Create or edit a REST API administrator
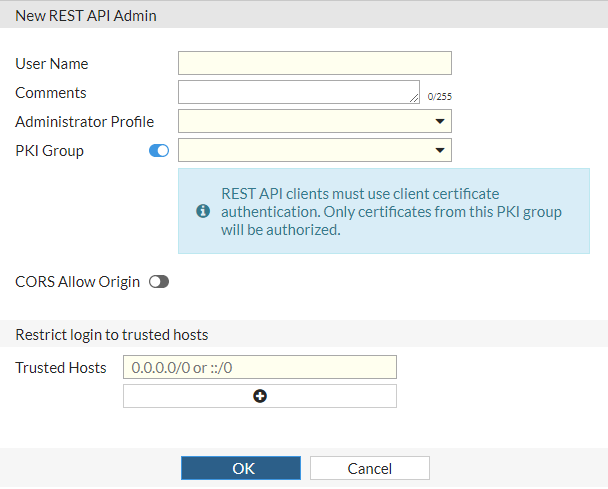
Select Create New > REST API Admin to open the New REST API Admin page. It provides settings for configuring a REST API administrator account.
Select a REST API administrator and then click Edit to open the Edit REST API Admin page.
Configure the following settings in the New REST API Admin page or Edit REST API Admin page and then click OK:
|
User Name |
Enter the login name for the administrator account. The name of the administrator should not contain the characters |
|
Comments |
Optionally, enter comments about the administrator account. |
|
Administrator Profile |
Select an administrator profile to use for the new administrator. To create an administrator profile, see Create or edit an administrator profile. |
|
PKI Group |
Enable this option for REST API clients and then select which PKI group to accept. |
|
CORS Allow Origin |
Enable this option for cross-origin resource sharing (CORS) and then specify the URL that can access the REST API. |
|
Trusted Hosts |
Enter the trusted hosts allowed to log in to the REST API. |
Using trusted hosts
Setting trusted hosts for all of your administrators increases the security of your network by further restricting administrative access. In addition to knowing the password, an administrator can connect only through the subnet or subnets that you specify. You can even restrict an administrator to a single IP address if you define only one trusted host IP address with a netmask of 255.255.255.255.
When you set trusted hosts for all administrators, the unit does not respond to administrative access attempts from any other hosts. This provides the highest security. If you leave even one administrator unrestricted, the unit accepts administrative access attempts on any interface that has administrative access enabled, potentially exposing the unit to attempts to gain unauthorized access.
The trusted hosts you define apply to the GUI, Ping, SNMP, and the CLI when accessed through Telnet or SSH. CLI access through the console port is not affected.
The trusted host addresses all default to 0.0.0.0/0.0.0.0. If you set one of the zero addresses to a nonzero address, the other zero addresses will be ignored. The only way to use a wildcard entry is to leave the trusted hosts at 0.0.0.0/0.0.0.0. However, this configuration is less secure.

