Policy matching using applications
Starting from 7.4.2, you can use applications as filters in policies without requiring web filter or application control profiles. If the traffic is allowed by the policy, packets are sent to the IPS engine for application match, and then, if enabled, UTM inspection (antivirus, IPS, DLP, and email filter) is performed.
Compared with the previous mechanism of filtering applications using ports and source/destination IPs in a policy, the new application filter automatically determines the application’s identity, regardless of the dynamic port or IP change, which improves your security posture.
|
|
Inline IPS is required to use this feature. To verify that inline IPS is enabled, run the |
To configure an SSL Inspection & Authentication policy for Facebook and Gmail access in the CLI:
config firewall policy
edit 2
set uuid 08c7b0c6-bfc2-51ee-17b8-078effe835eb
set srcintf "port2"
set dstintf "port1"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
set utm-status enable
set logtraffic all
set logtraffic-start enable
set log-http-transaction all
set extended-log enable
set application 15832
set ssl-ssh-profile "deep-inspection"
set av-profile "g-default"
set webfilter-profile "monitor-all"
set application-list "AP"
next
end
Logs
Traffic logs:
d1: date=2024-02-29 time=13:42:15 eventtime=1709242935321868122 tz="-0800" logid="0000000015" type="traffic" subtype="forward" level="notice" vd="root" srcip=10.100.1.55 srcport=40338 srcintf="port2" srcintfrole="undefined" dstip=157.240.241.35 dstport=443 dstintf="port1" dstintfrole="undefined" srccountry="Reserved" dstcountry="United States" sessionid=1695777498 proto=6 action="start" policyid=2 policytype="policy" poluuid="08c7b0c6-bfc2-51ee-17b8-078effe835eb" service="HTTPS" trandisp="noop" url="https://www.facebook.com/" agent="curl/7.81.0" appid=15832 app="Facebook" appcat="Social.Media" apprisk="medium" duration=0 sentbyte=0 rcvdbyte=0 sentpkt=0 rcvdpkt=0
Web filter log:
1: date=2024-02-29 time=13:42:15 eventtime=1709242935322088194 tz="-0800" logid="0317013312" type="utm" subtype="webfilter" eventtype="ftgd_allow" level="notice" vd="root" policyid=2 poluuid="08c7b0c6-bfc2-51ee-17b8-078effe835eb" policytype="policy" sessionid=1695777498 transid=117440514 srcip=10.100.1.55 srcport=40338 srccountry="Reserved" srcintf="port2" srcintfrole="undefined" srcuuid="6a168214-f8e3-51ec-9294-1673e0a41d9e" dstip=157.240.241.35 dstport=443 dstcountry="United States" dstintf="port1" dstintfrole="undefined" proto=6 httpmethod="GET" service="HTTPS" hostname="www.facebook.com" agent="curl/7.81.0" profile="monitor-all" action="passthrough" reqtype="direct" url="https://www.facebook.com/" sentbyte=774 rcvdbyte=3243 direction="outgoing" msg="URL belongs to an allowed category in policy" ratemethod="domain" cat=37 catdesc="Social Networking"
Application control log:
1: date=2024-02-29 time=13:42:15 eventtime=1709242935609343887 tz="-0800" logid="1059028704" type="utm" subtype="app-ctrl" eventtype="signature" level="information" vd="root" appid=15832 srcip=10.100.1.55 srccountry="Reserved" dstip=157.240.241.35 dstcountry="United States" srcport=40338 dstport=443 srcintf="port2" srcintfrole="undefined" dstintf="port1" dstintfrole="undefined" proto=6 service="HTTPS" direction="incoming" policyid=2 poluuid="08c7b0c6-bfc2-51ee-17b8-078effe835eb" policytype="policy" sessionid=1695777498 applist="AP" action="pass" appcat="Social.Media" app="Facebook" hostname="www.facebook.com" incidentserialno=1278682 url="/" agent="curl/7.81.0" httpmethod="GET" msg="Social.Media: Facebook" apprisk="medium"
Setting application default port as a service port
The default-app-port-as-service option can be used to set the application default port as a service port. This allows applications to match the policy and traffic from the application that does not match the default port is be blocked immediately the first time that traffic hits the firewall. When this option is enabled, the policy aggregates the ports used by the applications in the policy and performs a pre-match on the traffic.
config system settings
set default-app-port-as-service {enable | disable}
end
|
|
This option can be configured on a per-VDOM level. |
This setting is enabled by default on new installations. When upgrading, the setting is disabled to retain the previous behavior.
Example
In the following example, the policy is configured to match traffic from the YouTube application:
config firewall policy
edit 2
set uuid 08c7b0c6-bfc2-51ee-17b8-078effe835eb
set srcintf "port2"
set dstintf "port1"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
set utm-status enable
set logtraffic all
set logtraffic-start enable
set log-http-transaction all
set extended-log enable
set application 31077
set ssl-ssh-profile "deep-inspection"
set av-profile "g-default"
set webfilter-profile "monitor-all"
set application-list "AP"
next
end
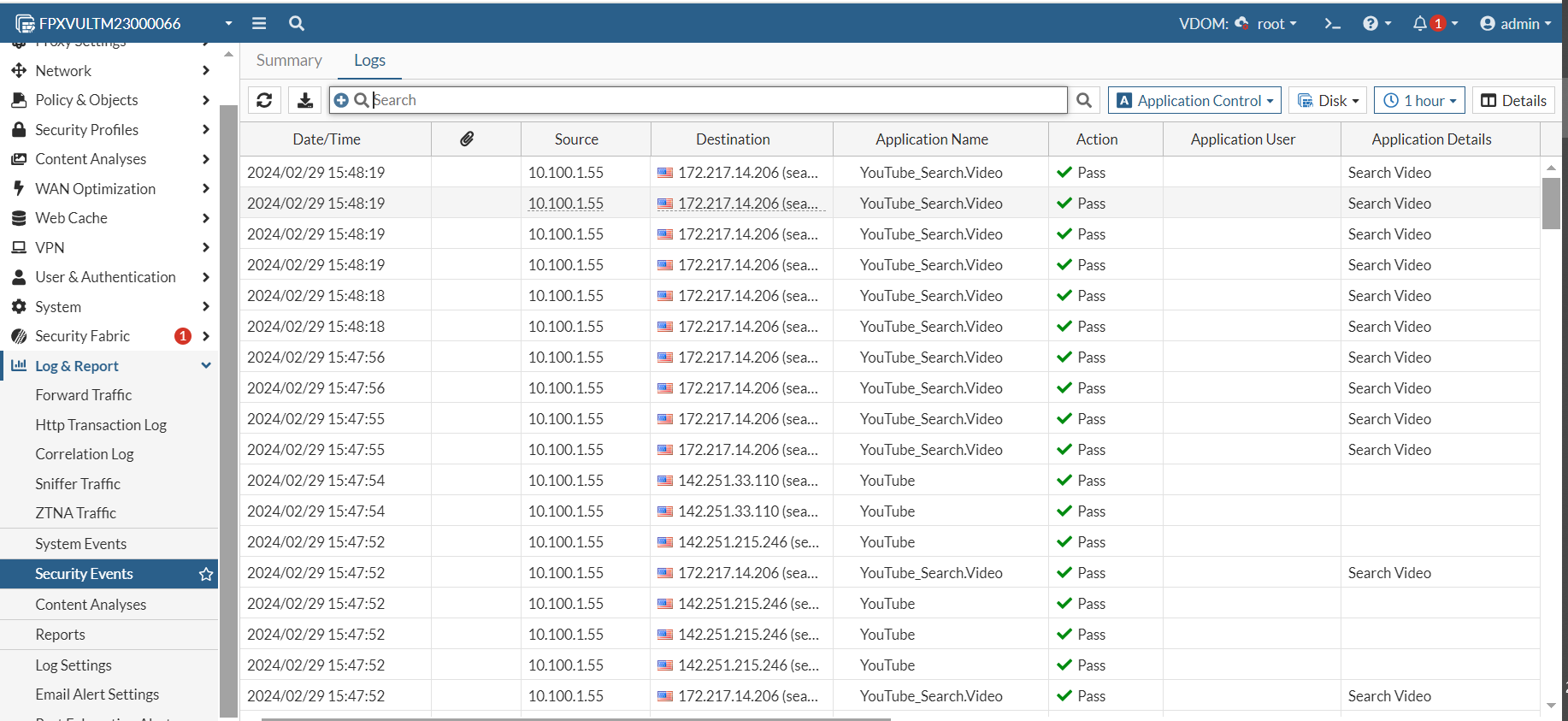
When traffic logging is set to UTM or All, then application control logs will be generated. To verify application logging, play some YouTube videos on a client system and then go to Log & Report > Security Events to view the Application Control logs.
When the default-app-port-as-service option is enabled, the traffic which does not match the default port is blocked immediately and only traffic log is generated. There are only logs for YouTube, as verified from the Application Name column:
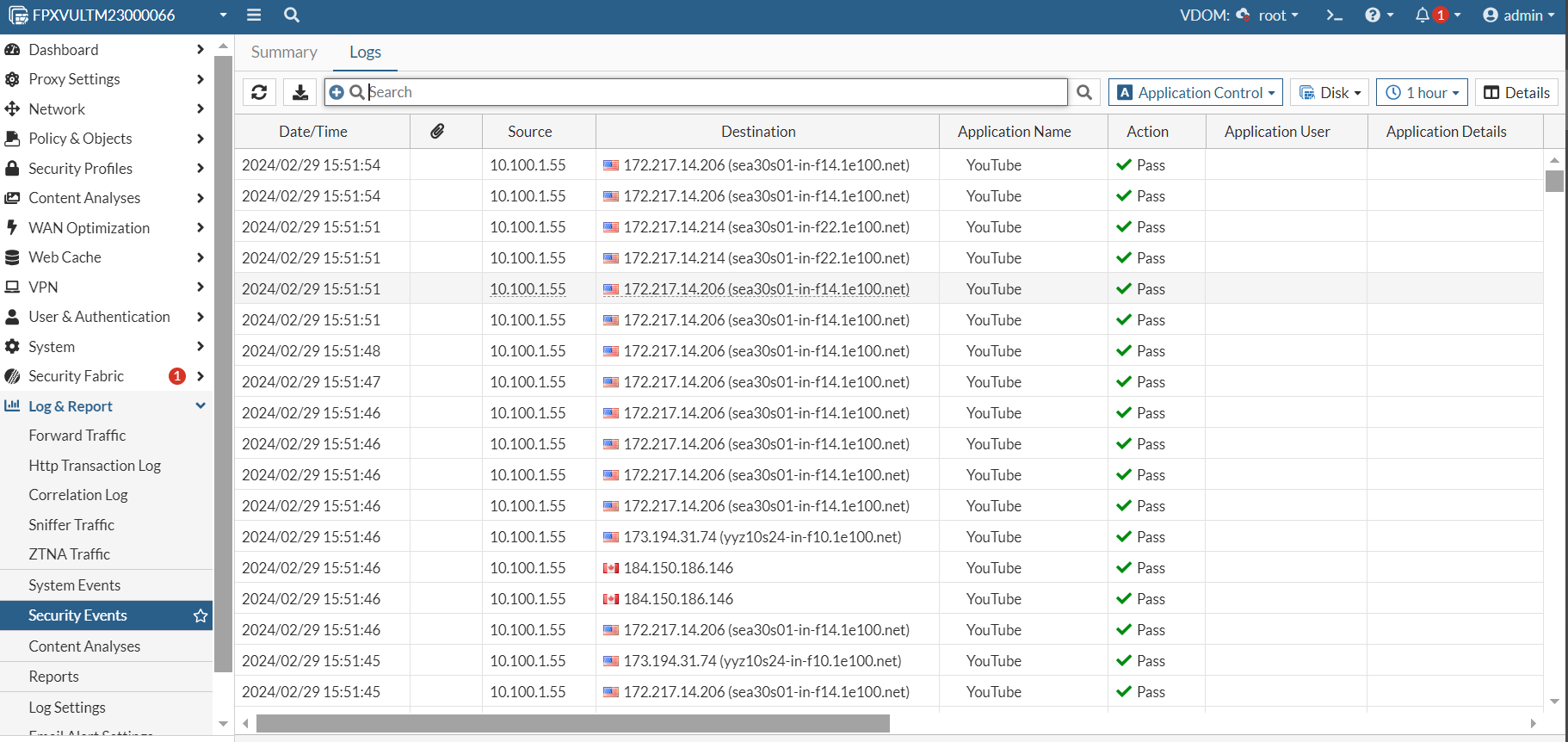
When the default-app-port-as-service option is disabled, the traffic which does not match the default port is not be blocked and both application and traffic logs are generated. There are logs for YouTube and YouTube_search.video, as verified from the Application Name column: