NGFW policy-based mode
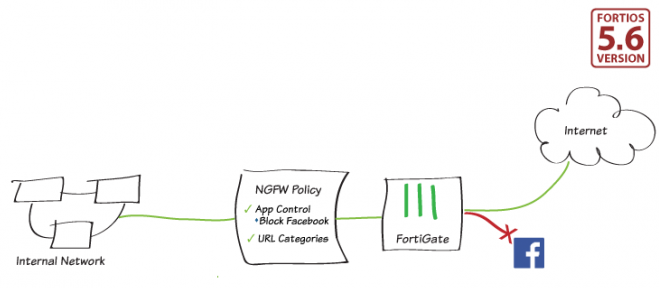
You can operate your FortiGate or individual VDOMs on your FortiGate in Next Generation Firewall (NGFW) policy-based mode when you select flow-based inspection. In NGFW policy-based mode, you can add applications and web filtering categories directly to a policy without having to first create and configure Application Control or Web Filtering profiles. If a URL category is set, the applications that are added to the policy must be within the browser-based technology category.
Switching NGFW mode from profile-based to policy-based converts your profile-based security policies to policy-based security policies. If you don’t want this to happen or you just want to experiment with policy-based NGFW mode, consider creating a new VDOM for policy-based NGFW mode. You can also back up your configuration before switching modes.
NGFW policy-based firewall policies may have unintended consequences to the passing or blocking of traffic. For example, if you add new firewall policies that are designed to DENY social media traffic based on applications or URLs, having a traditional “catch all” firewall policy to DENY all other traffic at the bottom of the firewall policy list may have the unintended consequence of blocking legitimate traffic.
NGFW policy-based mode applies the NAT settings from matching Central SNAT policies. If you don’t already have a Central SNAT policy in place, you will have to create one.
This recipe demonstrates a basic configuration of blocking Facebook using the new NGFW policy-based mode.


