How to add FortiGate SD-WAN Inbound Load Balancing to FortiGSLB
Follow the steps to add FortiGate SD-WAN Inbound Load Balancing to FortiGSLB.
- Create New Virtual Servers in FortiGate (Policy & Objects > Virtual Servers) or use the existing Virtual Server.
- Create FortiGate connector in Fabric Connectors and enable sync virtual servers. Wait a few seconds for virtual servers to sync with FortiGate.
- Create FQDN in GSLB services > Create FQDN member > Create new Virtual Server Pool > Select Connector members (FortiGate Virtual Servers). Choose SDWAN-InBandwidth as the preferred method.
- The virtual servers from the FortiGate connector will be added into the Pool and will work in GSLB services.
Example solution
This example illustrates the solution for when all the incoming traffic comes from one ISP.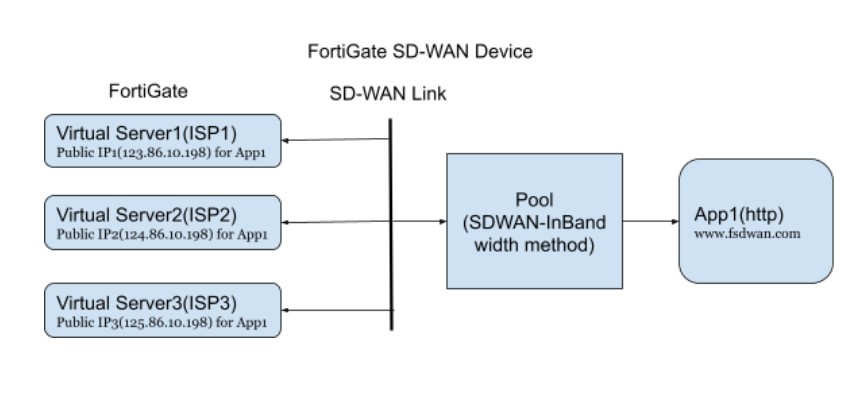

The example assumes that the customer has three ISP routers. The FortiGate SD-WAN has three members for each ISP. The SD-WAN will do the out-going load balance for App1, but in some cases the incoming traffic will keep coming from ISP1 and ISP2, which causes the ISP1 and ISP2 links to be very busy and leaves ISP3 link very free.
To solve this issue, FortiGSLB can load balance the incoming traffic to ISPs from the DNS level.
Steps:
- Create New Virtual Server in FortiGate (Policy & Objects > Virtual Servers) or use an existing Virtual Server.
- Create FortiGate connector in Fabric Connectors and wait few seconds to sync virtual servers
- Bind SD-WAN link with virtual servers in FortiGate Connector
- Create FQDN App1-www.fsdwan.com in GSLB services.
- Create FQDN member > Create new Virtual Server Pool. Select Connector member ISP1/ISP2/ISP3, enable health check Default_HLTHCK_HTTP, and choose SDWAN-InBandwidth as the preferred method.
- The virtual server from the FortiGate Connector will be added into the Pool and will work in GSLB services.
Sample topology view at FortiGSLB

After completing these steps, the customer will be able to monitor the App1 status for all ISPs on the GSLB service detail page. The FortiGSLB will load balance the traffic to three links. If one of the links is down, the FortiGSLB will direct the traffic to the available link. If all of the links are down, the FortiGSLB will direct the traffic to the App1 default server.

