MAC Address-Based Policies
This version adds a new address type — range of MAC addresses for IPv4 policies, including:
- IPv4 Firewall Policy.
- IPv4 Virtual Wire Pair Policy.
- IPv4 ACL Policy.
- IPv4 Central SNAT Policy.
- IPv4 DoS Policy.
The MAC address is a link layer-based address type and the MAC address cannot be forwarded across different IP segments.
For policies in NAT mode VDOM, we only support this new MAC address type as source address.
For policies in Transparent mode or Virtual Wire Pair interface, you can use this address type as source or destination address.
When you use this address type in a policy as source address in NAT mode VDOM, IP address translation (NAT) is still performed according to the rules defined in the policy. This new address type only works for source address matching. It does not have any association with NAT actions.
Sample configuration
To configure a MAC address range using the GUI:
- Go to Policy & Objects > Addresses to create or edit an address.
- For Category, select Address.
- For Type, select MAC Address Range and enter the address range.
- Enter the other fields and click OK.
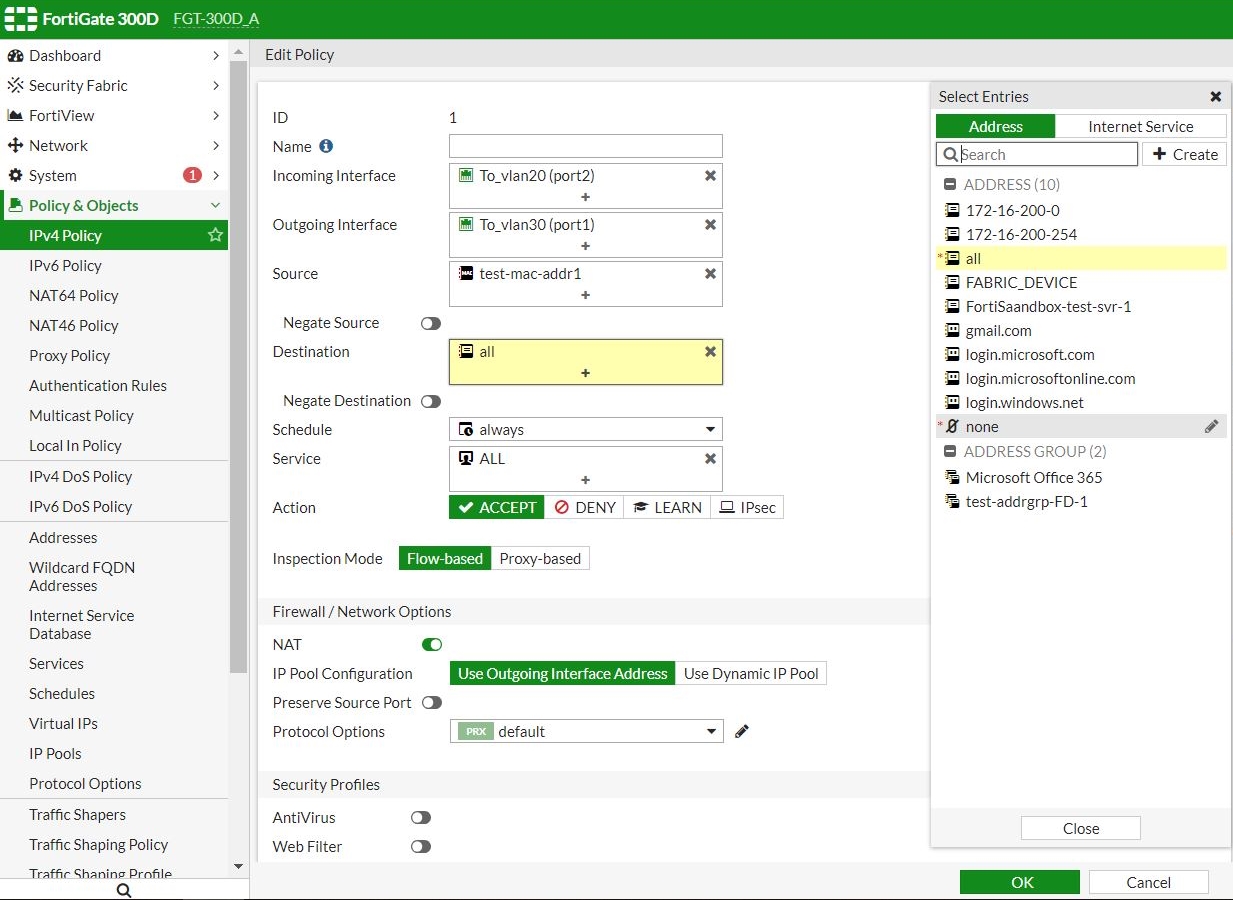
- Go to Policy & Objects > IPv4 Policy to apply the address type to a policy in NAT mode VDOM.
In NAT mode VDOM, this address type cannot be used as destination address.
To configure a MAC address range using the CLI:
- Create a new MAC address range type.
config firewall address edit <object_name> set type mac set start-mac <mac_address_start #> set end-mac <mac_address_end #> next end - Apply the address type to a policy. In Transparent mode or Virtual Wire Pair interface, this address type can be mixed with other address types in the policy.
config firewall address edit "test-mac-addr1" set type mac set start-mac 00:0c:29:41:98:88 set end-mac 00:0c:29:41:98:88 next end config firewall policy edit 1 set srcintf "port2" set dstintf "port1" set srcaddr "test-mac-addr1" "10-1-100-42" set dstaddr "all" set action accept set schedule "always" set service "ALL" set logtraffic all set nat enable next end