VRRP HA using API call to Azure
In this VRRP HA deployment mode that uses an API call to Azure, each FortiADC network interface on Azure maintains its own IP configuration table. You can add secondary IPs in the IP configuration table and use the IPs in the FortiADC configuration, such as virtual server IPs.
|
|
Prior to the FortiADC 6.2.0 release, deploying VRRP HA on Azure using an API call was the standard deployment mode. In version 6.2.0, deploying VRRP HA using Azure Load Balancers was introduced to mitigate the issues caused by the Azure API call deployment mode. We recommend deploying VRRP HA on Azure using Azure Load Balancers as the preferred deployment mode. |
In the Figure 1 example below, there are two (2) FortiADC-VMs in HA VRRP mode that share the same configuration for Virtual Server, Virtual Server NAT Pool, Firewall NAT SNAT, Firewall 1-1 NAT, and the network interface floating IP. On the Azure platform side, the corresponding IP configuration is only attached to the active FortiADC-VM, which is the FAD-HA-VM1 in this example.
Figure 1 FortiADC HA pair on Azure platform
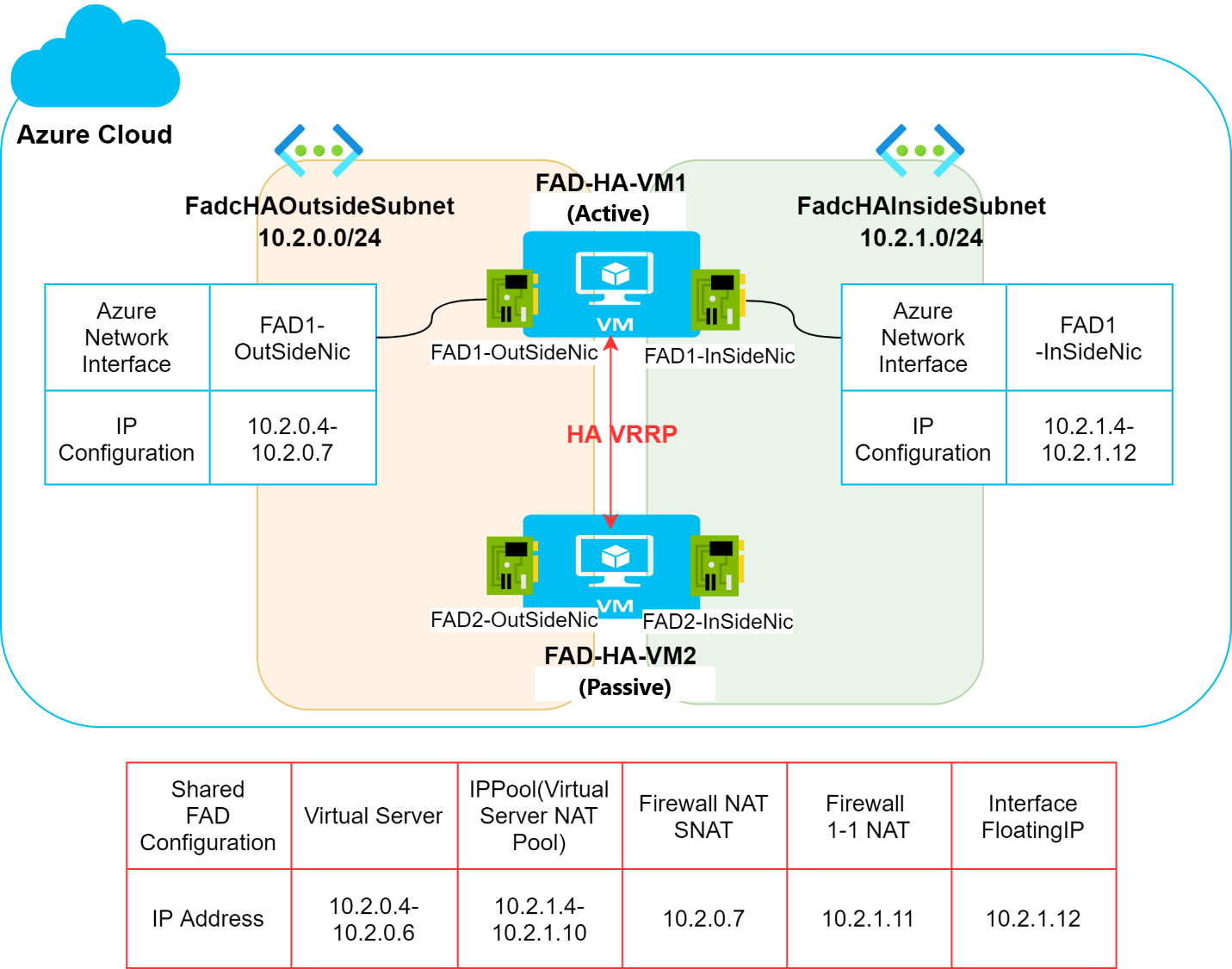
In the event of HA failover, the FAD-HA-VM2 becomes the active node. This requires the IP configuration to be migrated from FAD-HA-VM1 to FAD-HA-VM2 in the Azure backend. More specifically, this disassociates the related IP configuration on the FAD1-OutSideNic / FAD1-InSideNic and associates them on the FAD2-OutSideNic / FAD2-OutSideNic. This IP migration process is executed using an Azure API call, as illustrated in the Figure 2 example below.
Figure 2 IP Migration between the Azure network interface when HA failover occurs
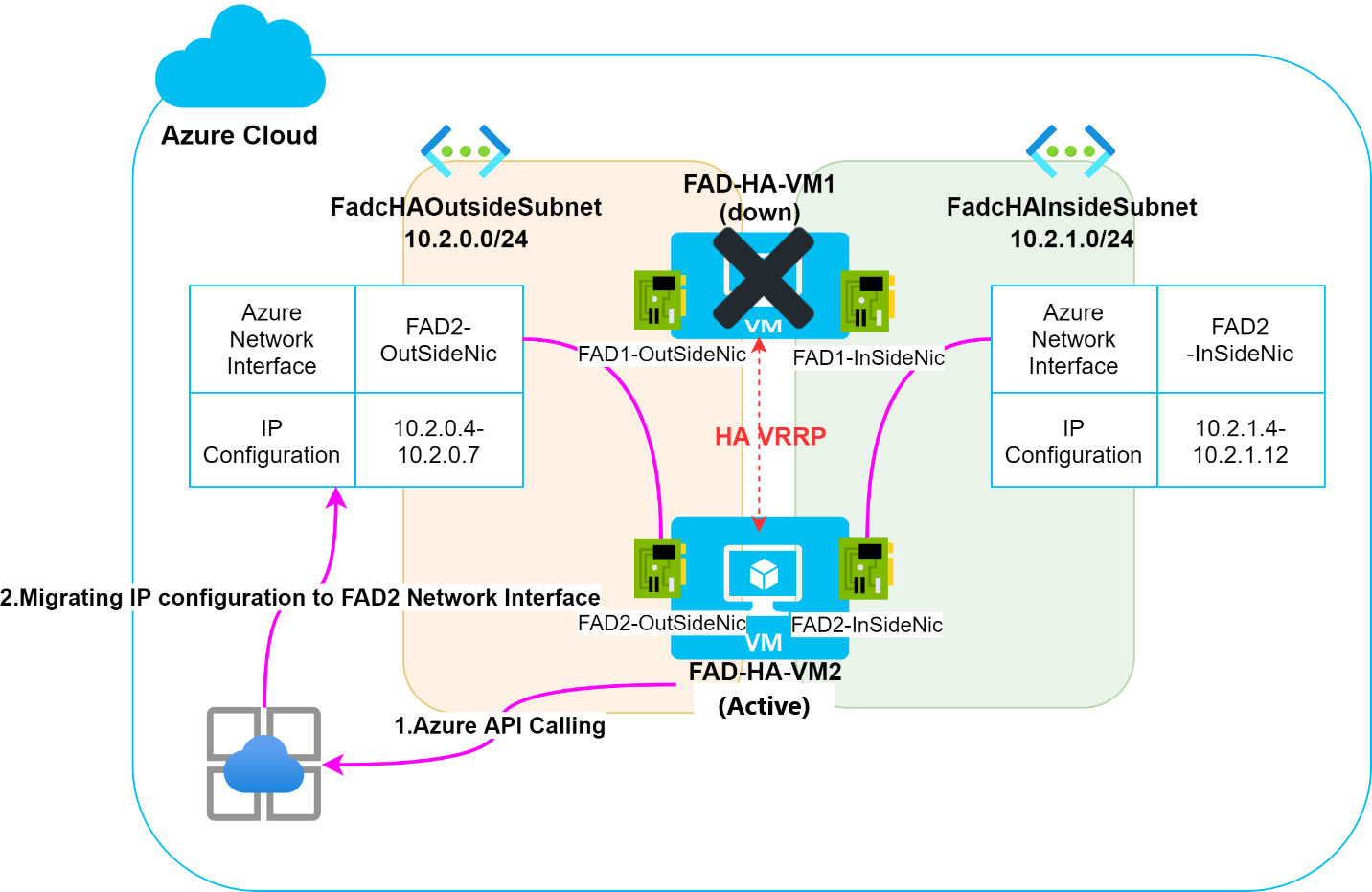
The major downside to the IP migration process is the significant amount of time required to propagate the change into the Azure environment. This may cause the business traffic to break for several minutes during the HA failover. Other critical issues may also occur, such as losing IP configuration on the Azure side during the failover.
For these reasons, FortiADC has developed a new deployment mode to avoid the issues created by the Azure API call. For more details on the new deployment mode, see VRRP HA using Azure Load Balancers.
|
|
For the Firewall 1-1 NAT configuration, the Azure API calling method is still required to migrate the IP during HA failover. |

