objects for the specified account while retrieving detection rule details from FortiNDR Cloud. |
Output
The output contains the following populated JSON schema:
{
"rule": {
"uuid": "",
"account_uuid": "",
"shared_account_uuids": "",
"run_account_uuids": "",
"name": "",
"category": "",
"query_signature": "",
"description": "",
"severity": "",
"confidence": "",
"auto_resolution_minutes": "",
"enabled": "",
"created_user_uuid": "",
"created": "",
"updated_user_uuid": "",
"updated": "",
"critical_updated": "",
"primary_attack_id": "",
"secondary_attack_id": "",
"specificity": "",
"rule_accounts": [
{
"account_uuid": "",
"query_filter": "",
"muted": "",
"muted_comment": "",
"muted_user_uuid": "",
"muted_timestamp": "",
"detection_count": "",
"detection_muted_count": "",
"detection_resolved_count": "",
"first_seen": "",
"last_seen": ""
}
],
"device_ip_fields": [],
"indicator_fields": [],
"source_excludes": []
},
"accounts": [
{
"uuid": "",
"name": ""
}
]
}
operation: Get Detection Rule Events List
Input parameters
| Parameter |
Description |
| Rule UUID |
Specify the UUID of the rule based on which you want to retrieve detection rule events from FortiNDR Cloud. |
| Limit |
(Optional) Specify the maximum number of results, per page, that this operation should return. By default, this option is set as 100. |
| Offset |
(Optional) Index of the first item to be returned by this operation. This parameter is useful for pagination and for getting a subset of items. By default, this is set as 0. |
Output
The output contains the following populated JSON schema:
{
"result_count": "",
"total_count": "",
"events": [
{
"event_type": "",
"uuid": "",
"customer_id": "",
"sensor_id": "",
"timestamp": "",
"flow_id": "",
"src": {
"ip": "",
"port": "",
"ip_bytes": "",
"pkts": "",
"geo": "",
"asn": "",
"internal": ""
},
"dst": {
"ip": "",
"port": "",
"ip_bytes": "",
"pkts": "",
"geo": "",
"asn": "",
"internal": ""
},
"geo_distance": "",
"intel": "",
"source": "",
"evidence_end_timestamp": "",
"evidence_iql": "",
"evidence_start_timestamp": "",
"observation_category": "",
"observation_class": "",
"observation_confidence": "",
"observation_context": "",
"observation_title": "",
"observation_uuid": "",
"sensor_ids": []
}
]
}
Included playbooks
The Sample - Fortinet FortiNDR Cloud - 1.0.0 playbook collection comes bundled with the Fortinet FortiNDR Cloud connector. These playbooks contain steps using which you can perform all supported actions. You can see bundled playbooks in the Automation > Playbooks section in FortiSOAR™ after importing the Fortinet FortiNDR Cloud connector.
- > Fortinet FortiNDR Cloud > Create Detections
- > Fortinet FortiNDR Cloud > Fetch Detection Rules
- > Fortinet FortiNDR Cloud > Fetch Detections by Rules
- Download PCAP Task File
- Fortinet FortiNDR Cloud > Fetch Detections
- Get Detection Events
- Get Detection Rule Details
- Get Detection Rule Events List
- Get Detection Rule Indicators
- Get Detection Rules List
- Get Detections List
- Get Devices with Detection
- Get Entity Summary
- Get Entity Tracking
- Get PCAP Tasks
- Get Passive DNS Details
- Get Sensors List
- Get Telemetry Bandwidth
- Get Telemetry Events
- Get Telemetry Packetstats
- Resolve Detection
- Terminate PCAP Task
Note: If you are planning to use any of the sample playbooks in your environment, ensure that you clone those playbooks and move them to a different collection since the sample playbook collection gets deleted during the connector upgrade and delete.
Data Ingestion Support
Use the Data Ingestion Wizard to easily ingest data into FortiSOAR™ by pulling detections from FortiNDR Cloud. Currently, "detections" in FortiNDR Cloud are mapped to "alerts" in FortiSOAR™. For more information on the Data Ingestion Wizard, see the "Connectors Guide" in the FortiSOAR™ product documentation.
Configure Data Ingestion
You can configure data ingestion using the “Data Ingestion Wizard” to seamlessly map the incoming FortiNDR Cloud "detections" to FortiSOAR™ "Alerts".
The Data Ingestion Wizard enables you to configure the scheduled pulling of data from FortiNDR Cloud into FortiSOAR™. It also lets you pull some sample data from FortiNDR Cloud using which you can define the mapping of data between FortiNDR Cloud and FortiSOAR™. The mapping of common fields is generally already done by the Data Ingestion Wizard; users mostly require to only map any custom fields that are added to the FortiNDR Cloud event.
- To begin configuring data ingestion, click Configure Data Ingestion on the FortiNDR Cloud connector’s "Configurations" page.
Click Let’s Start by fetching some data, to open the “Fetch Sample Data” screen.
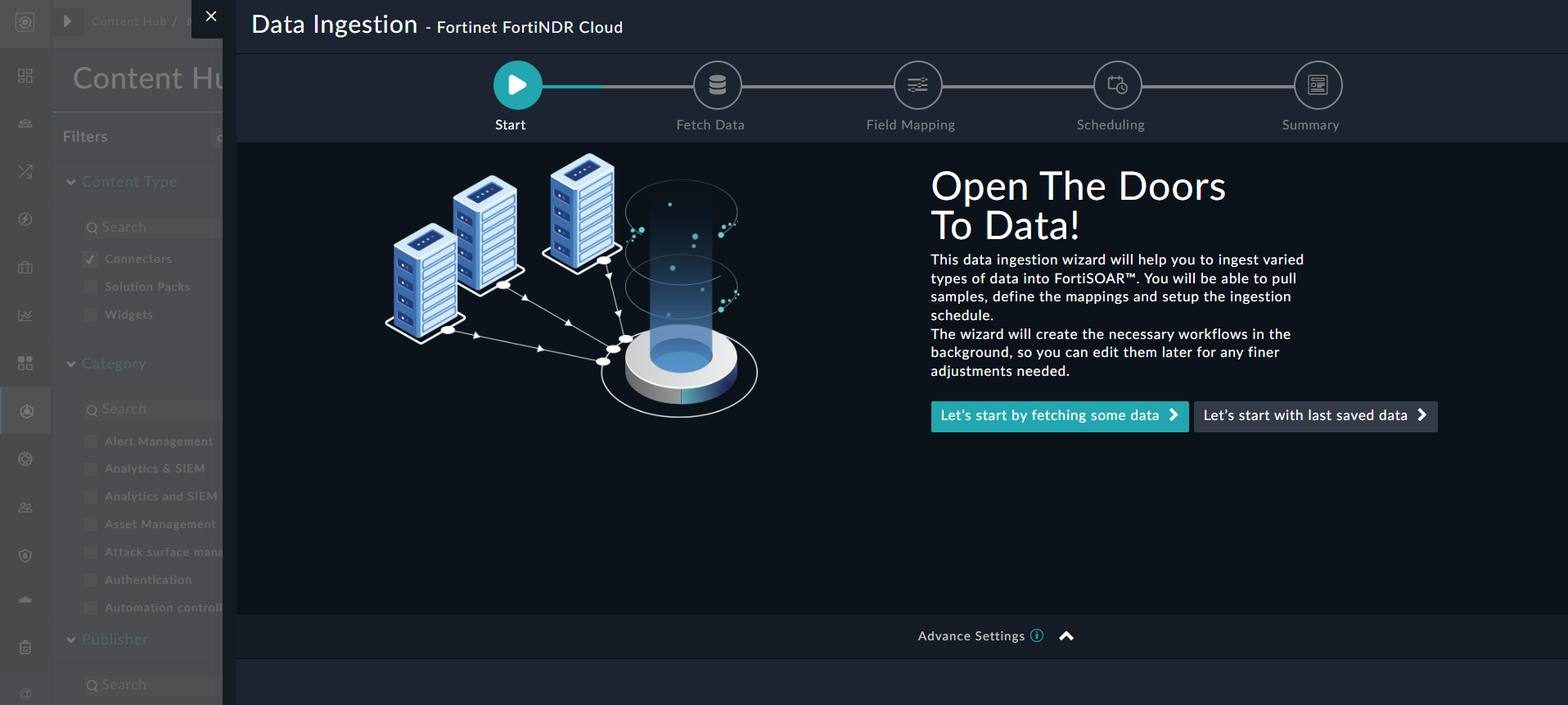
Sample data is required to create a field mapping between FortiNDR Cloud data and FortiSOAR™. The sample data is pulled from connector actions or ingestion playbooks.
- On the Fetch Data screen, provide the configurations required to fetch FortiNDR Cloud data.
Users can pull data from FortiNDR Cloud by specifying the last X minutes based on which they want to pull detections from FortiNDR Cloud. You can filter detections retrieved from FortiNDR Cloud based on the detection's status, and the rule's severity or confidence, as well as sort the retrieved results based on a field. If you want to retrieve only those detections that are muted, select the Muted checkbox. Additionally, you can also specify the maximum number of detections to be pulled from FortiNDR Cloud; the default is set as 100 detection records.
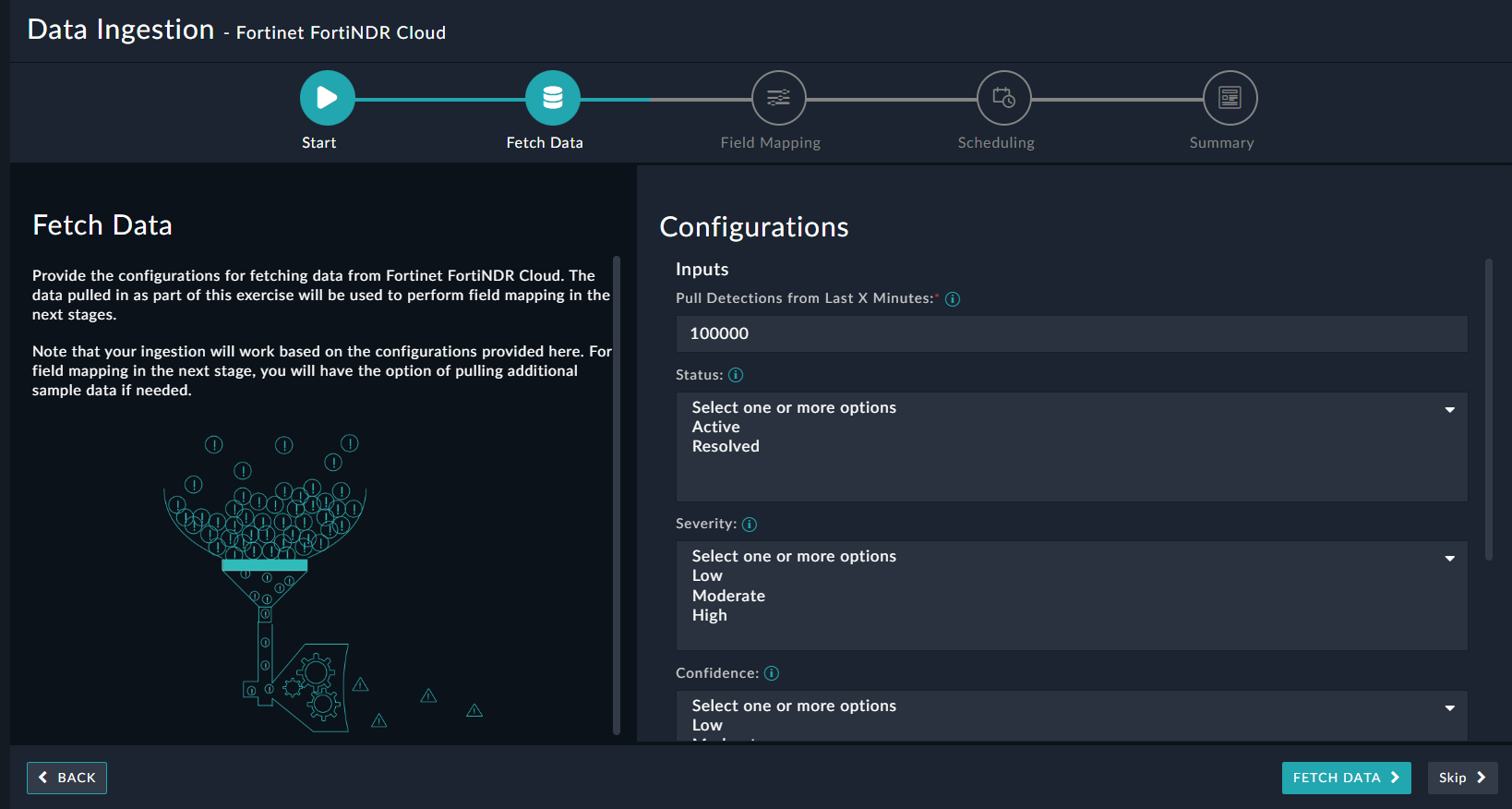
The fetched data is used to create a mapping between the FortiNDR Cloud data and FortiSOAR™ alerts. Once you have completed specifying the configurations, click Fetch Data.
-
On the Field Mapping screen, map the fields of a FortiNDR Cloud event to the fields of an alert present in FortiSOAR™.
To map a field, click the key in the sample data to add the “jinja” value of the field. For example, to map the confidence parameter of a FortiNDR Cloud event to the Confidence parameter of a FortiSOAR™ alert, click the Confidence field, and then click the confidence field to populate its keys:
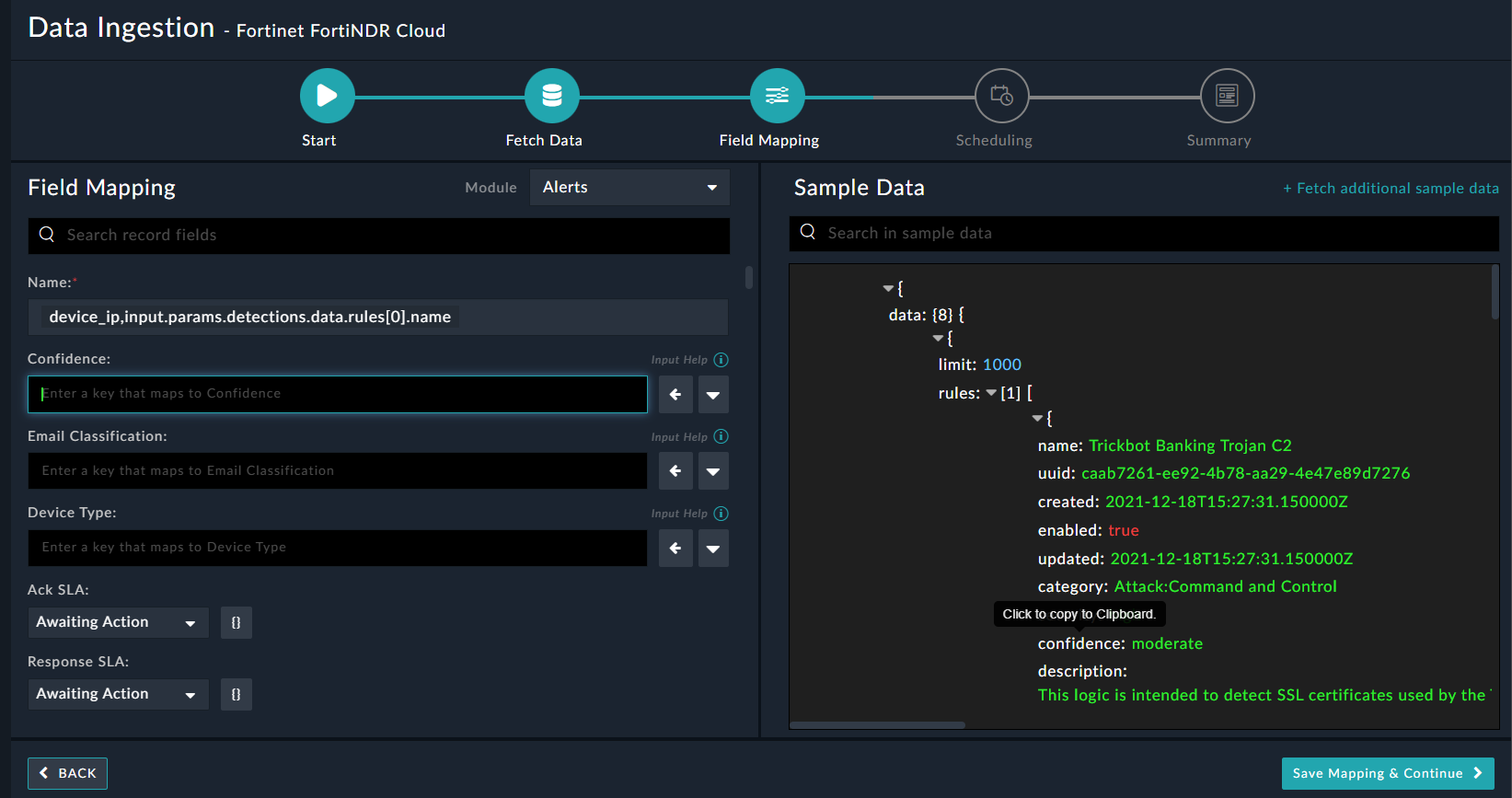
For more information on field mapping, see the Data Ingestion chapter in the "Connectors Guide" in the FortiSOAR™ product documentation. Once you have completed mapping fields, click Save Mapping & Continue.
-
Use the Scheduling screen to configure schedule-based ingestion, i.e., specify the polling frequency to FortiNDR Cloud, so that the content gets pulled from the FortiNDR Cloud integration into FortiSOAR™.
On the Scheduling screen, from the Do you want to schedule the ingestion? drop-down list, select Yes.
In the “Configure Schedule Settings” section, specify the Cron expression for the schedule. For example, if you want to pull data from FortiNDR Cloud every morning at 5 am, click Daily, and in the hour box enter 5 , and in the minute box enter 0:
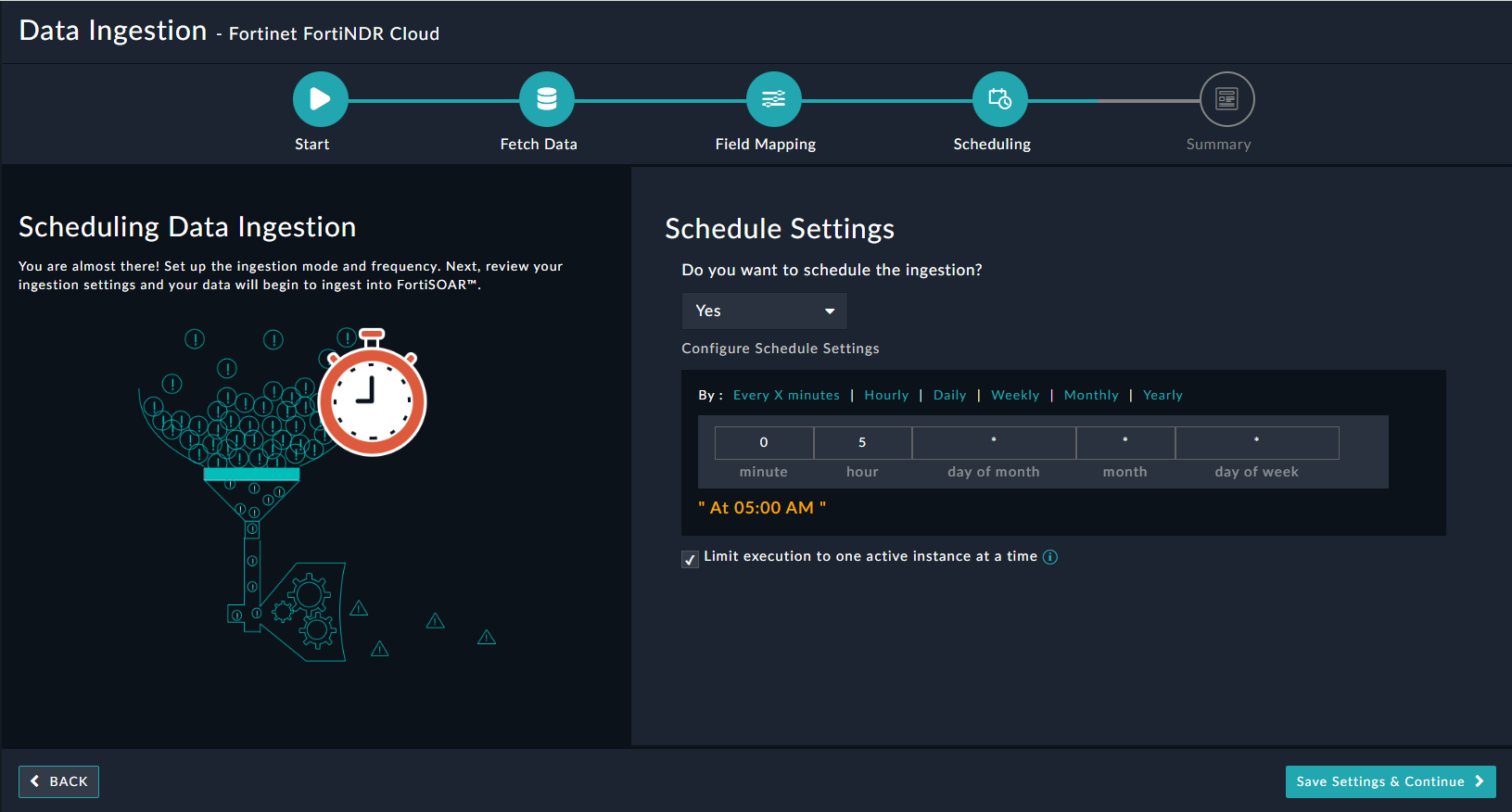
Once you have completed scheduling, click Save Settings & Continue.
-
The Summary screen displays a summary of the mapping done, and it also contains links to the Ingestion playbooks. Click Done to complete the data ingestion, and exit the Data Ingestion Wizard.









