Configuring user verification with SAML authentication and an Azure AD server user account
The following provides an example of configuring user verification, using an Azure Active Directory (AD) server for authentication. This configuration consists of the following steps:
- The EMS administrator adds the Azure AD server to EMS.
- The EMS administrator creates a SAML configuration in EMS, with EMS as the service provider (SP) and the Azure AD server as the identity provider (IdP).
- The EMS administrator configures an invitation code, and send the invitation code to the desired user.
- The end user receives the invitation email, and uses it to download FortiClient.
- The end user connects to EMS using their Azure AD credentials.
To configure an Azure AD server in EMS:
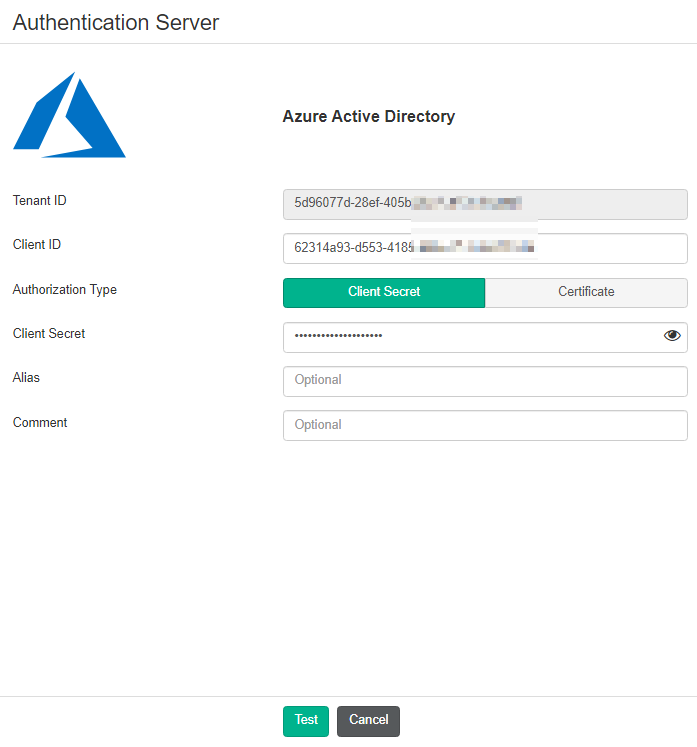
- Configure the Azure AD server as an authentication server in EMS:
- In the Azure management console, collect your AD tenant ID, client ID, and client secret.
- Go to Administration > Authentication Servers.
- Click Add > Azure.
- In the Tenant ID and Client ID fields, enter the IDs that you collected from the Azure management console.
- For Authorization Type, select Client Secret.
- In the Client Secret field, enter the client secret that you collected from the Azure management console.
- Configure other fields as desired.
- Click Test.
- After the test succeeds, click Save.
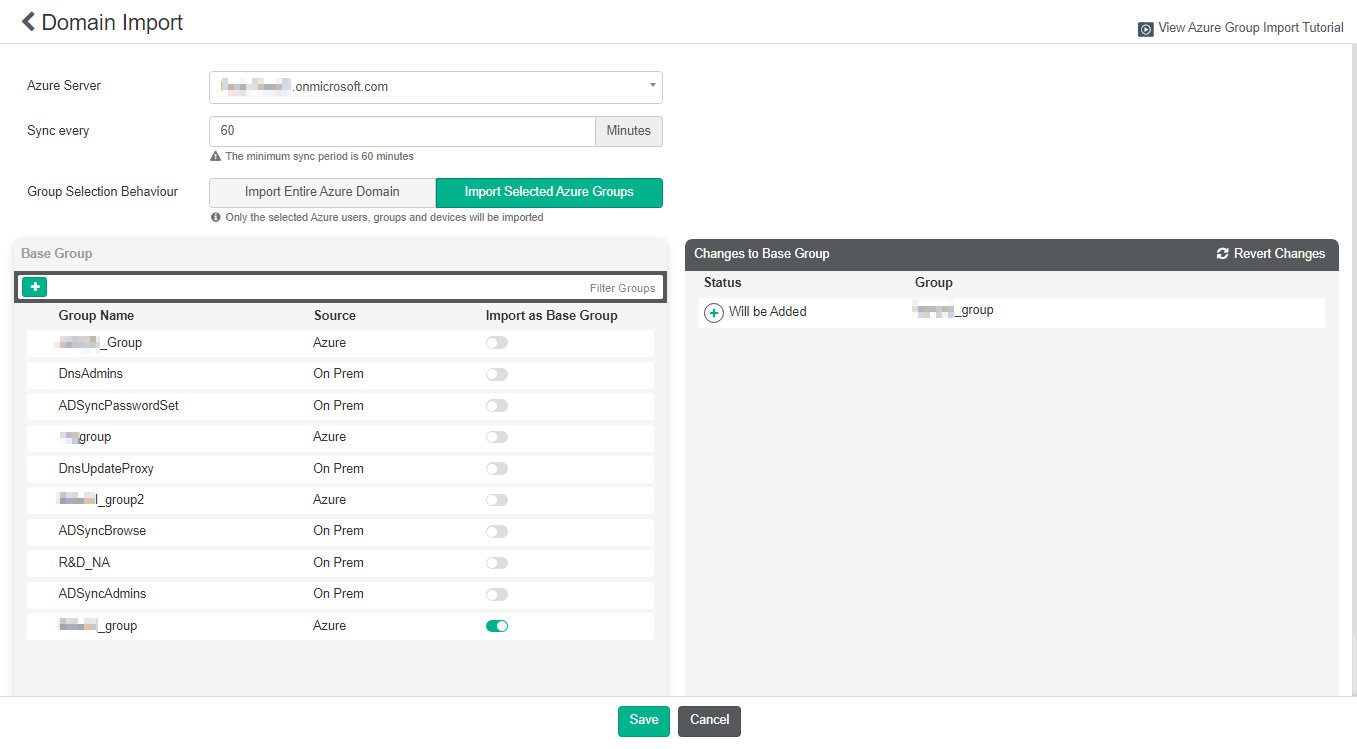
To add endpoints using an Azure AD server:
- Go to Endpoints > Manage Domains.
- Click Add, then Azure.
- From the Azure Server dropdown list, select the desired server.
- In the Sync every field, enter the number of minutes after which EMS syncs with the Azure server.
- For Group Selection Behaviour, select Import Entire Azure Domain or Import Selected Azure Groups.
- Enable Import as Base Group for the desired groups, then click Save.
Endpoints > Domains lists the Azure AD server domain groups and subgroups. It lists subgroups as a flat list and does not preserve the hierarchy from the AD server.
To register an Azure AD user's endpoint to EMS using SAML:
- Create a SAML configuration:
- In EMS, go to User Management > SAML Configuration.
- Click Add.
- For Authorization Type, select LDAP.
- From the Domain dropdown list, select the Azure AD server.
- In the SP Address field, enter the EMS IP address or FQDN. You can also use the Use Current URL button to populate the field.
- Under Identity Provider Settings, enter the Azure AD entity ID and single sign on URLs. Click Save.
- In the top banner, click Invitations.
- Click Add.
- For Verification Type, select SAML.
- From the SAML Config dropdown list, select the SAML configuration.
- Configure other settings as desired, then click Save.
- You can authenticate the endpoint using Azure AD by doing one of the following:
- To join the device to the Azure AD server, do the following:
- On the endpoint, go to Settings > Accounts.
- Under Access work or school, click Connect.
- Log in as an Azure AD user.
- In FortiClient, on the Zero Trust Telemetry tab, enter the invitation code to register to EMS. FortiClient register to EMS as the logged in Azure AD user without additional prompts.
- For a workgroup endpoint or an endpoint joined to an on-premise domain, in FortiClient, on the Zero Trust Telemetry tab, enter the invitation code to register to EMS. A Microsoft single sign on prompt displays. Enter the Azure AD user credentials to authenticate and connect FortiClient to EMS.
- To join the device to the Azure AD server, do the following: