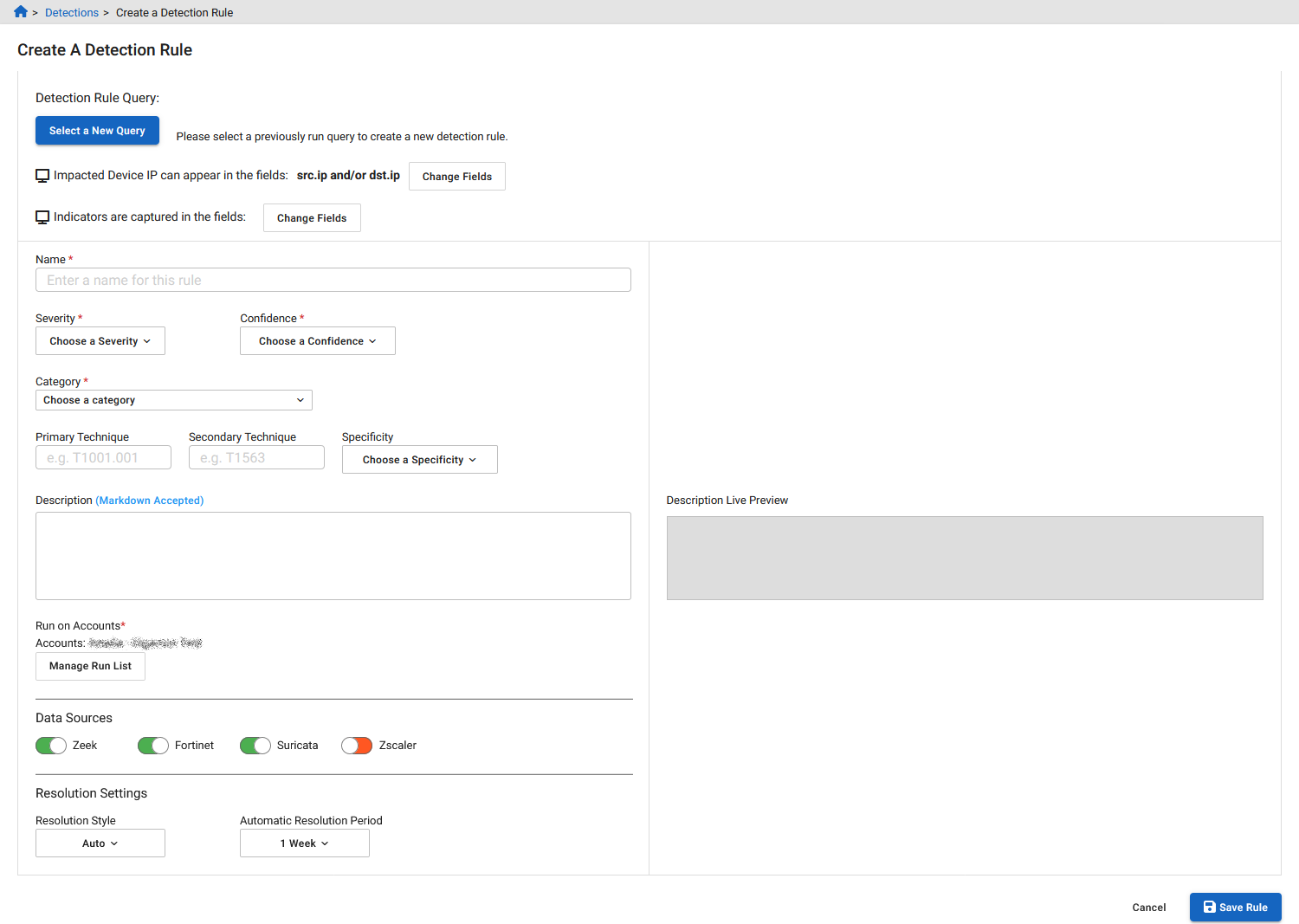
Creating a rule
Create rules to monitor suspicious behavior on the network. You can create and store up to 50 detection rules per account. An error message appears when you reach the limit. We recommend reviewing your rules on a regular bases to ensure they are still in use. Consider deleting rules that are no longer in use. To increase the rule limit for an account, contact Customer Support.
|
|
Before you create a rule, consider using a rule filter to customize a rule created by Fortinet. Rule filters save time creating a new rule and help manage the number of rules in your account. For information, see Adding custom filters to a rule signature. |
To create a rule:
- Click the Detections tab.
- In the toolbar at the top-right of the page, click the shield icon. The Create A Detection Rule page opens.

-
Click Select New Query. The Select a New Query dialog opens.
-
Click the Saved Queries or Query History tabs to create the new rule. Optionally, you can enter key words in the Search for Query field to search for a query.
-
Choose a query from the list and click Select. To select an adhoc query, expand Search Timeline.

-
- Configure the rule settings and click Save Rule.
Impacted Device IP can appear in the fields Click Change Fields to select the specific fields you want to use to generate a detection. By default, any internal IP address in the src.ipordst.ipfields will be used to generate detections.Indicators are captured in the fields Click Change Fields to add or remove an Indicator Field for a rule. You can choose up to five fields. Name Enter a name for the rule. Severity Choose High, Moderate or Low. Confidence Choose High, Moderate or Low. Category Click the drop down to select a category from the list. Primary Technique Enter the Primary Technique ID. Secondary Technique Enter the Secondary Technique ID. Run on Accounts
Click Manage Run List to choose which accounts the new rule should run in.. In the dialog that opens, choose an account and click Save.
This is applicable only if you have access to multiple accounts. For example, if your organization acquired another organization, once you deploy sensors in their network, it might be easier to ingest that data into a separate account and give your team access to it. If you were to write a rule targeting specific subnets in your account, that rule wouldn't be applicable to the acquired company's network, so you would only want to deploy it in your account.
Data Sources
Enable/disable Zeek, Fortinet, Zuricata, or Zscaler.
Resolution Style
Select Auto or Manual.
Automatic Resolution Period
Select 6 hours to 1 Month.