Universal Connector 1.0.0 Administration Guide
Configuring the Cisco ACI connector
Configuring the Cisco ACI connector
To configure the Cisco ACI Universal Connector:
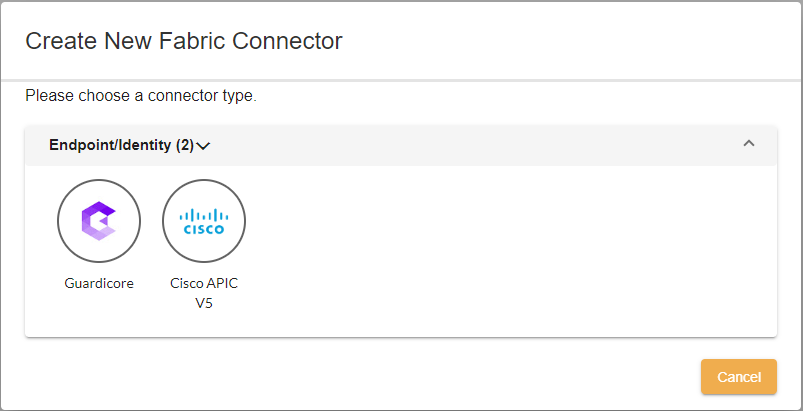
- Go to Management Extensions > Universal Connector.
- Click Create New on the toolbar, and select Cisco ACI.
- Enter the connector settings.
- Click Save & Continue, and then set the Status toggle to the on position to enable the connector.
- You can manually enter the update Interval for FortiManager to communicate with the Cisco APIC. The default is 60 seconds.
- FortiManager will authenticate against Cisco APIC using the credentials provided by the administrator on this page. Only once the authentication is successful can the connector can be enabled.
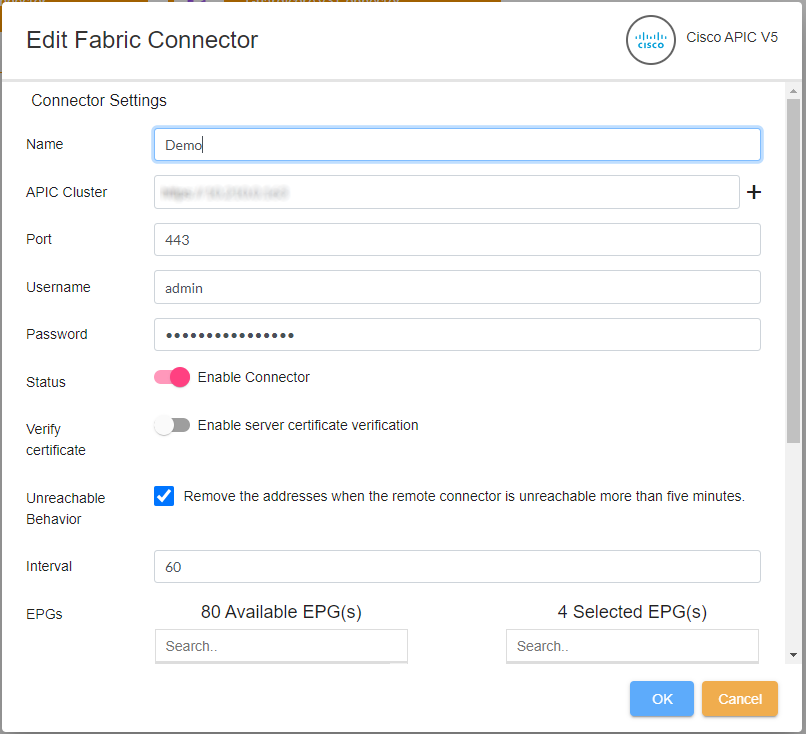
- You can enable/disable the certificate verification check for the remote Cisco APIC server.
The behavior for certificate verification is as follows:- If the remote certificate is valid and we enable the certificate verification, login succeeds.
- If the remote certificate is valid and we disable the certificate verification, login succeeds.
- If the remote certificate is invalid and we enable the certificate verification, login fails.
- If the remote certificate is invalid and we disable the certificate verification, login succeeds.
- Enable the connector in Policy & Objects. See Enabling Universal Connector MEA in Policy & Objects.
Configuring the Cisco ACI connector
To configure the Cisco ACI Universal Connector:
- Go to Management Extensions > Universal Connector.
- Click Create New on the toolbar, and select Cisco ACI.

- Enter the connector settings.
- Click Save & Continue, and then set the Status toggle to the on position to enable the connector.
- You can manually enter the update Interval for FortiManager to communicate with the Cisco APIC. The default is 60 seconds.
- FortiManager will authenticate against Cisco APIC using the credentials provided by the administrator on this page. Only once the authentication is successful can the connector can be enabled.

- You can enable/disable the certificate verification check for the remote Cisco APIC server.
The behavior for certificate verification is as follows:- If the remote certificate is valid and we enable the certificate verification, login succeeds.
- If the remote certificate is valid and we disable the certificate verification, login succeeds.
- If the remote certificate is invalid and we enable the certificate verification, login fails.
- If the remote certificate is invalid and we disable the certificate verification, login succeeds.
- Enable the connector in Policy & Objects. See Enabling Universal Connector MEA in Policy & Objects.



