Deploying FortiClient with Workspace ONE
You can deploy FortiClient on macOS devices silently without any user interaction by using Workspace ONE mobile device management (MDM). You can deploy FortiClient by deploying and executing a shell script through Workspace ONE mobile device management, making macOS devices download the FortiClient installer from a repository (the EMS server), installing FortiClient, and registering to EMS.
|
|
This documentation is based on deploying a FortiClient 7.0.6 installer created in EMS 7.0.6 to a device running macOS Monterey with Apple silicon. |
Deploying FortiClient from EMS through shell scripting is recommended, as it is simple and effective. To follow this procedure, all macOS devices should meet the following prerequisites:
- Running macOS 10.15.0 or later
- Managed by Workspace ONE
- Shell scripts begin with
#!and are in a valid location, such as#!/bin/shor#!/usr/bin/env zsh. - Command line interpreters for the applicable shells are installed.
To deploy FortiClient through shell scripting:
- Modify the script file:
- Download the given FortiClient deployment sample shell script InstallFortiClient.sh file from Fortinet Services & Support > Firmware Images.
- Open the file with a text editor.
- Modify the
weburlvalue:- If using on-premise EMS, modify the
weburlvalue to your FortiClient download link from EMS. For example, you would change the value fromweburl= <"FortiClient download URL from EMS">toweburl="https://your_EMS_FQDN:10443/installers/Default/FCT_MAC_7.0.6_GA/FortiClient_7.0.6.dmg", if the download link is https://your_EMS_FQDN:10443/installers/Default/FCT_MAC_7.0.6_GA/FortiClient_7.0.6.dmg. - If using FortiClient Cloud, you must first obtain the installer URL from the invitation email that FortiClient Cloud sends to end users. Configure an invitation email as Adding a new invitation for a deployment package describes, configuring only yourself as a recipient. After receiving the invitation email, copy the installer link in the email. Replace the "FCT7.zip" at the end of the URL to "FortiClient_7.2.x.dmg", then enter this value in
weburl. For example, if the invitation email includes example.ems.forticlient.forticloud.com/installers/default/FCT7/FCT7.zip as the installer URL and the installer is for FortiClient 7.0.6, you would enterweburl="example.ems.forticlient.forticloud.com/installers/default/FCT7/FortiClient_7.2.6.dmg".
- If using on-premise EMS, modify the
- For
FortiClient_Installerversion, enter the FortiClient version and build number. For example, you would enterFortiClient_Installerversion="7060208"if you are installing FortiClient 7.0.6 build 208. - Follow the instructions that the script provides to configure feature installation as desired. For example, to enable all features installed on the endpoint, set the value to
1for all features:Field Description av="1"
To disable malware protection, enter 0.af="1"
To disable application firewall, enter 0.sb="1"
To disable advanced persistent threat components, enter 0.sra="1"
To disable secure access architecture components, enter 0.sso="1"
To disable the single sign on mobility agent, enter 0.vs="1"
To disable vulnerability scan, enter 0.wf="1"
To disable web filter, enter 0.ztna="1"
You currently cannot disable zero trust network access. - The shell script mainly performs the following tasks:
- Skip the installation process if there is FortiClient installed with same version and features.
- Continue the installation process if one of the following is true:
- There is no FortiClient installed or free VPN version installed.
- FortiClient is installed with a different version and/or different features.
- Uninstall older versions of FortiClient if there is any.
- Download the FortiClient deployment package from the EMS server. Therefore, the managed macOS device should be able to access the download link.
- Install FortiClient on the macOS device.
If desired, modify the script file based on your requirements.
Save the file. You can now upload the script to Workspace ONE.
-
Upload the script to Workspace ONE:
- In Workspace ONE, go to Devices > Provisioning > Components > Files/Actions > ADD FILES/ACTIONS.
- Select Apple macOS.
On the General tab, name the instance.
On the Files tab, click ADD FILES. Click Choose Files, and upload the InstallFortiClient.sh file. Click SAVE.
-
On the Add Files page, enter a download path for the script. For example, you may enter /tmp/. Click SAVE. Workspace ONE displays the script file in the list.
-
Add an action to execute the script:
- On the Manifest tab, under Installation Manifest, click ADD ACTION.
On the Add Manifest page, from the Action(s) To Perform dropdown list, select Execute Script.
In the Script File Path and Name field, enter the script file download path and name. For example, you may enter /tmp/InstallFortiClient.sh.
Enable Execute As Root. Click SAVE. Workspace ONE shows the configuration under Installation Manifest.
Click SAVE. Workspace ONE shows the configuration under Files/Actions.
-
Add a product for the script:
- Go to Devices > Provisioning > Product List View > ADD PRODUCT.
Select Apple macOS.
On the General tab, enter the desired file name.
From the Smart Groups dropdown list, select the desired group.
On the Manifest tab, click ADD.
From the Action(s) To Perform dropdown list, select File/Action - Install.
In the Files/Actions field, select the FortiClient deployment script. Click SAVE.
On the Deployment tab, configure the activation and deactivation dates as desired. Configure other fields as desired, then click SAVE. You have created the FortiClient deployment using the script as a product on Workspace ONE. It is now ready to deploy on enrolled devices under the assigned group.
Note the following:
- Manually uninstalling FortiClient using the FortiClient uninstaller tool removes the VPN virtual adapter and stored zero trust network access (ZTNA) certificates on the endpoint. As a result, reinstalling FortiClient displays the FortiTray VPN and system keychain modification prompts. In this case, push and distribute the MDM configuration profile again before reinstalling FortiClient to fully silence the prompts.
- When connecting to VPN with client certificates, the system prompts the user for keychain access credentials to access and read the stored certificate. The user can decide to allow or deny access. Selecting Always Allow silences future prompts when FortiTray accesses the certificate.

- When FortiClient acts as a ZTNA client, the system is expected to display prompts to ask for user credentials to access the ZTNA client certificate stored in the login keychain.

- Revoking the endpoint client certificate from EMS removes the ZTNA client certificate and the MDM preloaded CA certificate from keychain access. Therefore, when removing the revoked CA Certificate, the system prompts for administrator credentials to modify the system keychain.
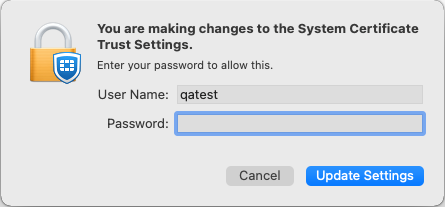
This deployment has the following limitations and issues:
- macOS displays prompts when FortiClient tries to install, update, or access an untrusted zero trust network access or VPN certificate.
- Manually uninstalling FortiClient on an endpoint with the FortiClientUninstaller tool deletes the VPN network extension in System Preferences > Network, which results in macOS displaying a prompt that FortiTray would like to add VPN configurations during future FortiClient deployments. As a workaround, the MDM administrator must push the configuration profile for FortiClient again before distributing the script on endpoints to ensure that all permissions are granted.
- The FortiClient console may fail to open and show a Javascript error prompt.
- Upgrading FortiClient to 7.0.6 may cause the following issues:
- FortiClient installation may freeze and show a prompt that the FortiTray application is not open anymore.
- Uninstalling old FortiClient versions may fail and show a prompt that the installation failed to shut down FortiClient.
-
There is an ongoing request for making the ZTNA CA certificate exportable from EMS. Therefore, the user can retrieve the CA certificate from EMS instead of from a registered endpoint.

