Example: FortiADC L7 Virtual Server with HA VRRP mode using Azure Load Balancer Topology

Creating an L7 virtual server to allow user access to protected resources from the internet
Follow the steps below to create an L7 virtual server to let the user access the protected resources from the internet.
In this example, we assume the following:
-
The protected server is a web server.
-
The web server is configured to use the VNET named FadcHAInsideSubnet.
In the example below, we will show you how to enable secure access from internet clients to a published Apache Tomcat server.
- Prepare your protected resource (the web server) and ensure it is connected to the VNET, FadcHAInsideSubnet. For this scenario, we have prepared an Apache Tomcat server.
- Check the Frontend IP configuration of the ALB, FAD-HA-loadbalance-external. This IP configuration, such as 51.x.x.x, is the Public IP for users to access the protected resource.

- Check the Backend pools of the ALB, FAD-HA-loadbalance-external. You will see both the FortiADC-VMs are in the FADHaLBBackendAddrPool with IP allocated from FadcOutSideSubnet.
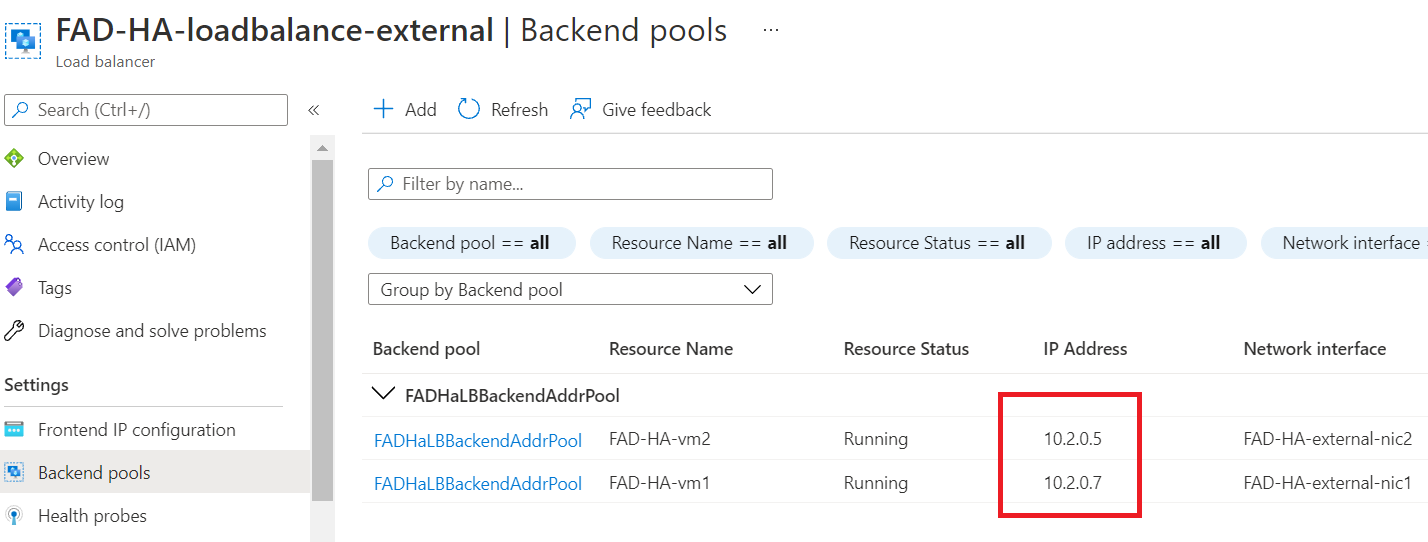
- Check the Health Probe in ALB FAD-HA-loadbalance-external.
When receiving business traffic from the user, FAD-HA-loadbalance-external directs the business traffic to the HA VRRP active FortiADC-VM, FAD-HA-VM1. ALB determines which FortiADC-VM is the active node by sending the health check packet to both FortiADC-VMs to see which will respond to the health check packet.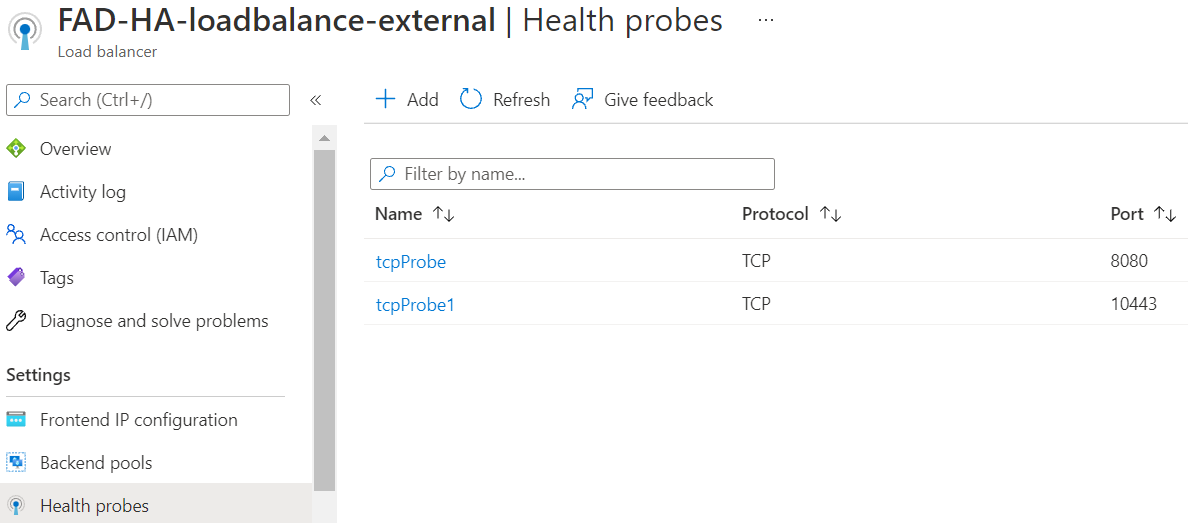
You can see there are 2 TCP Health Probes with port 8080 and 10443 respectively. - To enable the health check flow to work, the probing virtual server needs to be configured to respond to the health check packet on the FortiADC side.
- Configure the backend pool IP information of the FAD-HA-loadbalance-external on both FortiADC-VMs.
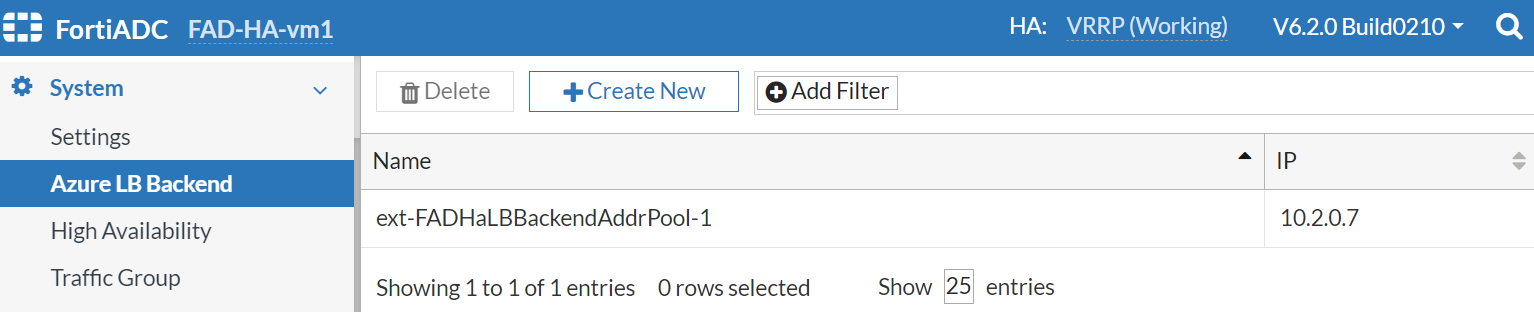
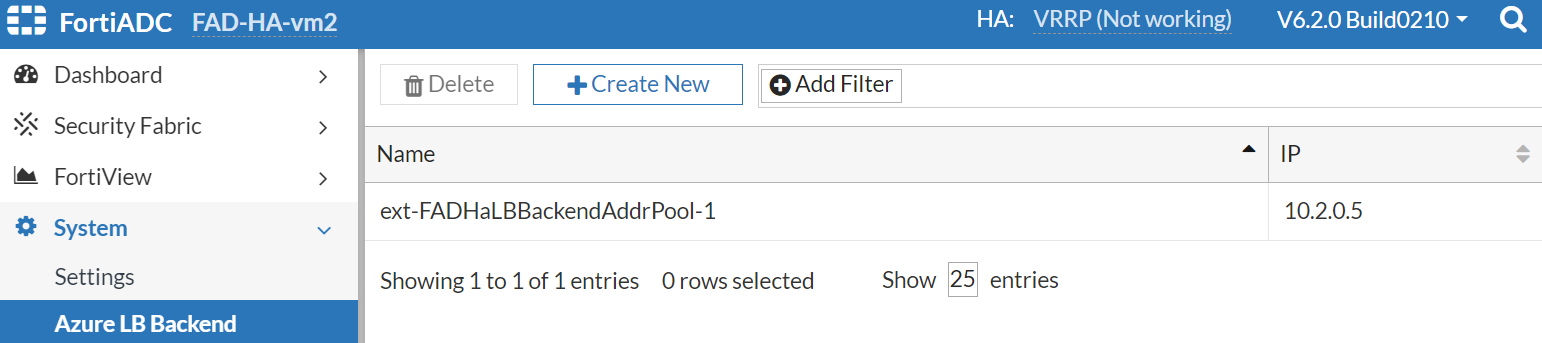
- Configure the probing VS which references the ext-FADHaLBBackendAddrPool-1 as the virtual server IP.
Set the probing VS with port 8080 and profile LB_PROF_TCP according to the tcpprobe as defined in the Health Probes of FAD-HA-loadbalance-external.
For FortiADC version 6.2.0 or later, LB_PROF_TCP is deprecated. Please use LB_PROF_L7_TCP instead.

Now, we have the probing VS using FADHaLBBackendAddrPOOL IP on both FortiADC-VMs.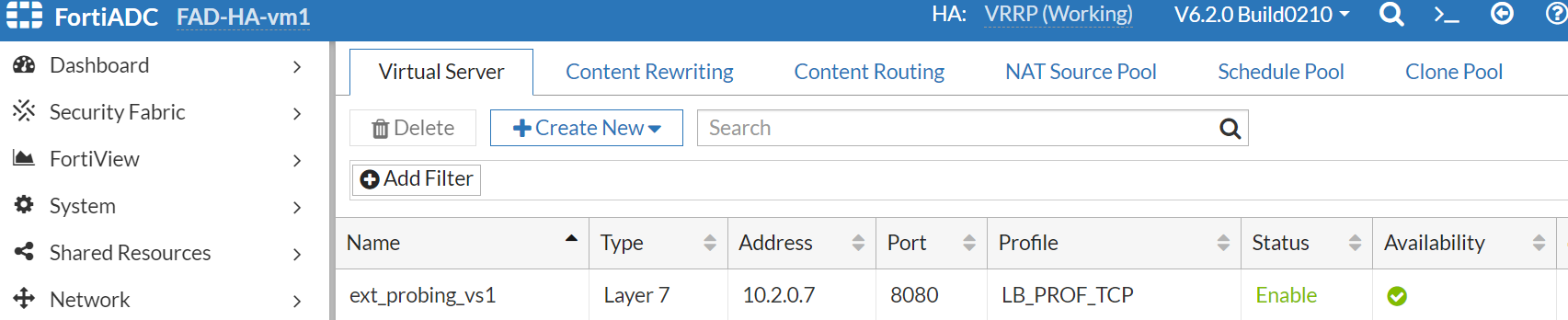

- Configure the backend pool IP information of the FAD-HA-loadbalance-external on both FortiADC-VMs.
- Create the L7 virtual server with port 443 and LB_PROF_HTTPS profile on the FortiADC-VM1. This virtual server is going to serve the HTTPS service.
We only support the ALB default route type. We also reference the azure loadbalancer backend IP in the L7 virtual server.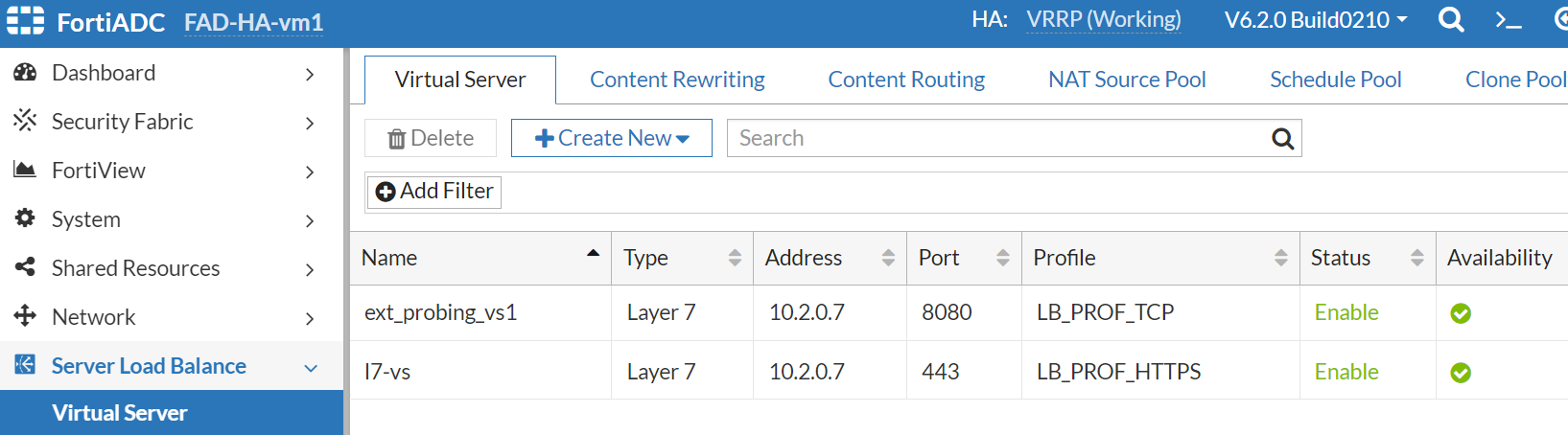
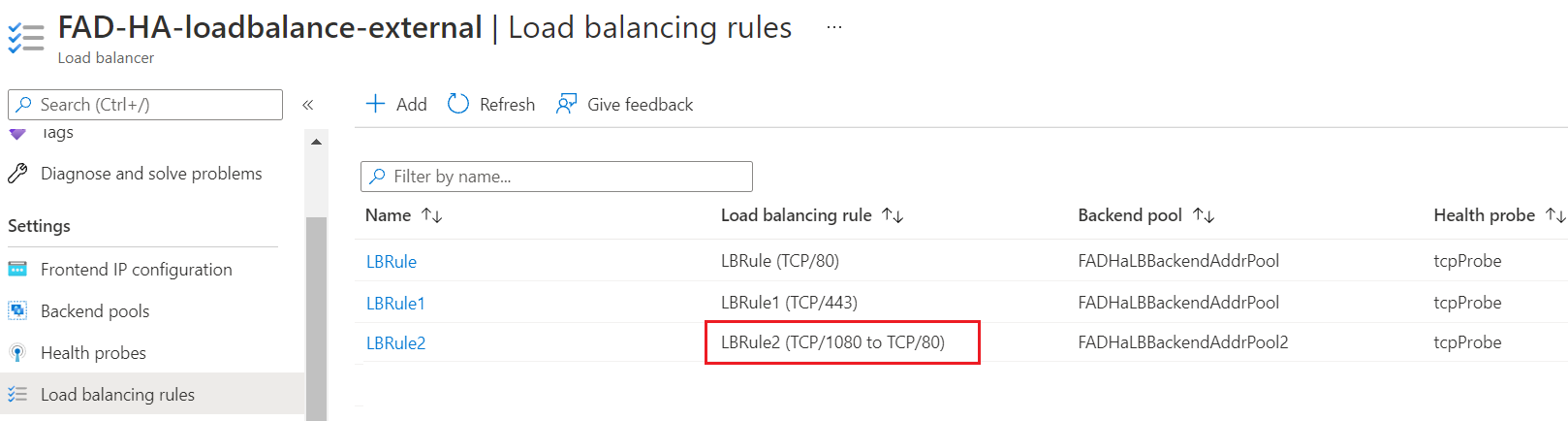
- Check the Load balancing rules in FAD-HA-loadbalance-external. Change the LBRule1 to use tcpprobe as the Heath probe.
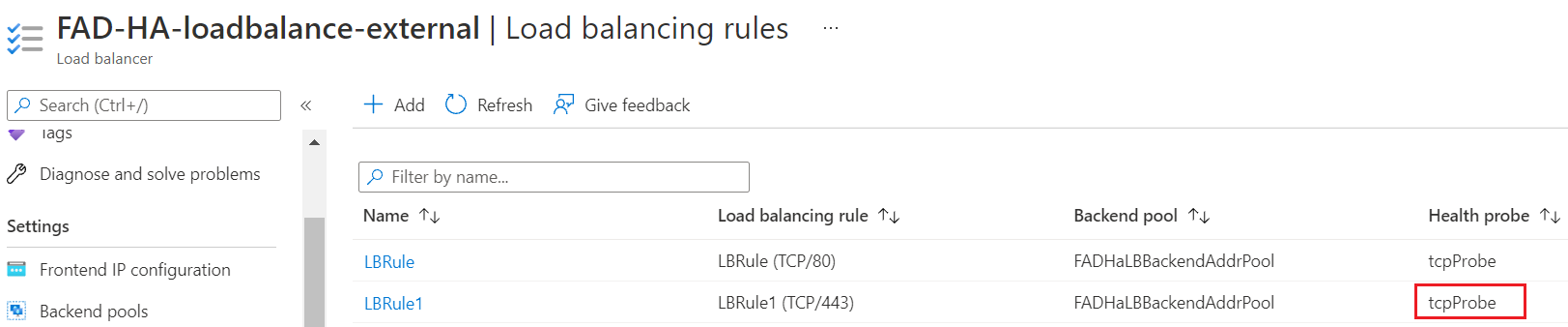
- Try to connect to https://51.x.x.x to get apache tomcat service.

Now, FAD-HA-VM1 is the active node. When HA failover occurs, the health check packet returns from FAD-HA-VM2, and the FAD-HA-loadbalance-external directs the business traffic to FAD-HA-VM2. The connection to https://51.x.x.x may lose a few seconds during the failover, but will recover soon after. - If you want to reuse the port on the backend FortiADC, you can add more backend pools in the ALB, FAD-HA-loadbalance-external.
- Add a third IP to the IP Configuration of the external interface for both of the FortiADC-VMs associated with the FadcOutSideSubnet.


- Add the ipconfig3 of both FortiADC-VMs to a new Backend pool for the ALB, FAD-HA-loadbalance-external.
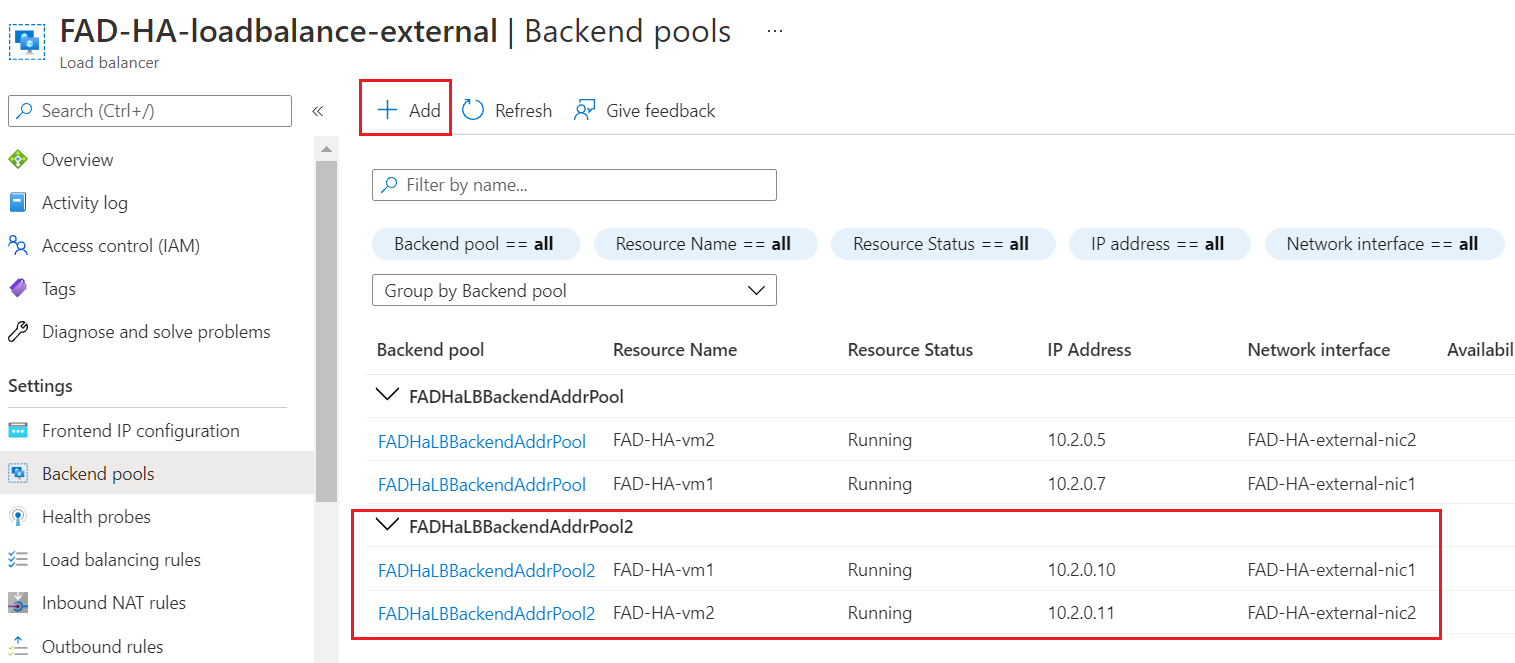
- Configure the backend pool IP information of the FAD-HA-loadbalance-external on both FortiADC-VMs.
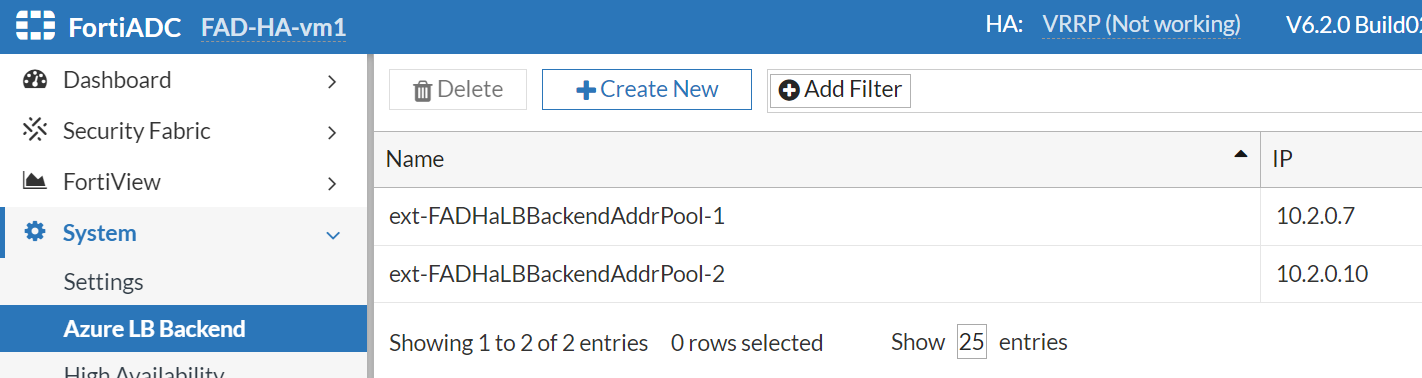

- Create the probing virtual server and L7 virtual server to reference ext-FADHaLBBackendAddrPool-2 on the FortiADC-VM2. This time we create a L7 HTTP virtual server.
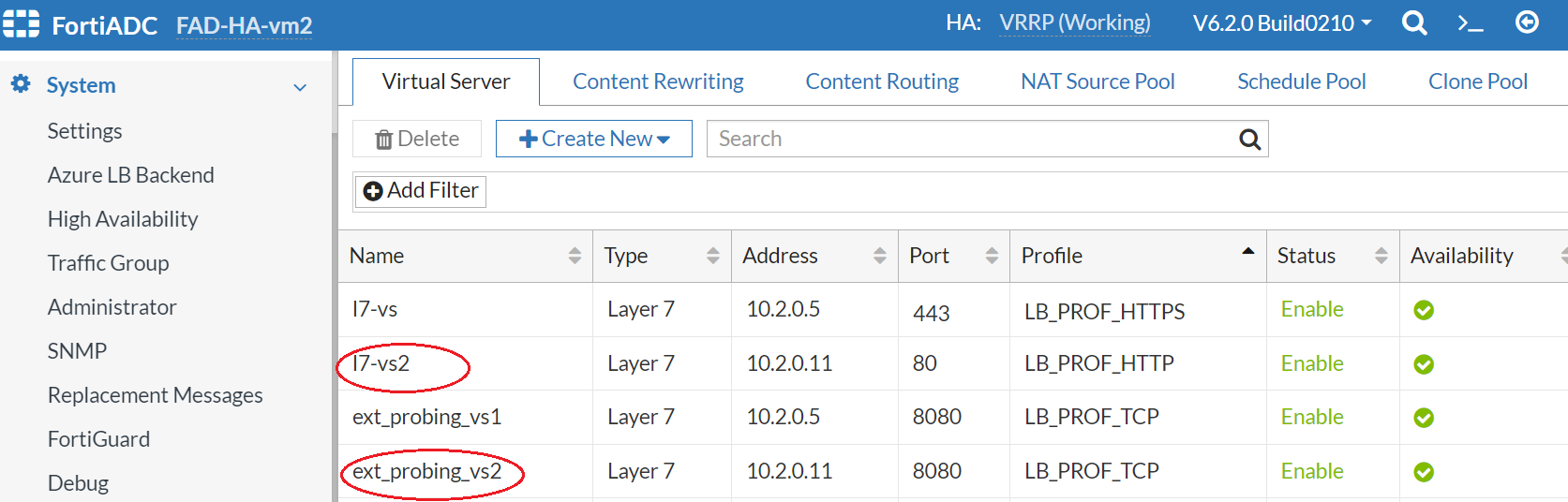
- Create a Load balancing rule to use the FADHaLBBackendAddrPool2 on FAD-HA-loadbalance-external. Map the front end port 1080 to backend port 80.
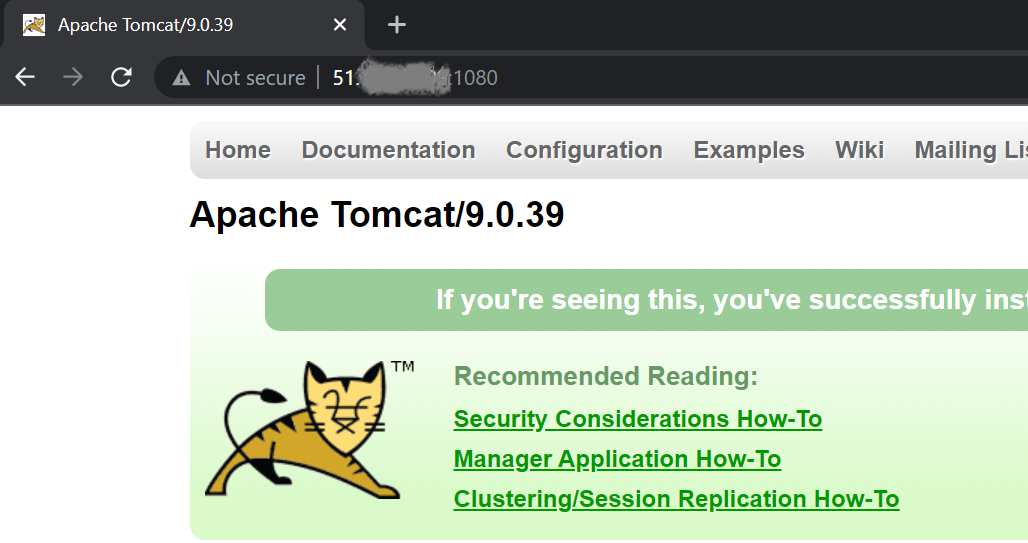
- Try to connect to http://51.x.x.x:1080 to get apache tomcat service.
- Add a third IP to the IP Configuration of the external interface for both of the FortiADC-VMs associated with the FadcOutSideSubnet.

