Azure Active Directory Delegated Permissions
This is the original method used. Requires a signed-in user to give FortiNAC permission to use the API when creating an MS InTune service connector. The process was error-prone and involved the user jumping back and forth between the MS Azure portal and the MS InTune connector view.
Existing MS Intune connectors (prior to the change) will have the Enable Delegated Permissions method enabled and will continue to work as before. However, for new service connectors, this button will be disabled and instead will require the user to register the Application with Azure with Application Permissions which is a much simpler process and better user experience.
The following information is for reference.
Step 1: Configure Azure Active Directory
-
Configure the Redirect URI. This will be used when responding to the authentication request made by FortiNAC in the next section (Configure FortiNAC step 3 - Authenticate With Azure AD).
-
Leave window open. In a separate browser window, login to the FortiNAC Administration UI. Name used in URL should be the hostname secured by the SSL certificate for the Admin UI. Certificates can be viewed under Security Configuration > Certificate Management.
https://<FortinacDNSHostname>:8443/
-
Navigate to Network > Service Connectors.
-
Click Create New.
-
Click Microsoft InTune.
-
Populate the Name field and click OK. The new Fabric Connector should now appear.
-
Double click on the connector or right-click and select Edit.
-
-
Copy the entire URL in the browser window and leave window open. The URL should look similar to the following
https://<FortinacDNSHostname>:8443/gui/network/service-connectors/MICROSOFT_INTUNE_MDM/1
-
In the Azure window under Redirect URI, select Web.
-
In the other field, enter the URL copied in step g.

Important: If the FortiNAC hostname in the browser URL does not match the hostname entered in the Redirect URI, the authentication attempt will fail because the hostname in the URI does not match the hostname in the request.High Availability: If FortinNAC is configured for High Availability, enter URI for Primary Server and the URI for the Secondary Server (do not use a shared name).
-
From the Application Registration view, copy down the following (will be used in FortiNAC configuration):
-
Application (client) ID
-
Directory (tenant) ID

-
-
From Certificates & Secrets select + New client secret and create a secret.
-
Review the secret for special characters (specifically colons or question marks). If they are present, generate a new secret. Repeat this process until a secret is generated without these special characters. The Refresh Token generated in the following section may not populate if the client secret contains colons or question marks. This caveat is currently under investigation.
-
Copy and store the secret value (not the ID). This will be used in FortiNAC configuration.
Note: The secret will be obscured once leaving the view and returning.
-
From API Permissions select + Add a permission.
-
Select Microsoft Graph > Delegated permissions
-
From the list expand DeviceManagementManagedDevices
-
Select the following:
DeviceManagementManagedDevices.Read.All

-
Grant Consent for the selected API’s by selecting the Grant admin consent for… button.

Step 2: Configure Service Connector in FortiNAC
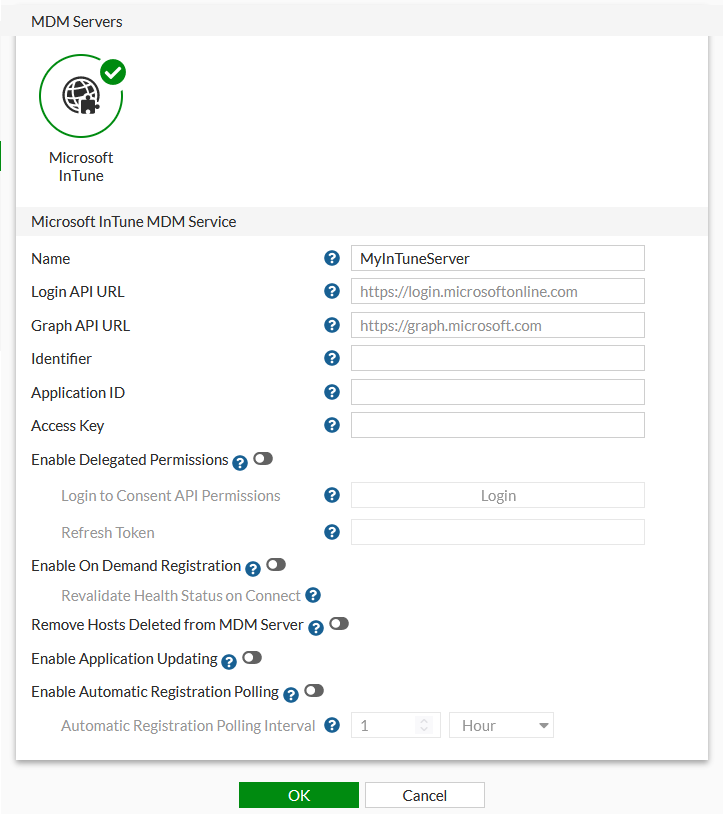
Configure a MDM Service to establish a connection with the Microsoft InTune Graph API.
-
Navigate to Network > Service Connectors and create new Microsoft InTune connector.
-
Use the field definitions for the MDM Services in the following table to enter the MDM Service information.
MDM Services Field Definitions
Field
Definition
Name
Name of the connection configuration for the connection between an MDM system and FortiNAC.
Identifier
Add the Directory (tenant) ID.
Application ID
Add the Application (client) ID.
Access Key
Add the Client Secret Value.
-
Close any other browser windows that are logged into Microsoft before proceeding.
-
Click the radial button next to Enable Delegated Permissions to enable.

-
Click the Login button. This will launch a dialog that will prompt to log into the Microsoft account.
Important: Use the same admin account used to create the Application within Azure.
This will generate a Refresh Token, and populate it in the Refresh Token field. The Refresh Token will be used by FortiNAC to generate access tokens. These tokens allow FortiNAC to perform API queries for the Graph API.
Note: The Refresh Token may not populate if the client secret contains special characters such as colons and question marks. See step 5 of Create a New Application Registration.
-
Use the field definitions for the MDM Services in the following table to enter the MDM Service information.
MDM Services Field Definitions
Field
Definition
Enable On Demand Registration
If enabled, when an unknown host reaches the captive portal, FortiNAC queries the MDM server for information about that host. If the host exists in the MDM server, it is registered in FortiNAC using the data from the MDM server.
Remove Hosts Deleted from MDM Server
If enabled, when FortiNAC polls the MDM server it deletes hosts from the FortiNAC database if they have been removed or disabled on the MDM server.
Enable Application Updating
**Leave disabled. Currently not applicable with InTune**
Enable Automatic Registration Polling
(MDM Polling)
Indicates how often FortiNAC should poll the MDM system to collect managed device information. Each time a poll executes, queries are sent to the MDM for:
-
The managed device list (one query per 100 entries)
-
One additional query per each managed device
If MDM notifications are configured, set the MDM Poll frequency to 1 Day.
If notifications are not configured, the frequency can be set higher.
Note: When choosing an interval, consider the number of queries sent per MDM poll, the size of the MDM’s database and the number of PODs integrated with the same MDM. If the frequency is set too high, the MDM may not be able to manage the rate of queries from FortiNAC, causing performance issues.
-
-
Click OK to save.
-
To verify FortiNAC can reach the MDM Server, right-click on the connector and select Test Connection.
-

-
To manually poll the MDM Server, right-click on the connector and select Poll.
-
To make any changes to the connector configuration, right-click and select Edit.
-
(Versions 9.1.5, 9.2.2 and above): Enable Host by Serial Number lookup. Allows FortiNAC to find hosts by serial number if unable to find by MAC address. Refer to ID 0761623 in Release Notes. In the FortiNAC CLI, login as root and run
globaloptiontool -name persistentAgentSecMgmt.findHostBySerialNumber -set true

