Site-to-site IPsec VPN with overlapping subnets
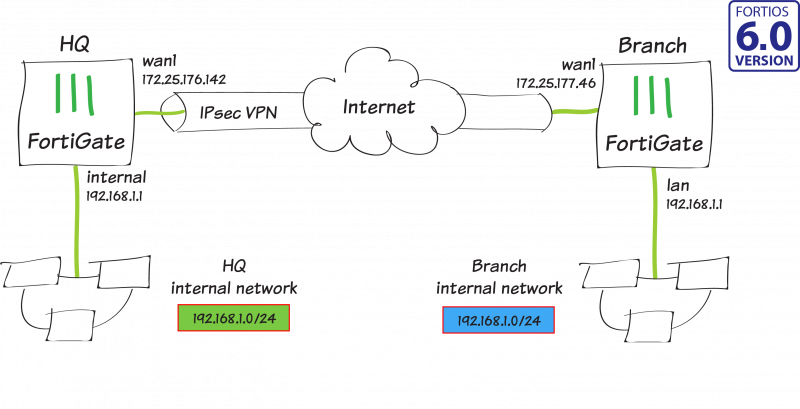
In this recipe, you create a route-based IPsec VPN tunnel, as well as configure both source and destination NAT, to allow transparent communication between two overlapping networks that are located behind different FortiGates.
In this example, one FortiGate will be referred to as HQ and the other as Branch. They both have 192.168.1.0/24 in use as their internal network (LAN), but both LANs need to be able to communicate to each other through the IPsec tunnel.

