Design considerations
Accessing Security Fabric devices without FortiPAM increases the risk of credentials leaking, unauthorized access, and difficultly tracking user activity.
FortiPAM helps enhance security in an enterprise network by providing role-based access, auditing, and security options for privileged users. The privileged users have system access beyond that of a regular user.
By offering functionalities that include credential vaulting, privileged account access control, and privileged activity monitoring and recording, FortiPAM helps reduce security risks associated with privileged user activities in an enterprise network.
Further, FortiPAM offers ZTNA tag-based and protocol-based access control (RDP, VNC, and WEB) for access from anywhere, including native web-based access. This helps protect critical assets with the highest level of security. For more information on FortiPAM ZTNA feature, see ZTNA in the latest FortiPAM Administration Guide.
Topology
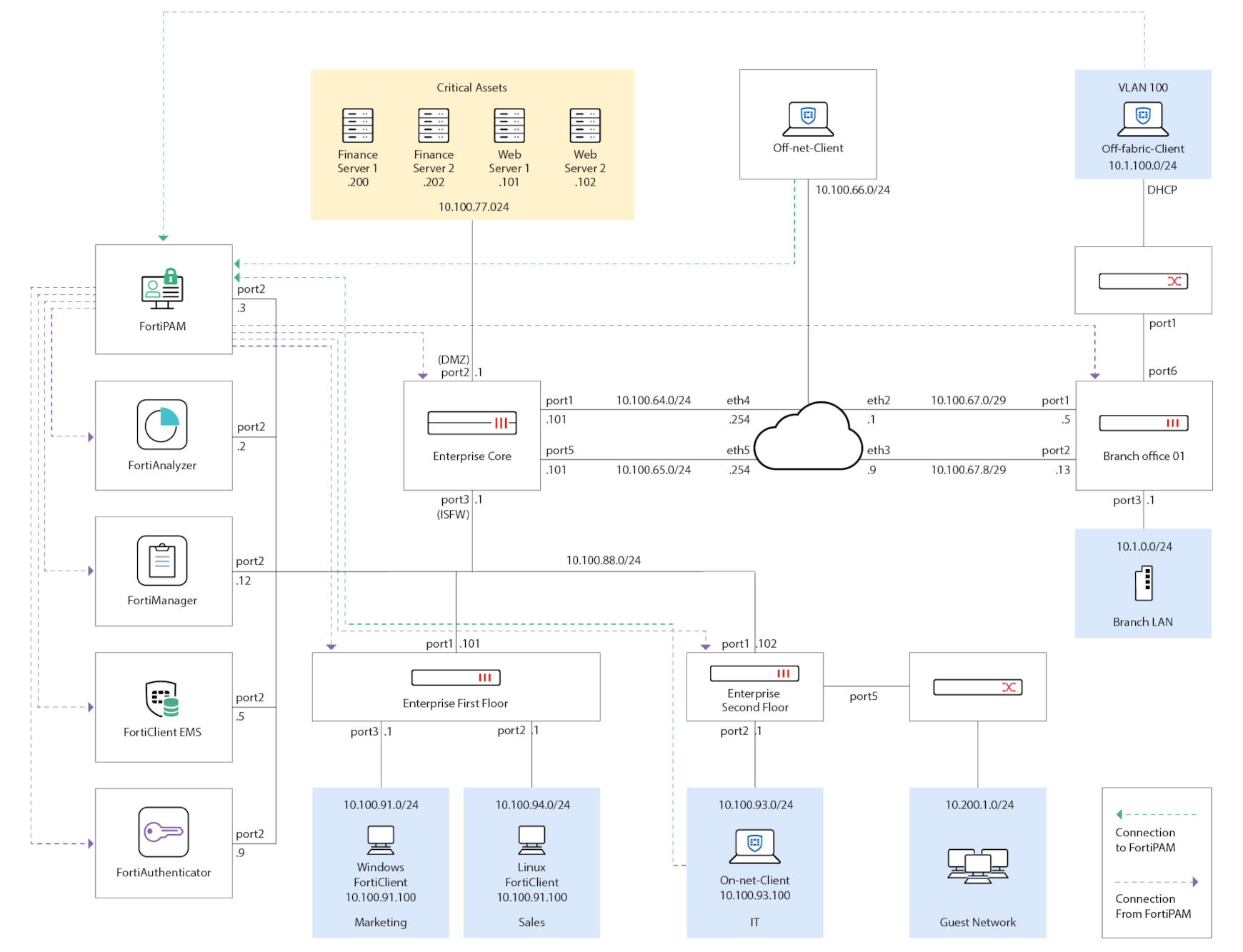
For the purpose of this Deployment guide, we cover the following:
Fabric devices and networks
Fortinet Security Fabric devices and their administrative interfaces:
|
Device |
Port/service |
HTTPS access |
SSH access |
|---|---|---|---|
|
Enterprise_Core |
port3 (ISFW) |
https://10.100.88.1 |
10.100.88.1 |
|
Enterprise_First_Floor |
port1 |
https://10.100.88.101 |
10.100.88.101 |
|
Enterprise_Second_Floor |
port1 |
https://10.100.88.102 |
10.100.88.102 |
|
Branch_Office_01 |
port3 |
https://10.1.0.1 |
10.1.0.1 |
|
FortiAnalyzer |
port2 |
https://10.100.88.2 |
None |
|
FortiManager |
port2 |
https://10.100.88.12 |
None |
|
FortiAuthenticator |
port2 |
https://10.100.88.9 |
None |
|
EMS_Server |
HTTPS |
https://10.100.88.5 |
None |
User and user groups
Users defined for the forti-arbutus.local domain:
|
User Group |
User |
Password |
|---|---|---|
|
Administrators, IT |
Mark Gilbert (MarkGilbert) |
SecurityFabric |
|
Customer Support |
John Locus (JohnLocus) |
SecurityFabric |
|
Marketing |
Tami Gerber (TamiGerber) |
SecurityFabric |
|
Adminstrators |
Administrator |
SecurityFabric |
Note: In this deployment, we use Active Directory users.
For the purpose of this Deployment guide, we assume that you will be deploying a full FortiPAM solution involving FortiPAM, EMS, and standard FortiClient. When both FortiPAM and FortiClient register to EMS, ZTNA endpoint control is available for secret launching and FortiPAM server access control.

