VXLAN over IPsec tunnel
This is an example of VXLAN over IPsec tunnel. VXLAN encapsulation is used in the phase1-interface setting and virtual-switch is used to bridge the internal with VXLAN over IPsec tunnel.
For more information, see IPsec Tunnels.
Sample topology
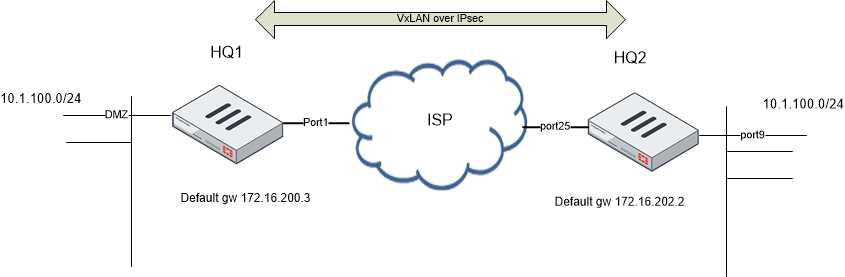
Sample configuration
To configure VXLAN over an IPsec tunnel:
- Configure the WAN interface and default route:
- HQ1:
config system interface edit "port1" set ip 172.16.200.1 255.255.255.0 next end config router static edit 1 set gateway 172.16.200.3 set device "port1" next end - HQ2:
config system interface edit "port25" set ip 172.16.202.1 255.255.255.0 next end config router static edit 1 set gateway 172.16.202.2 set device "port25" next end
- HQ1:
- Configure IPsec phase1-interface:
- HQ1:
config vpn ipsec phase1-interface edit "to_HQ2" set interface "port1" set peertype any set proposal aes128-sha256 aes256-sha256 aes128-sha1 aes256-sha1 set encapsulation VXLAN set encapsulation-address ipv4 set encap-local-gw4 172.16.200.1 set encap-remote-gw4 172.16.202.1 set remote-gw 172.16.202.1 set psksecret sample next end config vpn ipsec phase2-interface edit "to_HQ2" set phase1name "to_HQ2" set proposal aes128-sha1 aes256-sha1 aes128-sha256 aes256-sha256 aes128gcm aes256gcm chacha20poly1305 next end - HQ2:
config vpn ipsec phase1-interface edit "to_HQ1" set interface "port25" set peertype any set proposal aes128-sha256 aes256-sha256 aes128-sha1 aes256-sha1 set encapsulation VXLAN set encapsulation-address ipv4 set encap-local-gw4 172.16.202.1 set encap-remote-gw4 172.16.200.1 set remote-gw 172.16.200.1 set psksecret sample next end config vpn ipsec phase2-interface edit "to_HQ1" set phase1name "to_HQ1" set proposal aes128-sha1 aes256-sha1 aes128-sha256 aes256-sha256 aes128gcm aes256gcm chacha20poly1305 next end
- HQ1:
- Configure the firewall policy:
- HQ1:
config firewall policy edit 1 set srcintf "dmz" set dstintf "to_HQ2" set srcaddr "10.1.100.0" set dstaddr "10.1.100.0" set action accept set schedule "always" set service "ALL" next edit 2 set srcintf "to_HQ2" set dstintf "dmz" set srcaddr "10.1.100.0" set dstaddr "10.1.100.0" set action accept set schedule "always" set service "ALL" next end - HQ2:
config firewall policy edit 1 set srcintf "port9" set dstintf "to_HQ1" set srcaddr "10.1.100.0" set dstaddr "10.1.100.0" set action accept set schedule "always" set service "ALL" next edit 2 set srcintf "to_HQ1" set dstintf "port9" set srcaddr "10.1.100.0" set dstaddr "10.1.100.0" set action accept set schedule "always" set service "ALL" next end
- HQ1:
- Configure the virtual switch:
- HQ1:
config system switch-interface edit "VXLAN-HQ2" set member "dmz" "to_HQ2" set intra-switch-policy explicit next end - HQ2:
config system switch-interface edit "VXLAN-HQ1" set member "port9" "to_HQ1" set intra-switch-policy explicit next end
- HQ1:
- Optionally, view the VPN tunnel list on HQ1 with the
diagnose vpn tunnel listcommand:list all ipsec tunnel in vd 0 ---- name=to_HQ2 ver=1 serial=2 172.16.200.1:0->172.16.202.1:0 bound_if=5 lgwy=static/1 tun=intf/0 mode=auto/1 encap=VXLAN/2 options[0002]= encap-addr: 172.16.200.1->172.16.202.1 proxyid_num=1 child_num=0 refcnt=11 ilast=8 olast=0 ad=/0 stat: rxp=13 txp=3693 rxb=5512 txb=224900 dpd: mode=on-demand on=1 idle=20000ms retry=3 count=0 seqno=45 natt: mode=none draft=0 interval=0 remote_port=0 proxyid=to_HQ2 proto=0 sa=1 ref=2 serial=1 src: 0:0.0.0.0/0.0.0.0:0 dst: 0:0.0.0.0/0.0.0.0:0 SA: ref=3 options=10226 type=00 soft=0 mtu=1390 expire=41944/0B replaywin=2048 seqno=e6e esn=0 replaywin_lastseq=0000000e itn=0 life: type=01 bytes=0/0 timeout=42901/43200 dec: spi=635e9bb1 esp=aes key=16 c8a374905ef9156e66504195f46a650c ah=sha1 key=20 a09265de7d3b0620b45441fb5af44dab125f2afe enc: spi=a4d0cd1e esp=aes key=16 e9d0f3f0bb7e15a833f80c42615a3b91 ah=sha1 key=20 609a315c385471b8909b771c76e4fa7214996e50 dec:pkts/bytes=13/4640, enc:pkts/bytes=3693/623240 - Optionally, view the bridge control interface on HQ1 with the
diagnose netlink brctl name host VXLAN-HQ1command:show bridge control interface VXLAN-HQ1 host. fdb: size=2048, used=17, num=17, depth=1 Bridge VXLAN-a host table port no device devname mac addr ttl attributes 1 1. dmz 00:0c:29:4e:33:c9 1. Hit(1) 1 1. dmz 00:0c:29:a8:c3:ea 105 Hit(105) 1 1. dmz 90:6c:ac:53:76:29 18 Hit(18) 1 1. dmz 08:5b:0e:dd:69:cb 1. Local Static 1 1. dmz 90:6c:ac:84:3e:5d 1. Hit(5) 1 1. dmz 00:0b:fd:eb:21:d6 1. Hit(0) 2 38 to_HQ2 56:45:c3:3f:57:b4 1. Local Static 1 1. dmz 00:0c:29:d2:66:40 78 Hit(78) 2 38 to_HQ2 90:6c:ac:5b:a6:eb 124 Hit(124) 1 1. dmz 00:0c:29:a6:bc:e6 19 Hit(19) 1 1. dmz 00:0c:29:f0:a2:e7 1. Hit(0) 1 1. dmz 00:0c:29:d6:c4:66 164 Hit(164) 1 1. dmz 00:0c:29:e7:68:19 1. Hit(0) 1 1. dmz 00:0c:29:bf:79:30 19 Hit(19) 1 1. dmz 00:0c:29:e0:64:7d 1. Hit(0) 1 1. dmz 36:ea:c7:30:c0:f1 25 Hit(25) 1 1. dmz 36:ea:c7:30:cc:71 1. Hit(0)

