Adding an Entra ID server
You can integrate Microsoft Entra ID (formerly known as Azure Active Directory or Azure AD) with on-premise EMS and FortiClient Cloud.
To create an enterprise application for FortiClient:
- In the Azure portal, go to Microsoft Entra ID > Enterprise applications > New application.
- Click Create your own application.
- In the What's the name of your app? field, enter the desired name.
- Under What are you looking to do with your application?, select Register an application to integrate with Azure AD (App you're developing).
- Click Create.
To add Microsoft Graph API application permissions required for searching user groups:
- In the left menu, click App registrations, then click the All applications tab.
- Click your FortiClient enterprise application.
- In the left menu, click API permissions, and click Add a permission.
- In the Request API permissions slide-in, click Microsoft Graph.
- Select Application permissions.
- In the Select permissions section, search for and select the following permissions:
- Device.Read.All
- Domain.Read.All
- Group.Read.All
- GroupMember.Read.All
- Mail.Read
- User.Read
- User.Read.All
- Click Add permissions.
- In the API permissions page, click Grant admin consent for Default Directory. If this option is grayed out, you must log into an Azure admin account to perform this step.
To add a client secret string and determine its value:
- In the left menu, click App registrations, then click the All applications tab.
- Click your FortiClient enterprise application.
- In the left menu, click Certificates & secrets, and click New client secret.
- In the Add a Client Secret slide-in, add a Description and select the desired Expires option. Click Add.
- Observe that a new client secret has been created. Immediately after creation, copy the Value of the client secret string, which EMS uses as the Azure Client Secret. This value is not visible after this initial creation step and moving to another page.
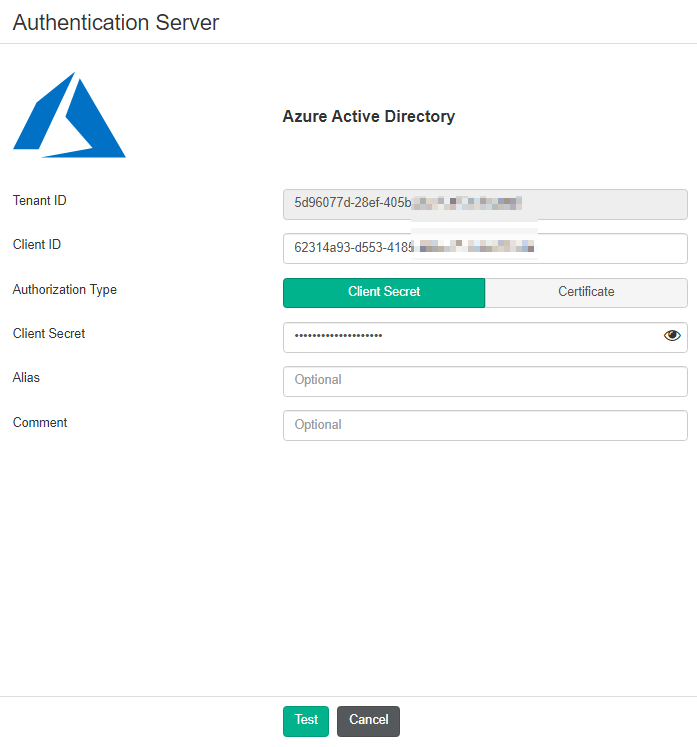
To configure an Entra ID server in EMS:
- Configure the Entra ID server as an authentication server in EMS:
- In the Azure management console, collect your tenant ID, client ID, and client secret.
- Go to Administration > Authentication Servers.
- Click Add > Azure.
- In the Tenant ID and Client ID fields, enter the IDs that you collected from the Azure management console.
- For Authorization Type, select Client Secret.
- In the Client Secret field, enter the client secret that you collected from the Azure management console.
- Configure other fields as desired.
- Click Test.
- After the test succeeds, click Save.
- Go to Endpoints > Manage Domains.
- Click Add, then Azure.
- From the Azure Server dropdown list, select the desired server.
- In the Sync every field, enter the number of minutes after which EMS syncs with the Azure server.
- For Group Selection Behaviour, select Import Entire Azure Domain or Import Selected Azure Groups.
- Enable Import as Base Group for the desired groups, then click Save.
Endpoints > Domains lists the Entra ID server domain groups and subgroups. It lists subgroups as a flat list and does not preserve the hierarchy from the AD server.
When using user management, Entra ID users can register their FortiClient to EMS using an invitation code or with SAML.
To configure the Azure tenant app for initiating passthrough (domain):
This is necessary for registering an Entra ID endpoint to EMS using an invitation code. This only applies for Entra ID-joined endpoints.
- Configure the redirect URL:
- In the Azure portal, go to App registration. Copy the application/client ID of the application used to connect with EMS.
- Click the application, then click the Redirect URIs link.
- Click Add a Platform > Select Mobile and Desktop applications.
- Add the following URL: ms-appx-web://microsoft.aad.brokerplugin/<application client ID>.
- Under Allow public client flows, toggle to Yes for Enable the following mobile and desktop flows.
- Save the configuration.
- Go to Roles and administrators.
- Search for and select Directory Readers.
- Click Add assignments.
- Select the application used to connect with EMS.
- Add desired users to the application in Entra ID:
- Go to Enterprise applications, and select the application used to connect with EMS.
- Go to Users and groups.
- Click Add user/group, and select the users that you will invite to EMS using an invitation code.
To register an Entra ID user's endpoint to EMS using an invitation code:
- In the EMS top banner, click Invitations.
- Click Add.
- For Verification Type, select Domain.
- From the LDAP Domain dropdown list, select the Entra ID server.
- Configure other settings as desired, then click Save.
- On the endpoint, go to Settings > Accounts.
- Under Access work or school, click Connect.
- Log in as an Entra ID user.
- In FortiClient, on the Zero Trust Telemetry tab, enter the invitation code to register to EMS. FortiClient register to EMS as the logged in Entra ID user without additional prompts.
To register an Entra ID user's endpoint to EMS using SAML:
You must copy some values from the Azure portal to EMS and other values from EMS to the Azure portal to complete the configuration.
- In EMS, create a SAML configuration:
- In EMS, go to User Management > SAML Configuration.
- Click Add.
- For Authorization Type, select LDAP.
- From the Domain dropdown list, select the Entra ID server.
- In this configuration, EMS acts as the service provider, while the Entra ID server is the identity provider. In the SP Address field, enter the EMS IP address or FQDN. You can also use the Use Current URL button to populate the field.
- In Azure, add and configure the Entra ID SAML Toolkit:
- Go to Enterprise applications, then click New application.
- Search for and select Azure AD SAML Toolkit.
- Configure a name for the toolkit as desired, then click Create.
- Click into the toolkit, select Single sign-on, then SAML.
- Under Basic SAML Configuration, click Edit.
- Copy the values from EMS in User Management > SAML Configuration > Service Provider Settings to the Azure portal. This table maps the EMS SAML fields that you must copy from EMS and configure in Entra ID. Configure as the table summarizes, then click Save.
EMS SAML field
Entra ID Basic SAML Configuration field
SP Entity ID
Identifier (Entity ID)
SP ACS (login) URL
Reply URL (Assertion Consumer Service URL)
SP Address
Sign on URL
- Under Attributes & Claims, click Edit.
- Click Unique User Identifier.
- From the Source attribute dropdown list, select user.localuserpricipalname. Click Save.
- In Azure, add a new claim:
- Click Add new claim.
- In the Name field, enter the domain identification value from EMS. You can find this value on EMS in User Management > SAML Configuration > Assertion Attributes > Domain Identification. This field is only visible when LDAP is selected as the Authorization Type and the Domain field is populated in SAML Configuration.
- Ensure that Namespace is empty.
- From the Source attribute field, select user.localprincipalname. Click Save.
- Under SAML Certificates, download the Certificate (Base64) file.
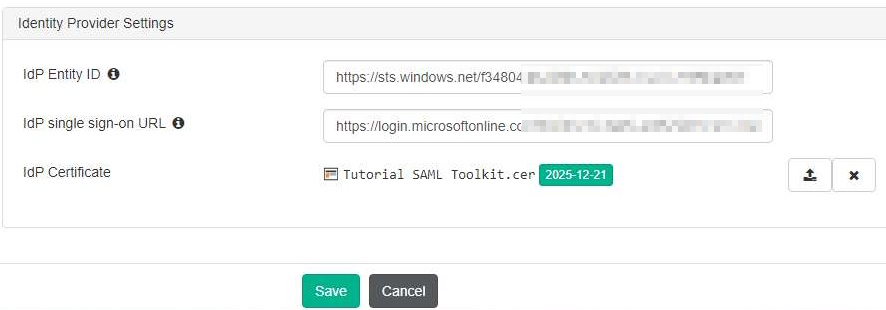
- Copy the URLs under Set up Tutorial SAML Toolkit to EMS:
- Copy the Entra ID Identifier value to the IdP Entity ID field in EMS.
- Copy the Login URL value to the IdP single sign-on URL field in EMS.
- In the IdP certificate field, upload the certificate that you downloaded in step 3. Save the SAML configuration in EMS.
- In Azure, go to Users and groups. Add users to the list as desired. Azure authorizes any user added to this list to connect to EMS.
- Configure the invitation in EMS:
- In the top banner, click Invitations.
- Click Add.
- For Verification Type, select SAML.
- From the SAML Config dropdown list, select the SAML configuration.
- Configure other settings as desired, then click Save.
- You can authenticate the endpoint using Entra ID by doing one of the following:
- To join the device to the Entra ID server, do the following:
- On the endpoint, go to Settings > Accounts.
- Under Access work or school, click Connect.
- Log in as an Entra ID user.
- In FortiClient, on the Zero Trust Telemetry tab, enter the invitation code to register to EMS. FortiClient register to EMS as the logged in Entra ID user without additional prompts.
- For a workgroup endpoint or an endpoint joined to an on-premise domain, in FortiClient, on the Zero Trust Telemetry tab, enter the invitation code to register to EMS. A Microsoft single sign on prompt displays. Enter the Entra ID user credentials to authenticate and connect FortiClient to EMS.
- To join the device to the Entra ID server, do the following:
The EMS administrator can configure endpoint policies and deployment configurations for specific endpoint groups from an Entra ID server.