Optimizing the FortiSwitch network
Starting in FortiOS 6.4.2 with FortiSwitchOS 6.4.2, you can check your FortiSwitch network and get recommendations on how to optimize it. If you agree with the configuration recommendations, you can accept them, and they are automatically applied. The following tests have been added:
-
Managed Switch Capacity Exceeded on FortiGate
This test checks for the number of FortiSwitch units managed by the downstream FortiGate devices that have exceeded 80% of the limit. The score is calculated individually and then averaged out. If the number of connected FortiSwitch units is equal or greater than the maximum limit, then the result is a fail.
You can upgrade to higher capacity FortiGate devices or add more FortiGate devices to the Security Fabric so the FortiSwitch units can be split between multiple FortiGate devices.
In the following example, the downstream FortiGate device passed.

-
Redundant FortiLinks
This test checks for redundant FortiLinks between the FortiGate device and the FortiSwitch unit. There are multiple ports dedicated to FortiLink on FortiSwitch units directly connected to FortiGate devices. FortiSwitch units that are not directly connected to the FortiGate device are exempt from this test. If there are no redundant FortiLinks, then the result is a fail.
In the following example, the FortiGate device failed. The Recommendations section lists which FortiSwitch units require redundant FortiLinks.

-
Redundant ISL
For FortiSwitch units with inter-switch links (ISLs), this test checks for two redundant links. If there is only one link, then the result is a fail. The Recommendations section lists which devices require an additional link. FortiSwitch units with inter-chassis links (ICLs) are exempt from the test.
In the following example, the devices passed.

-
Enable MCLAG
This test checks for candidate FortiSwitch units that can form a tier-1 MCLAG. To do this, the FortiSwitch units must be connected to each other and directly connected to the FortiGate device. The FortiSwitch unit must support MCLAG. If an MCLAG already exists, this check is skipped.
In the following example, three devices passed the test and two devices were exempt.

-
Lockdown LLDP Profile
This test ensures that there are no accidental changes to the topology. For edge ports (not FortiLink or ISL), FortiOS suggests using the default LLDP profile. The test verifies the following:
- Looks for an edge port that has an auto-ISL LLDP profile
- Checks if the edge port BPDU guard is disabled
- Check if the FortiGate DHCP server and switches do not have a DHCP key
In the following example, the devices failed. The EZ (Easy Apply) symbol appears, and port configurations to optimize the Security Fabric can be applied in the Recommendations section.

-
Enable STP
This test checks if STP is enabled on edge ports. After the network topology is stable, edge ports should have STP enabled to optimize the Security Fabric. In the following example, the devices passed.
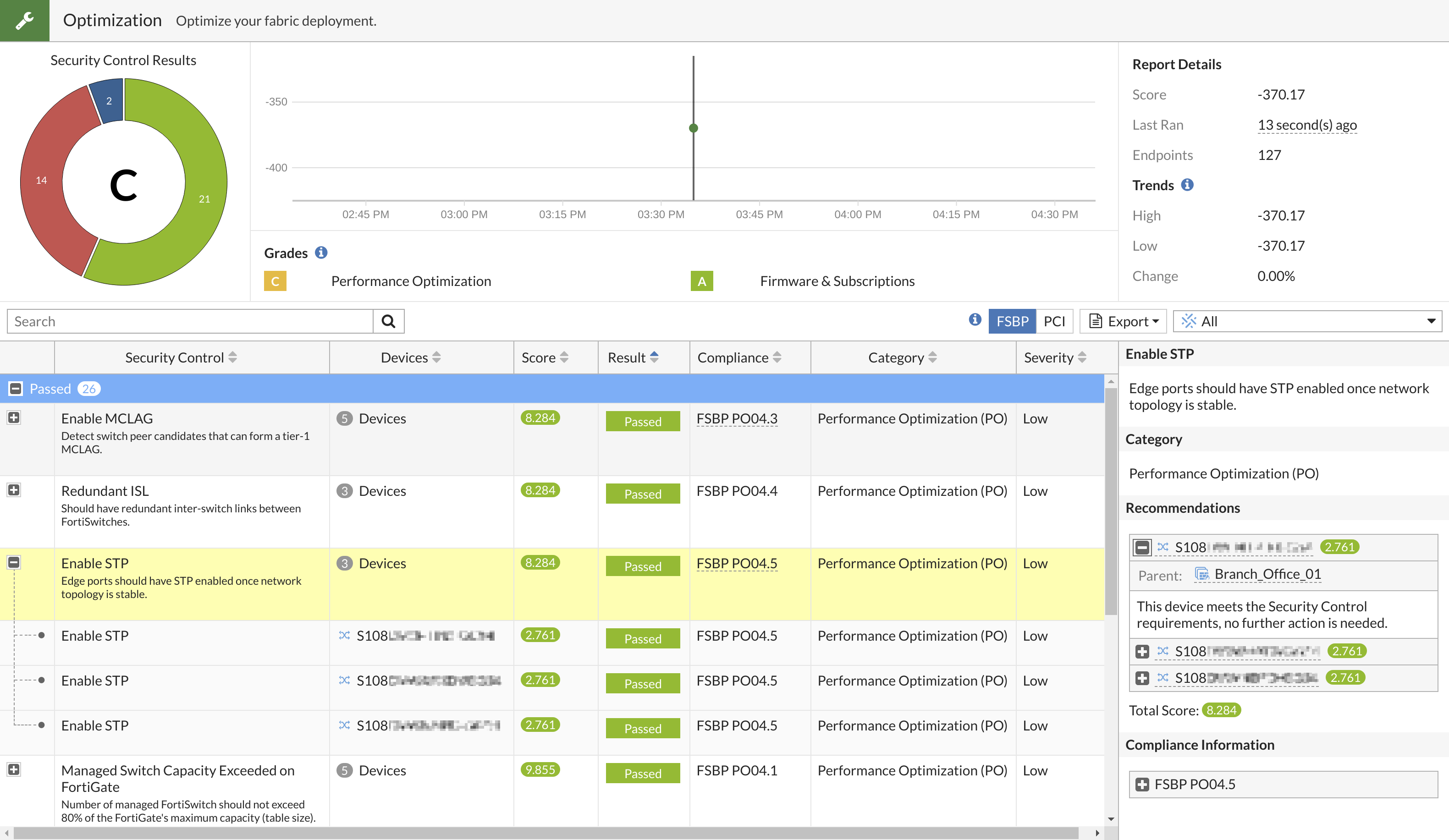
In FortiOS 7.2.4 with FortiSwitchOS 7.2.3, more tests have been added to the FortiSwitch recommendations to help optimize your network:
- If port 8 of an FS-108E or FS-108 unit is used for an inter-switch link (ISL), FortiOS recommends creating a custom auto-config policy.
- If the configured speed is less than the maximum speed for a switch port, FortiOS recommends changing the port speed to the maximum amount.
-
FortiOS checks if the ISLs and inter-chassis links (ICLs) are static to increase stability during events such as cable disconnections or power outages. If any ISLs or ICLs are not static, FortiOS recommends locking down the Security Fabric topology to prevent the automatically created ISLs and ICLs from being accidentally deleted.
In the following figure, two ISL configurations need to be locked down.

-
When a multichassis link-aggregation group (MCLAG) is recommended between two FortiSwitch units, there is a Create MCLAG button available under WiFi & Switch Controller > Managed FortiSwitches in the Topology view.
In FortiOS 7.4.0 with FortiSwitchOS 7.4.0, more tests have been added to the FortiSwitch recommendations to help optimize your network:
-
Check if the switch port where a quarantined device was last seen has bouncing enabled.
-
Check if the Basic Input/Output System (BIOS) on the FortiSwitch unit needs to be upgraded before FortiSwitchOS can be upgraded.
-
If the
poe-statushas been enabled under theconfig switch-controller auto-config policycommand, FortiOS recommends that you disable it to prevent unpredictable problems caused by connecting two power sourcing equipment (PSE) ports.
In FortiOS 7.4.1 with FortiSwitchOS 7.4.1, more tests have been added to the FortiSwitch recommendations to help optimize your network:
-
When a connected tier-1 MCLAG peer group is detected and FortiOS detects a possible tier-2 MCLAG pair of switches, FortiOS recommends forming a tier-2 MCLAG.
After you accept the recommendation, the
set lldp-profile default-auto-mclag-iclcommand is configured on the two switches with the recommended interchassis link (ICL) ports, and theconfig switch auto-isl-port-groupcommand is configured on the parent MCLAG peer group. -
When a connected tier-2 MCLAG peer group is detected and FortiOS detects a possible tier-3 MCLAG pair of switches, FortiOS recommends forming a tier-3 MCLAG.
After you accept the recommendation, the
set lldp-profile default-auto-mclag-iclcommand is configured on the two switches with the recommended ICL ports, and theconfig switch auto-isl-port-groupcommand is configured on the parent MCLAG peer group.
NOTE: For detection to be successful, there must be fully meshed connection (each tier-2 FortiSwitcch unit must have a connection to each tier-1 FortiSwitch unit; each tier-3 FortiSwitch unit must have a connection to each tier-2 FortiSwitch unit.
NOTE: The Security Rating feature is available only when VDOMs are disabled.
To optimize your FortiSwitch network:
- Go to Security Fabric > Security Rating.
- Select Run Now (under Report Details in the right pane) to generate the Security Rating report.

- Select the Optimization section.

- Under Failed, select + next to each item to see more details in the right pane.

- If you agree with a suggestion in the Recommendations section, select Apply for the change to be made.

|
|
After accepting a recommended change to the network, you must go to Security Fabric > Security Rating and click Run Now again after the network change is made to update the recommendations based on the new network topology. |
Example
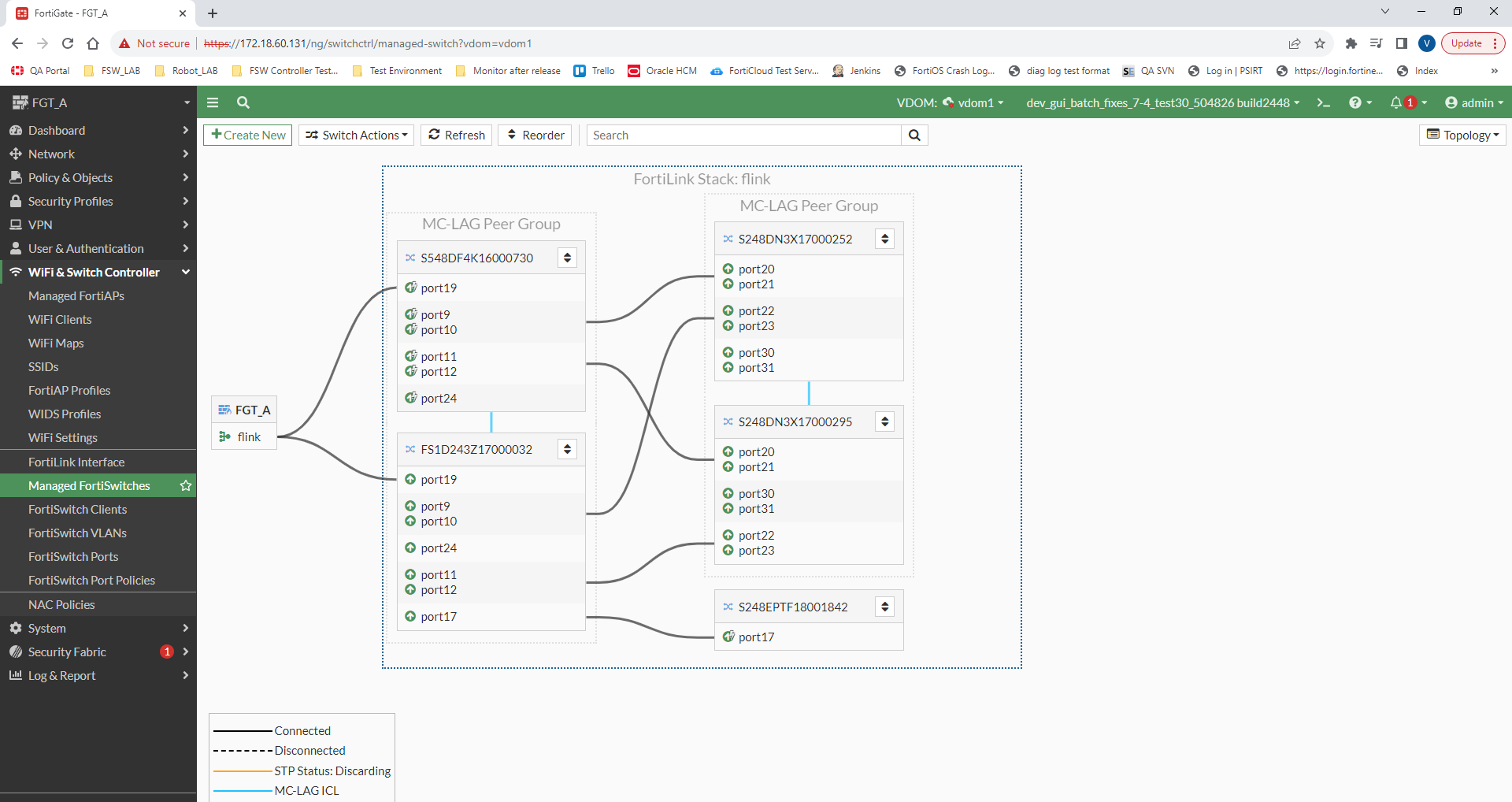
In this example, a FortiGate device manages four FortiSwitch units. Two of the switches already form an MCLAG, and the user wants a second MCLAG tier for redundancy.

-
In the FortiOS GUI, go to WiFi & Switch Controller > Managed FortiSwitches and verify that the two tier-2 FortiSwitch units are the same model so that they can form an MCLAG.
-
Go to Security Fabric > Security Rating and click Run Now.

-
After the security rating report has run, expand the Optimization results to see Enable MC-LAG Tier 2/3.

-
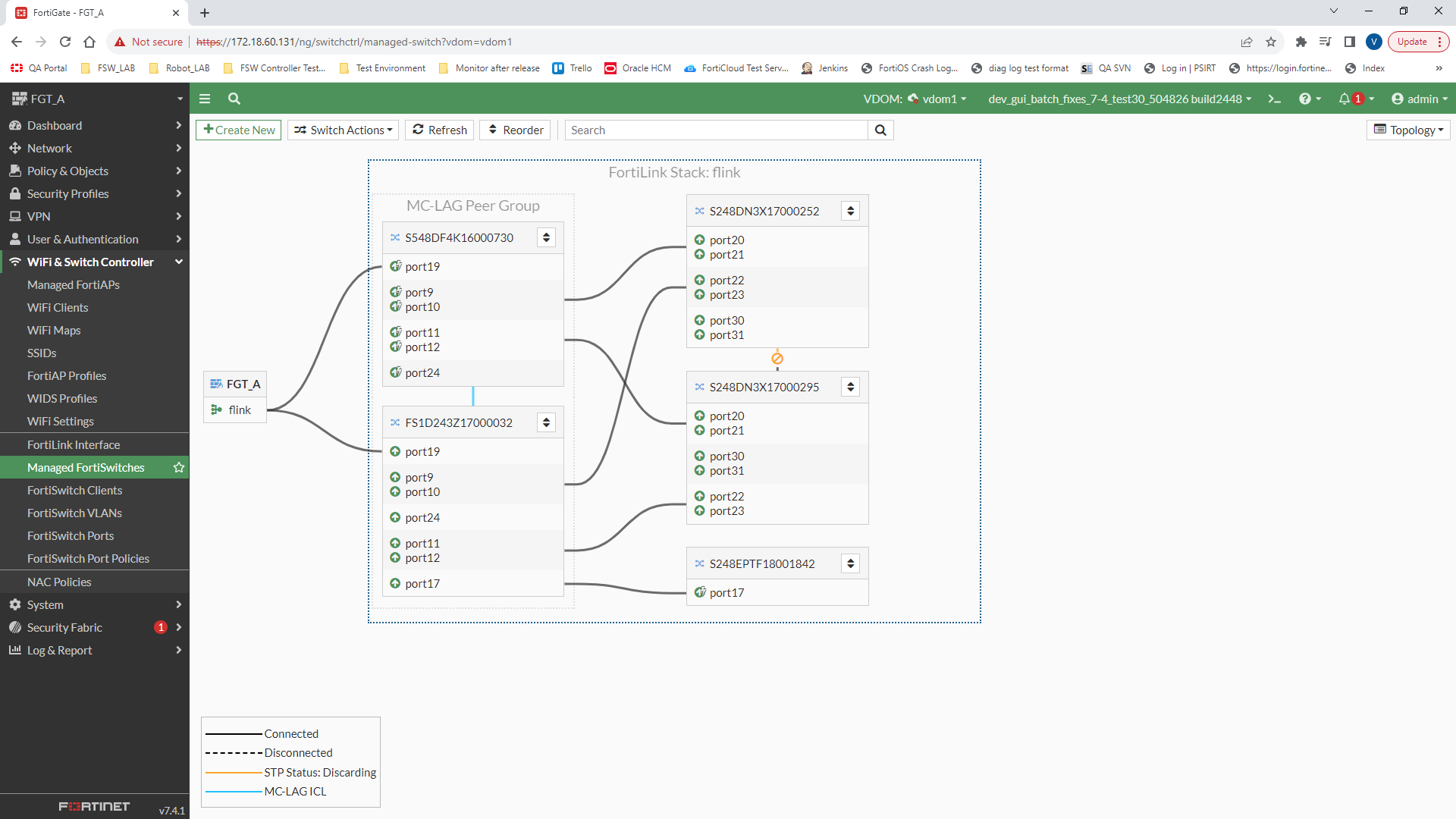
Go to WiFi & Switch Controller > Managed FortiSwitches and hover over the link connecting the two tier-2 FortiSwitch units. Click Create MC-LAG pair.

-
In the Create MC-LAG Pair panel, enter the ISL port group name.

-
The Managed FortiSwitches page shows that the MCLAG is formed for the tier-2 managed FortiSwitch units.