Testing SSO configuration from FortiSASE
From FortiSASE, you can test the single sign on (SSO) configuration settings end-to-end by logging into a user account configured on your SSO server. This feature allows you to open a popup test window that points to the SSO login page.
This test provides SSO configuration test results and raw log output of SAML debug from the security PoP that can help you troubleshoot issues with any misconfigured SSO configuration settings.
|
|
When using the Chrome web browser for testing SSO configuration, you must disable TLS 1.3 hybridized Kyber support via chrome://flags for this test to work. |
|
|
Testing SSO configuration from FortiSASE supports FortiClient agent-based mode using Microsoft Entra ID SSO or Okta SSO via Configuration > VPN User SSO. |
|
|
The example below is for testing an Entra ID SSO configuration and demonstrates general steps that also apply to Okta SSO. |
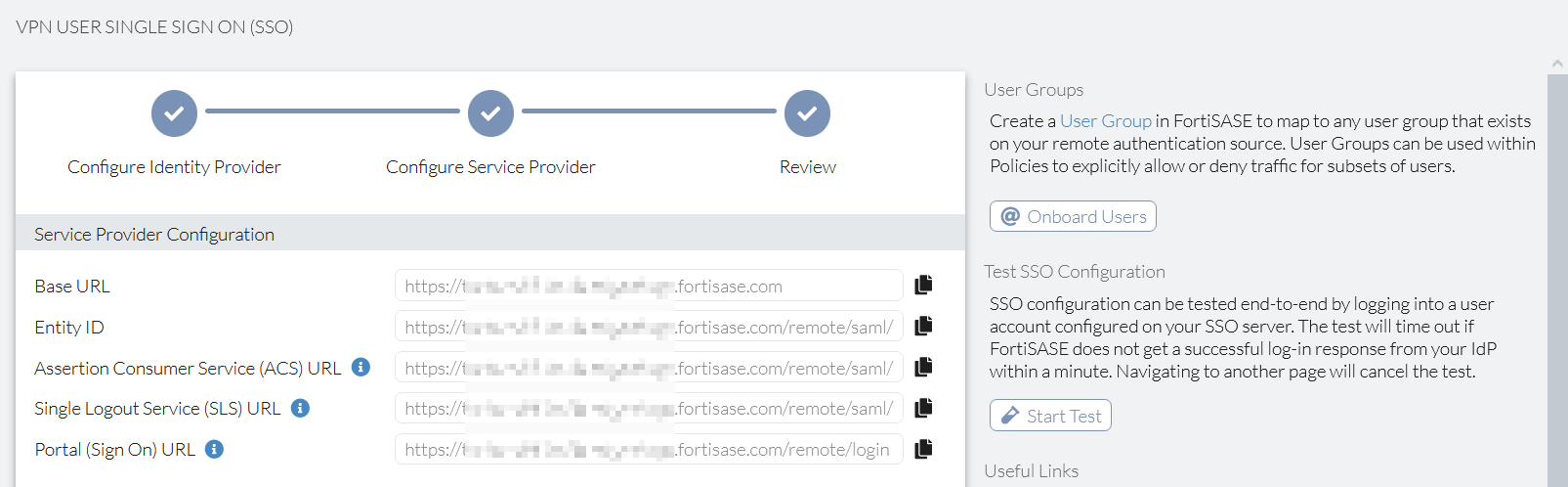
To test SSO configuration from FortiSASE using Entra ID SSO:
- Go to Configuration > VPN User SSO. Ensure that you configured Entra ID SSO and that you clicked Submit at the end of the configuration steps. For details, see Configuring FortiSASE with Entra ID SSO in FortiClient agent-based mode.
- In right-hand gutter, click Start Test.

Ensure that you disable or exempt any web browser popup blockers to allow popups for the Configuration > VPN User SSO page prior to clicking Start Test. Otherwise, you see the error message Failed to trigger SSO configuration test and the test SSO configuration feature does not work as desired.

Ensure that the web browser remains on the Configuration > VPN User SSO page for the test duration. Going to another page cancels the test.
- A popup from the SSO provider prompts for login information. This is the user account that has already been set up on the SSO server that you want to use for the test. When prompted, enter the username and password of the user account to use for the test.

Ensure that you enter the username and password of the user account within one minute. The test times out if FortiSASE does not get a successful login response within a minute with the error message SSO configuration test timed out.
- You see that the notification SSO configuration verified successfully displays in the right-hand gutter when the SAML connection test succeeds. If the test fails, one of the following error messages displays:
- Failed to trigger SSO configuration test.
- SSO configuration test timed out.
- Within one minute of starting the test, the SSO Configuration Test Output slide-in window appears.
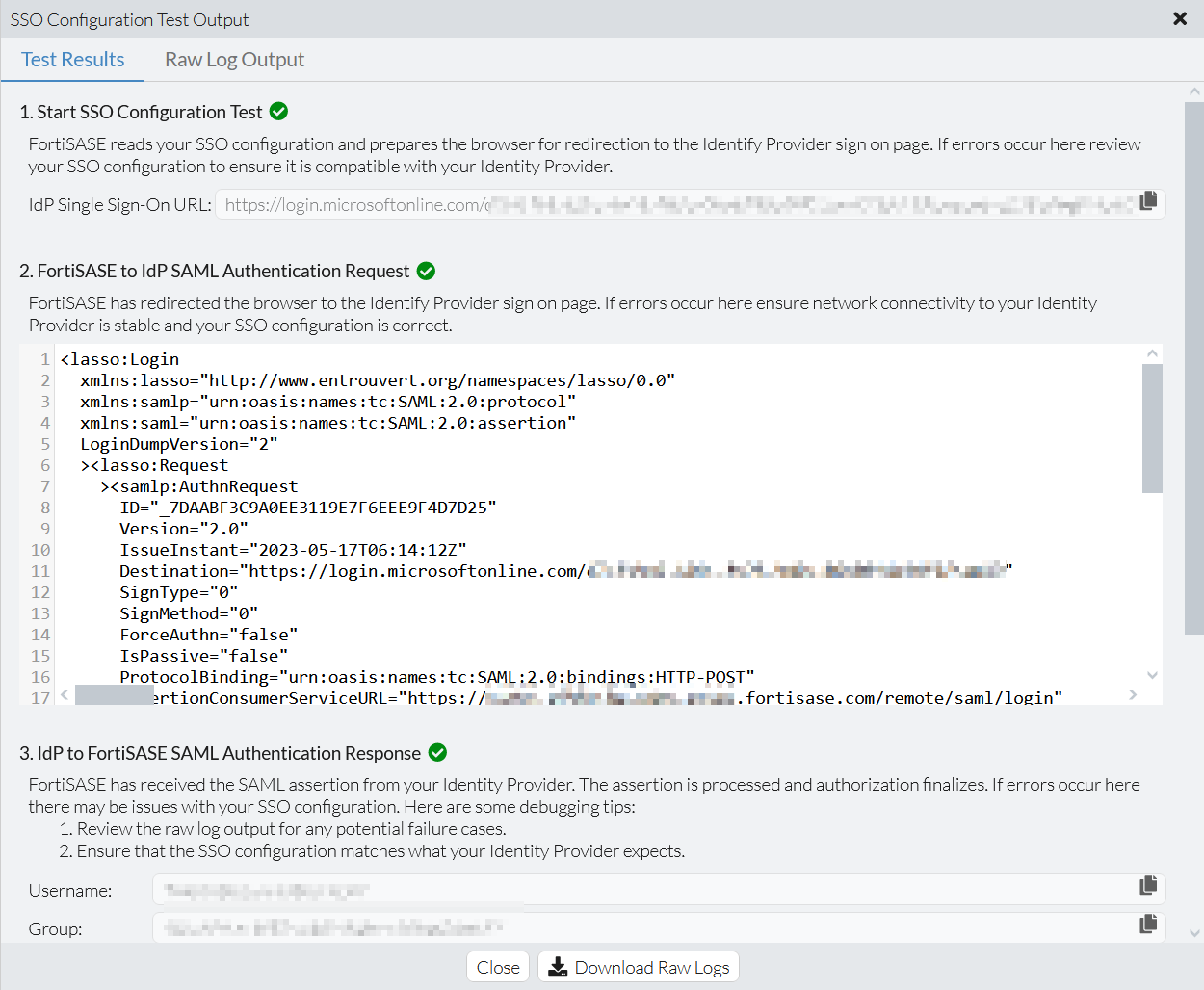
- In the Test Results tab, you see the corresponding icons that help you to narrow down your SAML troubleshooting steps:
- Green checkmark next to test steps that succeeded
- Red X next to test steps that failed, which suggests issues with the SSO configuration. The window displays debugging/troubleshooting steps when this occurs.
The following shows an example Test Results tab with successful test steps.
The following shows an example Test Results tab with a failed test step that an identity provider entity ID misconfiguration caused.

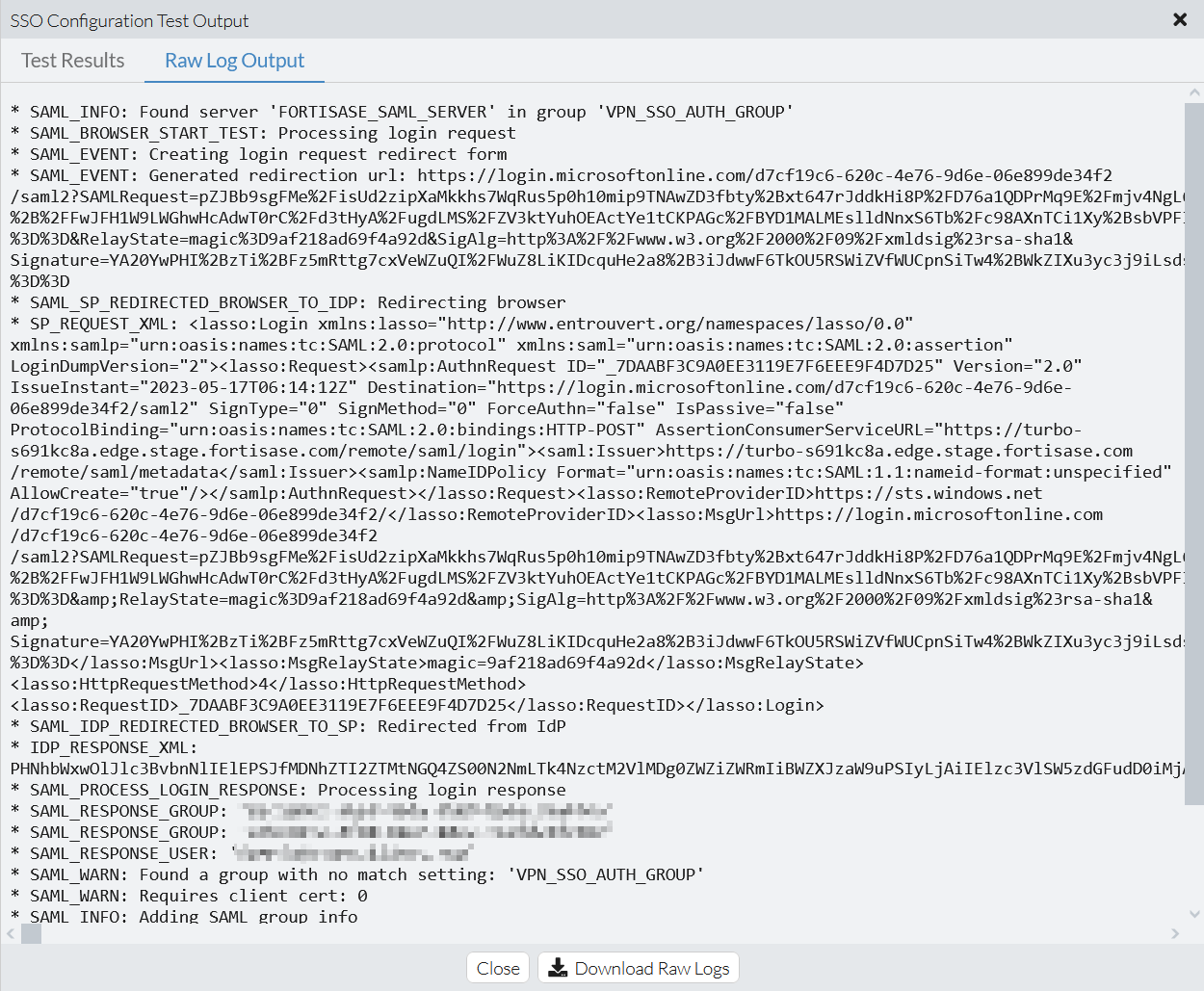
In the Raw Log Output tab, observe the SAML debug raw log output from the security point of presence with sensitive information removed. The following shows an example of the Raw Log Output tab with successful test steps.
The following shows an example Raw Log Output tab with a failed test step that an identity provider entity ID misconfiguration caused.
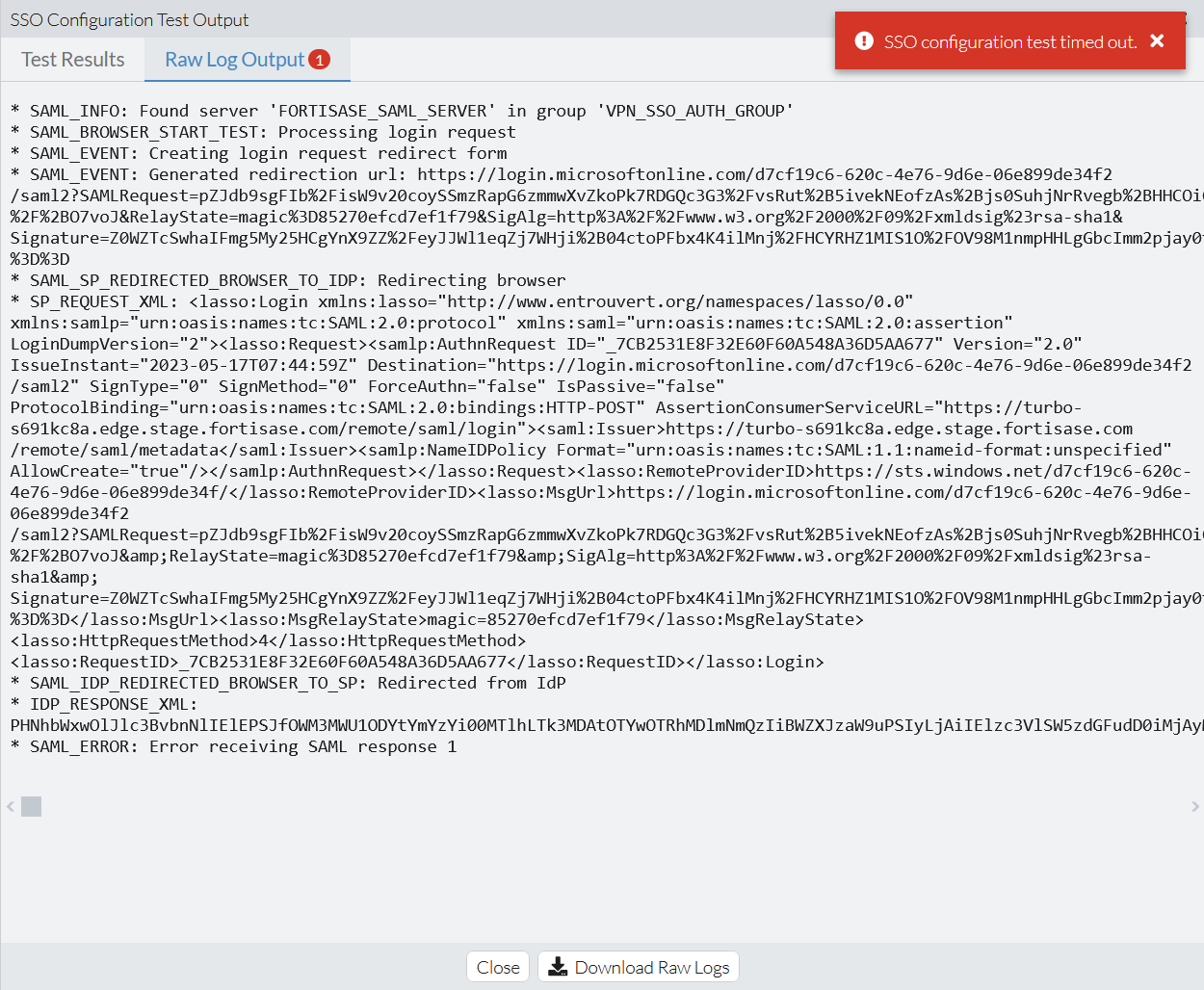
Notice the number next to the Raw Log Output tab title indicating the number of error messages in the output. See the SAML_ERROR: Error receiving SAML response 1 as the last line of the output.
- In the Test Results tab, you see the corresponding icons that help you to narrow down your SAML troubleshooting steps:

