Retrospective IoC - History Scan (Threat Hunting)
This feature expands Indicators of Compromise (IoC) scanning to include DNS and traffic logs, along with the previously included web filter logs. The scan time range can also be customized to scan further back in time, so that when a new package is received from FortiGuard, it will be able to immediately scan back using the new definitions.
This feature requires a valid IoC license. The rescan options will not be available in the GUI or CLI without a license. The administrator must have System Settings write privileges to enable or disable and configure global rescan.
To configure global rescan settings in the GUI:
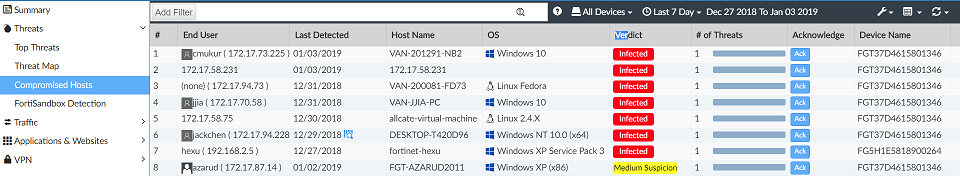
- Go to SOC > FortiView > Threats > Compromised Hosts.
- From the Tools menu on the right hand side of the toolbar, select Edit Rescan Configuration. The Edit IoC Rescan Policy Settings window opens.

- Under IoC Rescan Global Settings:
- Turn on Enable Global IoC Rescan.
- Set the running time to either a specific hour of the day, or package update to rescan when the package is updated.
- Under IoC Rescan Current ADOM Settings:
- Turn on Enable Current ADOM IoC Rescan.
- Select the log types that are scanned (DNS, Web Filter, and Traffic logs).
- Set the number of previous days' logs that are scanned.
By default, all log types are selected, and the scan will cover the past 14 days. The maximum recommended number of scan days is calculated based on historical scan speeds, or 30 days if no previous scans have been done.
- All scan tasks are shown in the Rescan tasks table, which includes:
- The start and end time of each task.
- The status of the task (complete, running, etc.).
- How complete a task is, as a percent.
- The total number of scanned logs and the threat count (the number of logs with threats) for each task.
- The IoC package update time.
- A count of the new threats that were added in this update.
Running tasks can be canceled by clicking the cancel button in the Status column.

- Click a non-zero threat count number in the Rescan tasks table to drill down to a specific scans task details. These details include the Detect Pattern, Threat Type, Threat Name, # of Events, and the Endpoint.

- Click Back to return to the settings window.
- Click OK to return to the compromised hosts list.
- In the compromised hosts list, a rescan icon will be shown in the Last Detected column if any threats where found during a rescan. To view only those hosts that had threats found during a rescan, select Only Show Rescan from the Tools menu in the toolbar.
To configure global rescan settings with the CLI:
- Configure global rescan settings:
config system log ioc
set notification {enable | disable}
set notification-throttle <integer>
set rescan-max-runner <integer>
set rescan-run-at {0 | 1 - 24}
set rescan-status {enable | disable}
set status {enable | disable}
end
where:
Variable
Description
notification {enable | disable}
Enable/disable IoC notification (default = enable).
notification-throttle <integer>
The minute value for throttling the rate of IoC notifications (1 - 10080, default = 1440).
rescan-max-runner <integer>
The maximum number of concurrently running IoC rescans (1 - CPU maximum, default = 8).
rescan-run-at {0 | 1 - 24}
The hour when the IoC rescan runs (1 - 24, 0 = run when there is a package update, default - 0)
rescan-status {enable | disable}
Enable/disable the IoC rescan feature (default = enable).
status {enable | disable}
Enable/disable the IoC feature (default = enable).
- View the current and historical scan tasks:
diagnose test application scansched 11 history <adom>
adom_name adom_oid t_add status logs_count percent threats_count t_begin t_end
Corporate 782 1546881863 running 655746608 34 4471 Mon Jan 7 09:24:29 2019
Mon Jan 7 09:50:48 2019
Corporate 782 1546809626 complete 595550740 100 0 Sun Jan 6 13:20:34 2019
Sun Jan 6 13:35:32 2019
diagnose test application scansched 11 current <adom>
adom_name adom_oid t_add status logs_count percent threats_count t_begin t_end
Corporate 782 1546881863 running 655746608 31 4085 Mon Jan 7 09:24:29 2019
Mon Jan 7 09:51:12 2019

