Manually adding an application to be blocked
To manually add an application to be blocked:
- Select Add Application . The following displays:
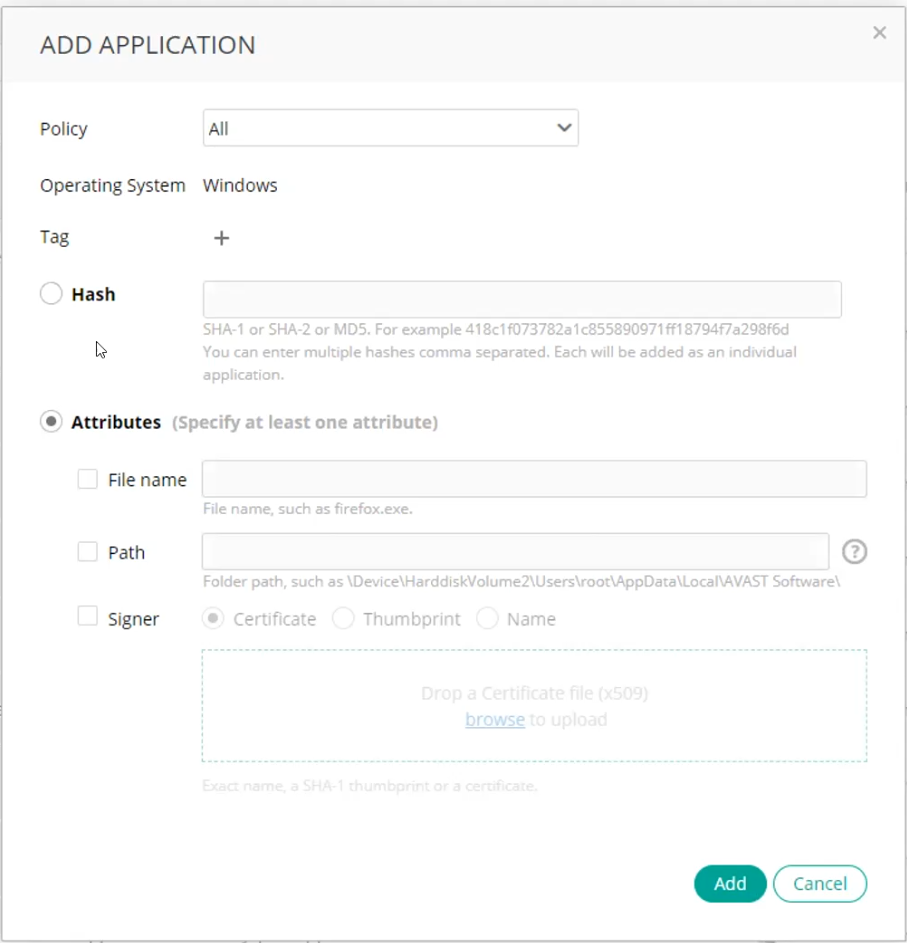
- From the Policy dropdown menu, select one or more of the Application Control policies in which to block this application or select the All option to specify that this application is to be blocked by all Application Control type policies. FortiEDR is provided out-of-the-box with a single Application Control type policy and you can clone it in order to create additional Application Control type policies as needed.
- You can optionally use the Tag field in order to classify this application. Tags can be helpful for classifying and filtering long lists of applications. In the Tag field, click the Add button
 to specify the tag to be added to the application. You can assign a previously defined tag or define a new tag.
to specify the tag to be added to the application. You can assign a previously defined tag or define a new tag.
- Define the application(s) to be blocked (so that they are not executed) using one of the following options: Hash or any combination of File Name / Path / Signer, as follows:

FortiEDR blocks only executables and DLLs that meet the defined criteria. When determining whether a file is an executable, DLL, or another type, FortiEDR adheres to the file nature rather than the file name (such as the
.exeextension).- Hash: Mark the Hash radio button and specify one or more Hashes. Each hash is the unique identifier of an individual application. If you enter multiple hashes, then they must be comma separated. Supported hash formats are specified under the field.

OR
- File Name / Path / Signer: Mark the Attributes radio button, check at least one of the File Name / Path / Signer fields checkboxes and fill the relevant values, as follows:
- Specify the executable file of the application to be blocked by filling in the File name field.
- Specify the path to the executable file of the application to be blocked by filling in the Path field.
- If you select Signer, then either upload the Signer’s Certificate (as shown below), provide its thumbprint or type in the Signer’s name. Uploading a certificate or specifying thumbprint is more secured that specifying signer name and hence recommended.

For example, selecting the Name radio button, then entering the word
Microsoft, blocks the execution of any application that was signed by Microsoft. You must enter the exact name of the Signer.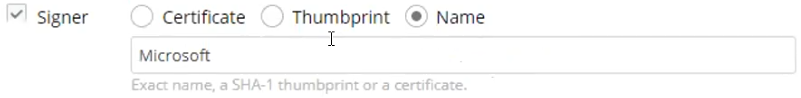
If you fill in both the File name field (described above) and the Path field, then that application is only blocked if its executable is in that path. If you only fill in the File name field, then that application is blocked no matter where its executable file appears.
Wildcards can be used in a folder name by placing a single wildcard (*) at the beginning, end and middle of the path.
For example:
*\folder0\folder1*\folder2*
- Hash: Mark the Hash radio button and specify one or more Hashes. Each hash is the unique identifier of an individual application. If you enter multiple hashes, then they must be comma separated. Supported hash formats are specified under the field.
- Click the Add button. The application is then listed in the Application Control Manager.
When a Collector Group is assigned to the application control policy (specify above), then all these applications are blocked and cannot be launched.

