Creating secret templates
To create a secret template:
- Go to Secrets > Secret Templates.
- In the secret templates list, select Create.
The New Secret Template window opens.
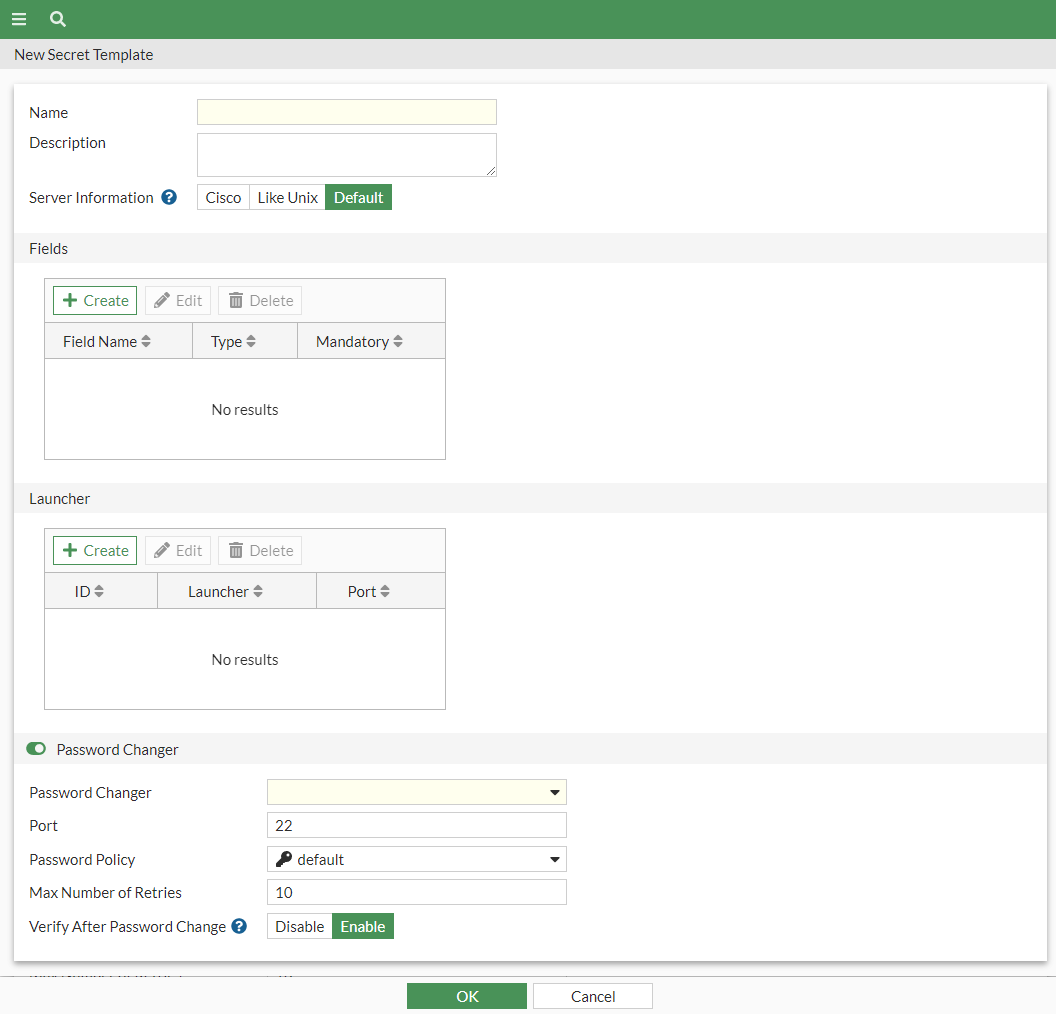
- Enter the following information:
Name
Name of the template.
Description
Optionally, enter a description.
Server Information
The general type of server to which the template is intended to connect:
Cisco
Like Unix
Default
Fields
Secrets require fields to enter the secret related information.
To add new fields, select Create and then enter the following information, and click OK:
Field Name
The name of the field.
Type
From the dropdown, select a field type:
Domain: A domain field.
Passphrase: A passphrase fields.
Password: A password field.
Private-Key: A private-key field.
Public-Key: A public-key field.
Target-Address: A target address field.
Text: A text field.
URL: A URL field.
Username: A username field.
Mandatory
Enable to make this field mandatory or disable if this field will be optional.

From the list, select a field and then select Edit to edit the field.
From the list, select fields and then select Delete to delete the fields.
Launcher
Launcher helps you access a target server. See Secret launchers.
A launcher allows you to log in to a website or device without you needing to know the credentials.
To add a new launcher, select Create and then enter the following information, and click OK:
Launcher Name
From the dropdown, select a launcher.

Use the search bar to look up a launcher.

Use the pen icon to edit a custom launcher.
To create a new launcher, in the dropdown, select Create.
Enter the following information and click OK:
Name
The name of the launcher.
Type
From the dropdown, select a launcher type:
Other client: Other client launcher type.
Remote desktop: RDP client launcher type.
SSH client: SSH client launcher type.
VNC: VNC client launcher type.
Executable
The program file name, e.g.,
putty.exefor an SSH client.
Ensure that the program path is already added to the environment variable path in Windows before launching the secret.
Note:
An absolute path is also supported. Use the escape character (
\) when using an absolute path, e.g.:C:\\Users\\user1\\Documents\\putty.exeC:\\Users\\user1\\Documents\\New folder\\putty.exeParameter
The command line parameters:
$DOMAIN$TARGET$HOST$USER$PASSWORD$VNCPASSWORD$PASSPHRASE$PUB_KEY$PRI_KEY$URL$PORT$TMPFILE
Example
For
putty.exeas the Executable,-|$USER -pw $PASSWORD $HOSTare the parameters.For
putty.exeas the Executable for SSH execution,-l $USER -pw $PASSWORD $HOST -m C:\\Users\\user1\\Desktop\\cmd.txtor
-l $USER -pw $PASSWORD $HOST -m \"C:\\Program Files\\cmd.txt\"are the parameters.
For the full path of a file, use the escape character double backslash (
\\) for the-mparameter.Note:
When there is no space in the path, double quotes are not necessary:
-l $USER -pw $PASSWORD $HOST -m C:\\Users\\user1\\Desktop\\cmd.txtWhen there is space in the path, double quotes must be used with backslash:
-l $USER -pw $PASSWORD $HOST -m \"C:\\Program Files\\cmd.txt\"Initial Commands
Configure initializing the environment. See Creating a new launcher command.
Clean Commands
Configure cleaning the environment. See Creating a new launcher command.
Launcher Port The launcher port number.

The port number will be mapped to the launcher variable `
$PORT`.
The minimum allowed value is
1.
From the list, select a launcher and then select Edit to edit the launcher.
From the list, select launchers and then select Delete to delete the launchers.
Password Changer
A password changer can be configured for a custom secret template to change the password of a secret periodically and to check the health of a secret periodically.
Note: The option is enabled by default.
Password Changer
From the dropdown, select the password changer that will be used for this template or create a new password changer. See Creating a password changer.

Use the search for to look up a password changer.

Use the pen icon next to a password changer to edit it.
Port
The port used for the password changer (default = 22).
Password Policy
The password policy to use in the password changer.
From the dropdown, select a password policy or create a new password policy. See Creating a password policy.

Use the search for to look up a password policy.

Use the pen icon next to a password policy to edit it.
Max Number of Retries
The maximum number of retries allowed after which the connection fails (default = 10).
Verify After Password Change
When enabled, whenever secrets with the template conducts a password change, a verification of the newly changed password is ran.
Note: The option is enabled by default.
- Click OK.

