Decrypted Traffic Mirror
SSL mirroring allows the FortiProxy unit to decrypt and mirror traffic to a designated port. A decrypted traffic mirror profile can be applied to explicit, transparent, SSH tunnel, and SSH proxy policies when the custom-deep-inspection, deep-inspection, or deep-test SSL/SSH inspection security profile is selected. SSL inspection is automatically enabled when you enable a security profile on the policy configuration page.
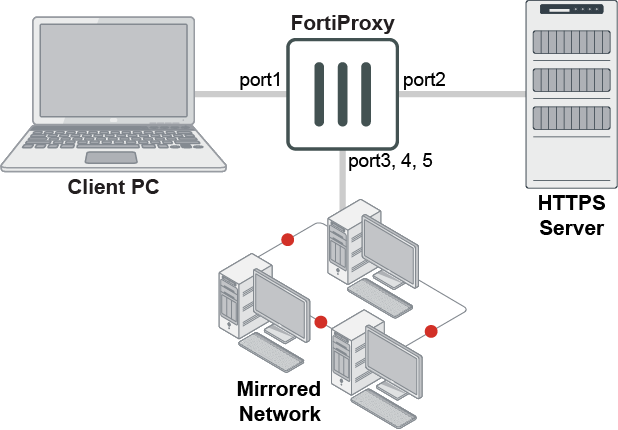
To configure SSL mirroring in a policy:
- Create a decrypted traffic mirror profile by selecting Create New under Policy & Objects > Dycrypted Traffic Mirror in the GUI. Configure the following options:
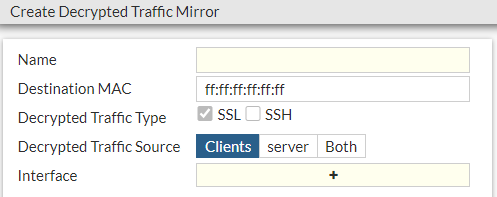
Name Enter the name of the decrypted traffic mirror profile. Destination MAC Enter the destination MAC address for the mirrored traffic. Decrypted Traffic Type Select whether decrypted SSL traffic, decrypted SSH traffic, or both are mirrored. Decrypted Traffic Source Select whether decrypted client-side traffic, decrypted server-side traffic, or both are mirrored. Interface Select which interfaces will have decrypted traffic mirrored.
Fortinet recommends that you mirror the traffic to a dedicated interface or virtual interface.
API Preview The API Preview allows you to view all REST API requests being used by the page. You can make changes on the page that are reflected in the API request preview. This feature is not available if the user is logged in as an administrator that has read-only GUI permissions. Alternatively, use the
config firewall decrypted-traffic-mirrorcommand. For example:config firewall decrypted-traffic-mirror
edit "1"
set dstmac ff:ff:ff:ff:ff:ff
set traffic-type ssl ssh
set traffic-source both
set interface "port1"
next
end
- Configure the policy to enable SSL traffic mirroring:
config firewall policy
edit 1
set type explicit-web
set name "All"
set uuid 10e62d76-7c94-51ee-fa3a-ae92170cea18
set dstintf "port1"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "webproxy"
set explicit-web-proxy "web-proxy"
set utm-status enable
set logtraffic all
set log-http-transaction all
set decrypted-traffic-mirror "Decrypt"
set ssl-ssh-profile "Deep_Custom".
set webfilter-profile "default"
next
end
To verify and troubleshoot issues with traffic mirroring, use the Network > Diagnostics tab to capture and analyze the mirrored traffic.

