Appendix L : WinRM configuration for Windows server
WinRM is needed for agentless RDP session log retrieving.
Use the commands as shown below to enable WinRM and set authentication on the target Windows servers.
- Configuring Windows server
- Configuring firewall rules for WinRM
- Creating a privileged account
- Setting up audit policy for RDP log retrieval
Configuring Windows server
To configure Windows server:
- Open the Windows PowerShell console as an administrator and enter the following commands to enumerate the listeners:
PS C:\Users\xxx> winrm quickconfig PS C:\Users\xxx> winrm set winrm/config/service '@{AllowUnencrypted="true"}' PS C:\Users\xxx> winrm enumerate winrm/config/listener - After enumerating the listeners, if HTTPS listener is not enabled, run the following command:
PS C:\Users\xxx> New-SelfSignedCertificate -Subject 'CN=<windows host name>' -TextExtension '2.5.29.37={text}1.3.6.1.5.5.7.3.1'PS C:\Users\xxx> winrm create winrm/config/Listener?Address=*+Transport=HTTPS '@{Hostname="<windows host name>"; CertificateThumbprint="<thumbprint received by New-Self Signed Certificate>"}'PS C:\Users\xxx> winrm quickconfig -transport:https
PS C:\Users\xxx> winrm enumerate winrm/config/listener

Single quotes are required for Windows 2016 and later.
Configuring firewall rules for WinRM
On some Windows servers and cloud platforms, the WinRM traffic (5985 for HTTP, 5986 for HTTPs) can be blocked by default.
Ensure that WinRM traffic is allowed for RDP log retrieving.
To enable Windows Remote Management:
-
On the target Windows server, go to Control Panel > System and Security > Windows Defender Firewall.

- From the menu on the left, select Advanced settings.
- In the User Account Control dialog that opens, click Yes.
A new window opens.

- From the menu on the left, select Inbound Rules.
- In the Inbound Rules window, according to your network topology, right-click Windows Remote Management and select Enable Rule.
Creating a privileged account
We create a new user belonging to the administrators groups.
To create a privileged account:
- Go to Control Panel > System and Security.

- Click Administrative Tools.
- In the User Account Control dialog that opens, click Yes.
A new window opens.

- Double-click Computer Management to open it.
- In the User Account Control dialog that opens, click Yes.
The Computer Management window opens.

- From the navigation pane on the left, select Local Users and Groups.

- Right-click the Users folder and select New User....
The New User dialog opens.
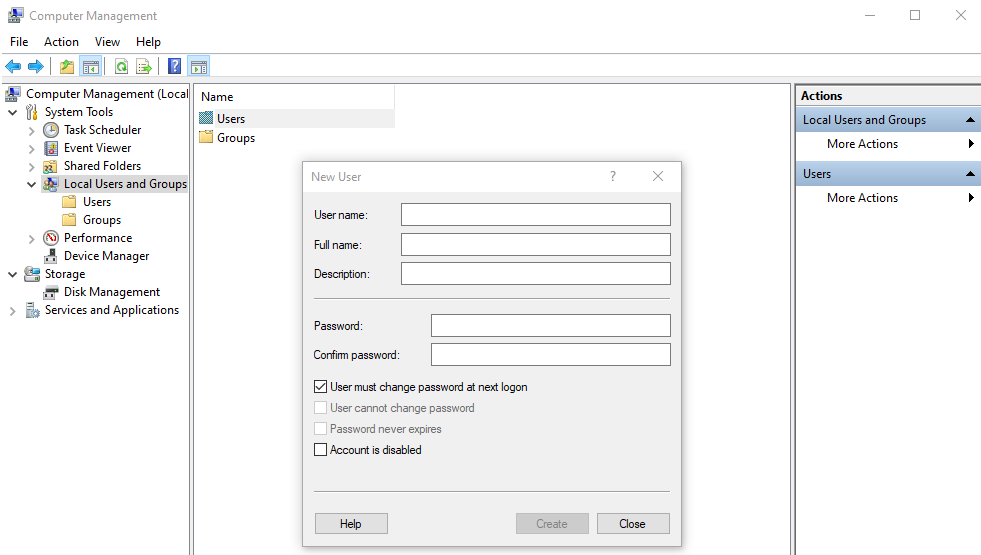
- In the New User dialog:
- In User name, enter a username.
- In Full name, enter the full name of the user.
- In Description, enter a description for the user.
- In Password, enter a password.
- In Confirm password, enter the password again to confirm.
- Click Create to create the user.
- Double-click the Users folder, right-click the user that was created in step 8, and select Properties.
- In the new dialog that opens, go to the Member Of tab, select Administrators, and click Add....
- Click OK to save changes.

If you intend to retrieve RDP logs for the privileged account, you must create a secret for the privileged account with a Windows target. See Creating a secret.
Setting up audit policy for RDP log retrieval
To set up audit policy for RDP log retrieval:
- Log in to the Windows machine to configure the policy as an administrator.
- Go to Control Panel > System and Security.
- Click Administrative Tools and in the new window that opens, double-click Local Security Policy.
- In the the User Account Control dialog that opens, click Yes.
The Local Security Policy window opens.

- From the navigation pane on the left, expand Local Policies > Audit Policy.

- For the event filter profile that applies to the privileged account secret on FortiPAM:
- If Process Log is set to Monitor, set Audit process tracking as success and failure by right-clicking Audit process tracking, selecting Properties, selecting Success and Failure, and clicking OK.
- If Filesystem Log is set to Monitor, set Audit object access as success and failure by right-clicking Audit object access, selecting Properties, selecting Success and Failure, and clicking OK.

When you enable the policy to audit object access events, you must specify which files, folders, and user actions are logged.
You must be specific with the setting to avoid excessive logging.
- If User Management Log is set to Monitor, set Audit account management as success and failure by right-clicking Audit account management, selecting Properties, selecting Success and Failure, and clicking OK.
- Log in to the Windows machine to configure policy and administrator privileges.
- On the Windows machine, open File Explorer, right-click the file you intend to set the auditing policy for, and select Properties:
- Go to the Security tab, click Advanced.
- Go to the Auditing tab, click Continue.
- In the User Account Control dialog, click Yes.
- Click Add.

The Add button is labelled Edit on Windows 8.
- In the new window that opens, click Select a principal.
- In Select User, Computer, Service Account, or Group, click Advanced.
- Select users whose access to the file you want to monitor.
- Click OK.
- In the Permissions tab, set the permission for each of the user you have added.
- Click OK.
- Click OK.
The configuration is now complete. Windows will generate audit events when the users you have specified takes actions on the files or folders for which you have set up audit policies.

