Creating a user
|
|
By default, FortiPAM has a default user with the username When you go into the system for the first time, you must set a password for this account. Additional users can be added later. |
To create a user:
-
Go to User Management > User List, and select Create
The New User List wizard is launched.
- Enter the following information, and click Next after each tab:
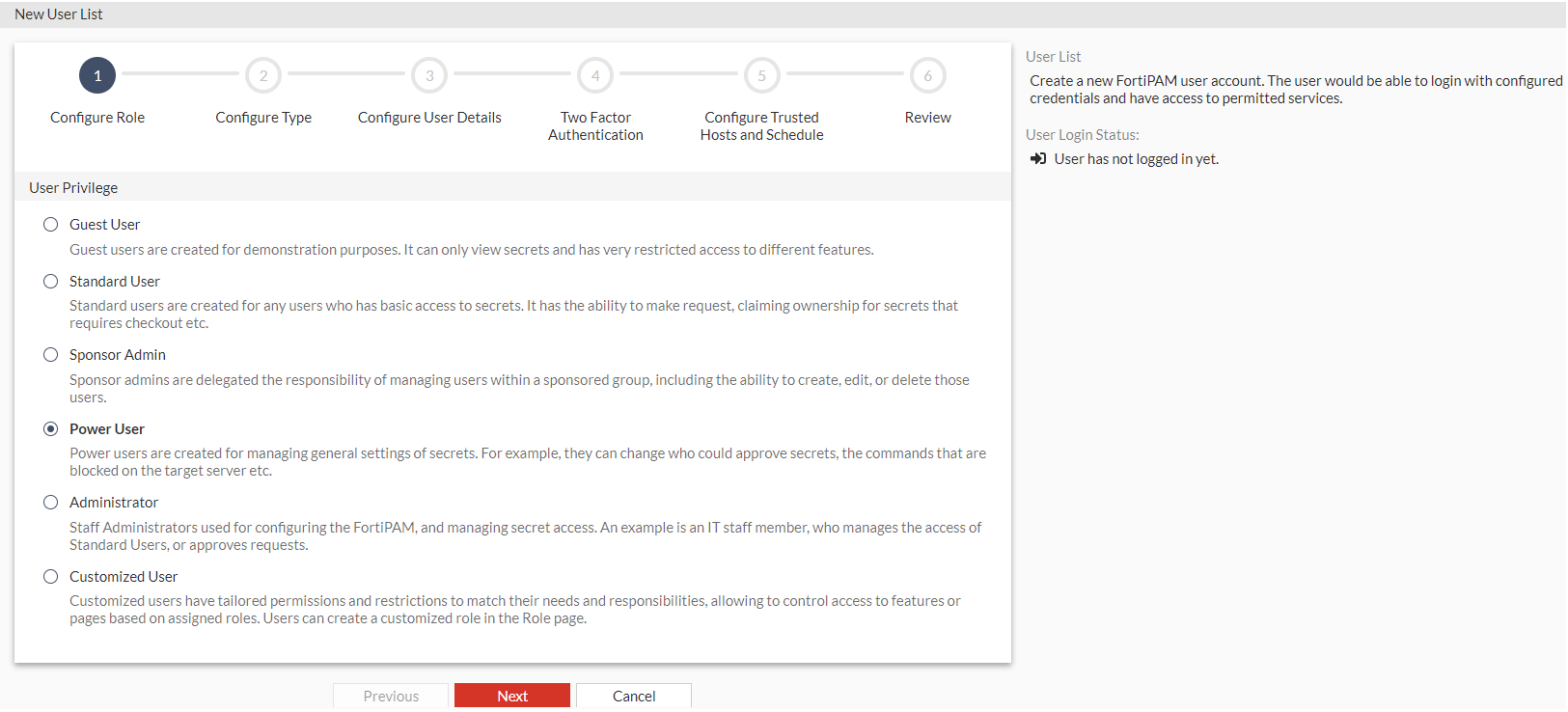
Configure Role
User Privilege
Select from the following user role types:
Guest User
Standard User
Sponsor Admin
Power User
Administrator
Customized User
For Sponsor Admin, select a sponsor admin role and a sponsored group. Sponsor admins can only manage users within their assigned sponsored group. For more information about sponsored groups, see Sponsored groups.
For Administrator, select from one of the available administrator roles from the Choose an Administrator Role dropdown.
For Customized User, select from one of the available custom roles from the Choose a custom defined Role dropdown.

The sponsor admin/administrator/custom role decides what a sponsor admin, administrator, or customized user can see. Depending on the nature of the administrator work, access level, or seniority, you can allow them to view and configure as much or as little as required.

Use the search bar to look for an administrator/custom role.
For information on the user types and their roles, see Users in FortiPAM and Role.
Configure Type
User Type
Select a user type:
Local User

To change the local user password, see Admin.
API User
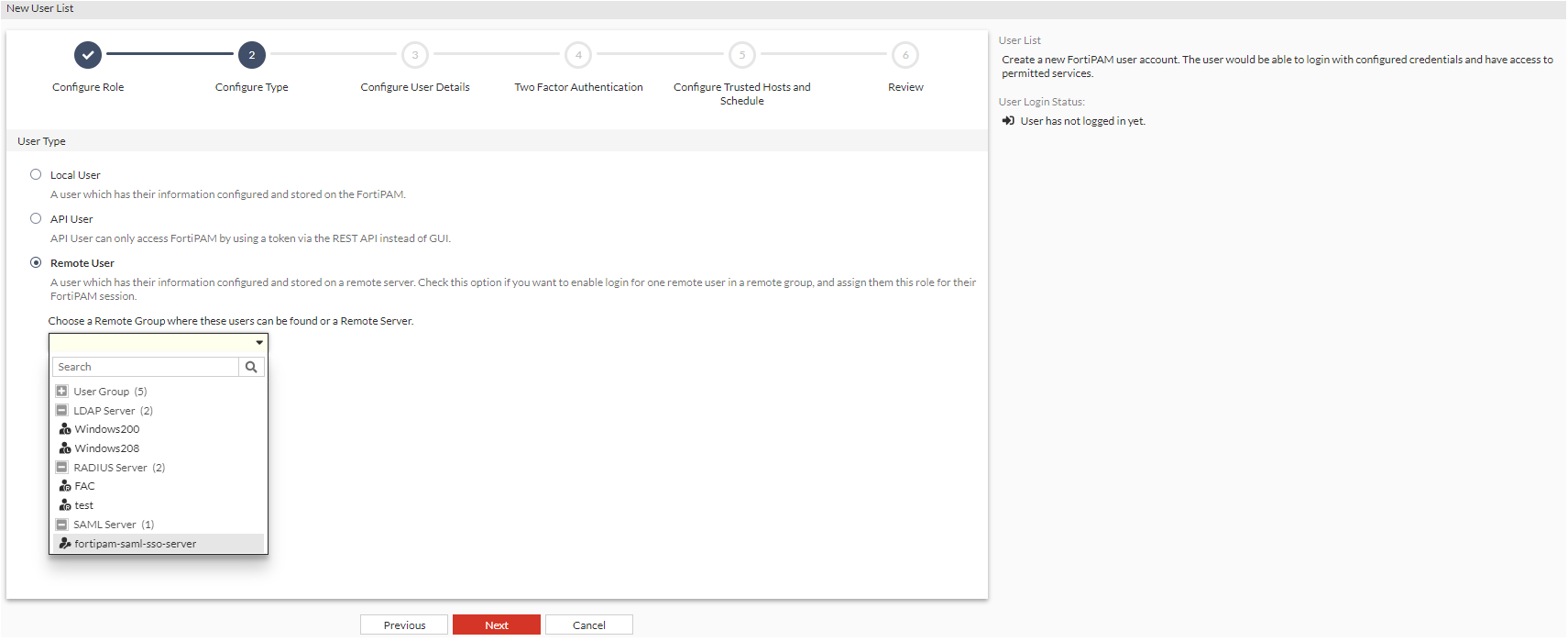
Remote User: Select the option if you want to enable login for one remote user in a remote group, and assign the user the remote user type for the FortiPAM session.
For Remote User, select a remote group where the user is found from the Choose a Remote Group where these users can be found or a Remote Server dropdown. See User groups.

Use the search bar to look for a remote group.
For information on the user types, see Users in FortiPAM.
Or
For Remote User, select a remote server where the user resides from the Choose a Remote Group where these users can be found or a Remote Server dropdown. See LDAP servers, SAML Single Sign-On (SSO), and RADIUS servers.

Use the search bar to look for a remote server.

In the Choose a Remote Group where these users can be found or a Remote Server dropdown, remote user groups and remote servers are mutually exclusive, i.e., only one can be selected.
Force SAML Login
Enable/disable forced SAML login (default = disable).
Note: This option must be enabled when creating a SAML user.
Configure User Details
Username
The username.

Do not use
< > ( ) # " '`characters in the username.Password The password.
Note: This option is only available when the user type is local.
Confirm Password
Enter the password again to confirm.
Note: This option is only available when the user type is local.
Status
Enable/disable user login to FortiPAM.

When you attempt to create a new user that exceeds the licensed seats, the Status option in the Configure User Details tab cannot be enabled.
As you hover over the Enable button, a tooltip appears, alerting you that the user cannot be enabled as you have exceeded your license seat.
Note: The option is not available when the user type is an API user.
Comments
Optionally, enter comments about the user.
Two Factor Authentication
Email address
The email address.
Note: This option is mandatory for all authentication types.
Critical System Email Alert
Enable/disable sending critical system alerts via email.
Note: The option is disabled by default.
General Email Alert
Enable/disable sending general alerts via email.
Note: The option is disabled by default.
Two-Factor Authentication
Enable/disable using two-factor authentication.
Note: Two factor authentication is disabled by default.
Note: Two factor authentication is not available for an API user.
You can also set up Two Factor Authentication using CLI. See Two Factor Authentication using CLI.
Specify the type of user authentication used:
FortiToken
FortiToken Cloud. See 2FA with FortiToken Cloud example.
Email (default)

SMS based two factor authentication is not supported in FortiPAM 1.3.0.
Token
From the dropdown, select a token.
Note: The option is mandatory and only available when the Authentication Type is FortiToken.
Configure Trusted Hosts
IPv4 Trusted Hosts
Trusted IPv4 addresses users use to connect to FortiPAM.

Use + button to add a new IPv4 address and x to delete an added IPv4 address.
Configure the schedule for which the user can connect to the FortiPAM
Enable/disable configuring the login schedule for the users.
From the dropdown, select a schedule. See Schedule.
Note: This option is disabled by default.
- In the Review tab, verify the information you entered and click Submit to create the user.

Use the pen icon to edit tabs.
|
|
Alternatively, use the CLI commands to create users. |
To regenerate the API key:
- Go to User Management > User List.
- Select the API user whose API key you intend to change and then select Edit.
- In the Details pane, select Re-generate API Key.
- In the Re-generate API Key window, select Generate.

Regenerating the API key will immediately revoke access for any API consumers using the current key.
A new API key for the API user is generated.
- Click Close.
CLI configuration to set up a local user example:
config system admin
edit <user_name>
set accprofile <role_name>
set password <password>
next
end
CLI configuration to set up a remote LDAP user example:
config system admin
edit <ldap_username>
set remote-auth enable
set accprofile <profname>
set remote-group <ldap_group_name>
next
end
CLI configuration to set up a remote RADIUS user example:
config system admin
edit <radius_username>
set remote-auth enable
set accprofile <profname>
set remote-group <radius_group_name>
next
end
CLI configuration to enable two-factor authentication example:
config system admin
edit <username>
set password "myPassword"
set two-factor <fortitoken | fortitoken-cloud | email>
set fortitoken <serial_number>
set email-to "username@example.com"
next
end

