Configure the connector
To configure the Azure Universal Connector:
-
Enable the Universal Connector. See Enabling Universal Connector MEA.
-
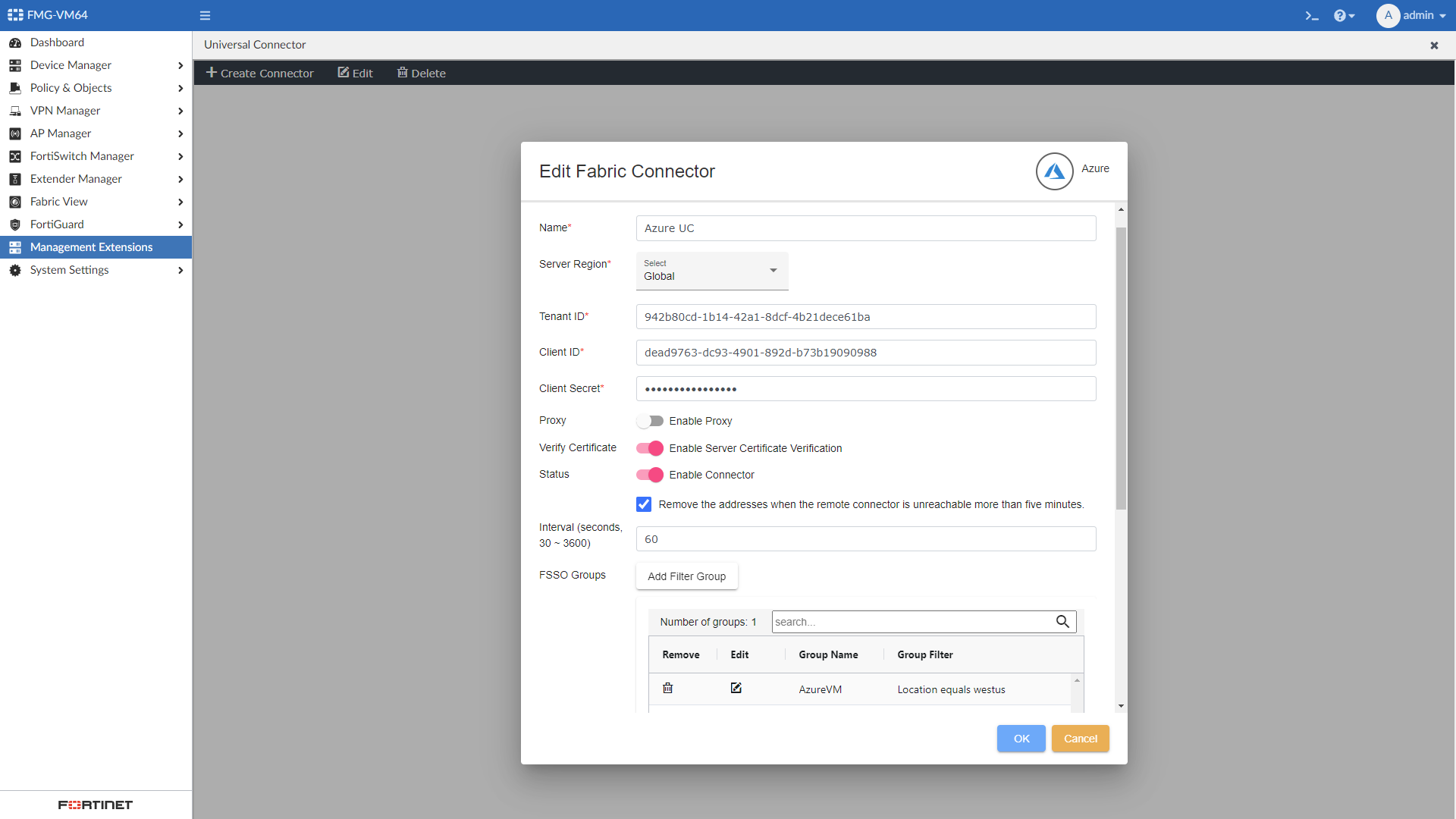
Go to Management Extensions > Universal Connector.
-
Click Create New on the toolbar, and select Azure.
-
Configure the connector settings:
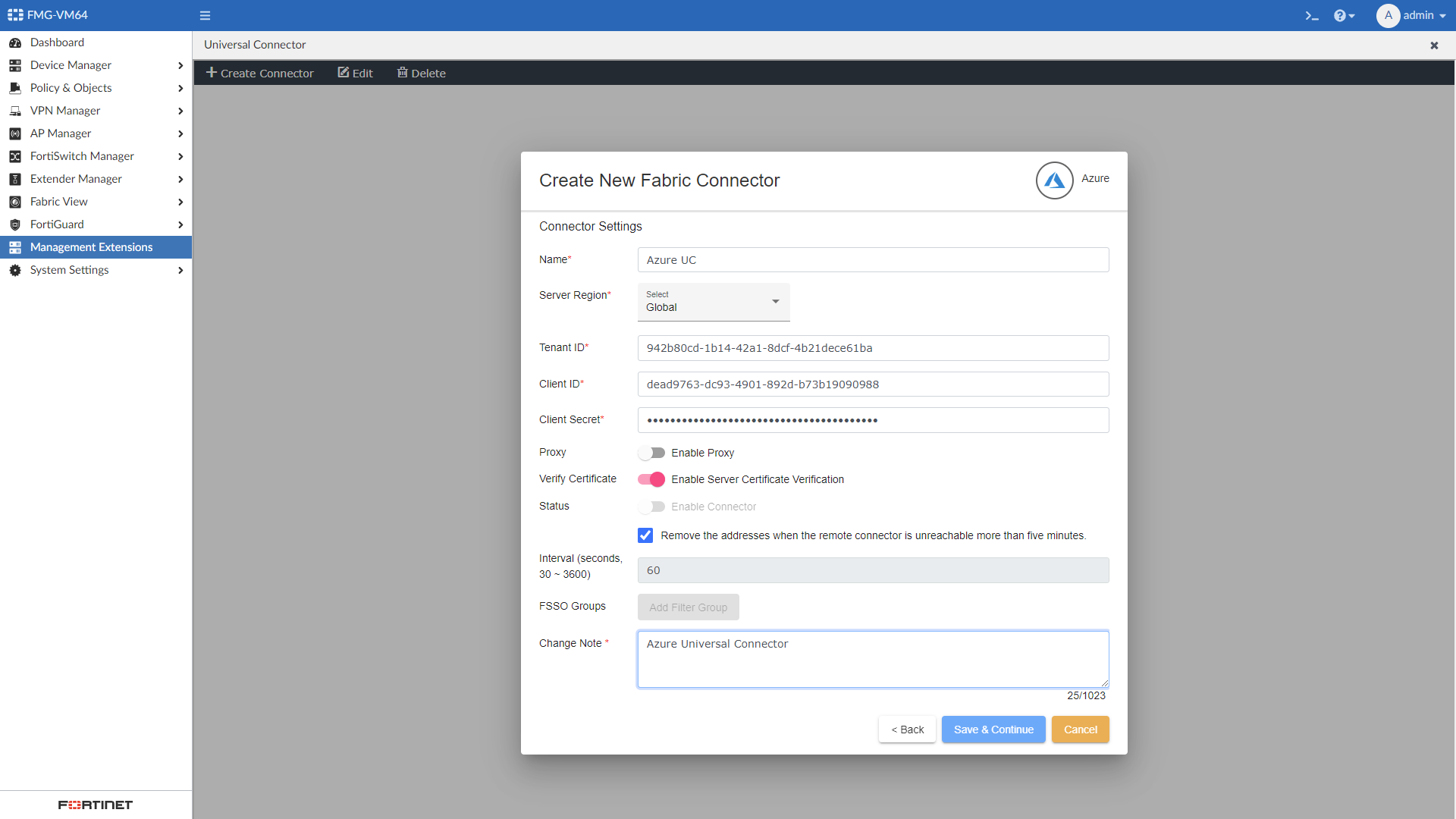
Name Enter the connector name. Server Region Select an Azure region. Tenant ID Enter your tenant ID. Client ID Enter your client ID. Client Secret
Enter your client secret. Proxy
Enable the proxy option if your FortiManager and FortiGate are behind proxy servers.
When Proxy is enabled, you can select the following:
Authentication Method Specify the authentication method as either Basic or Kerberos. Proxy Scheme Choose either HTTP or HTTPS. Proxy Host Enter the proxy host information. Proxy Username
Enter the proxy username.
Proxy Password
Enter the proxy password.
Realm
Specify a Kerberos realm.
This setting is only available when using the Kerberos Authentication Method.
SPN
Enter a Service Principal Name (SPN).
This setting is only available when using the Kerberos Authentication Method.
Kerberos Configuration
Enter the Kerberos configuration.
Below is an example of how to input Kerberos configurations:
[realms]
DEMO.IO = {
kdc = demo-vm1.demo.io
}
This setting is only available when using the Kerberos Authentication Method.
Verify Certificate
Enable or disable server certificate verification.
Status
Enable or disable the connector.
The status is disabled by default and cannot be enabled until you have added a FSSO group.
Remove the addresses when the remote connector is unreachable for more than five minutes.
This option is enabled by default, and addresses are cleared if the connection to Azure is lost for five minutes.
When the checkbox is not selected, all address information is maintained until the connection is reestablished or the administrator changes the connector configuration.
Interval
You can manually change the interval for the Universal Connector to fetch groups and IPS from Azure and then send them to FortiManager. The default interval is 60 seconds.
-
Click Save & Continue.
-
Configure the FSSO Groups by clicking Add Filter Group.
Add Filter Group is grayed out by default, and you can only select it after you have entered all of the credential information required by the connector and clicked Save & Continue.-
Configure the FSSO Group Name.
-
Select the Add Conditions, and click Apply.

-
Click Add.
-
-
Toggle the Status of the connector to ON, fill in a change note, and click OK.