Secure tunneling
This example shows how to configure two FortiGate units for active-passive WAN optimization with secure tunneling. The same authentication group is added to both FortiGate units. The authentication group includes a password (or pre-shared key) and has Peer Acceptance set to Accept any Peer. An active policy is added to the client-side FortiGate unit and a passive policy to the server-side FortiGate unit. The active policy includes a profile that performs secure tunneling, optimizes HTTP traffic, and uses transparent mode and byte caching.
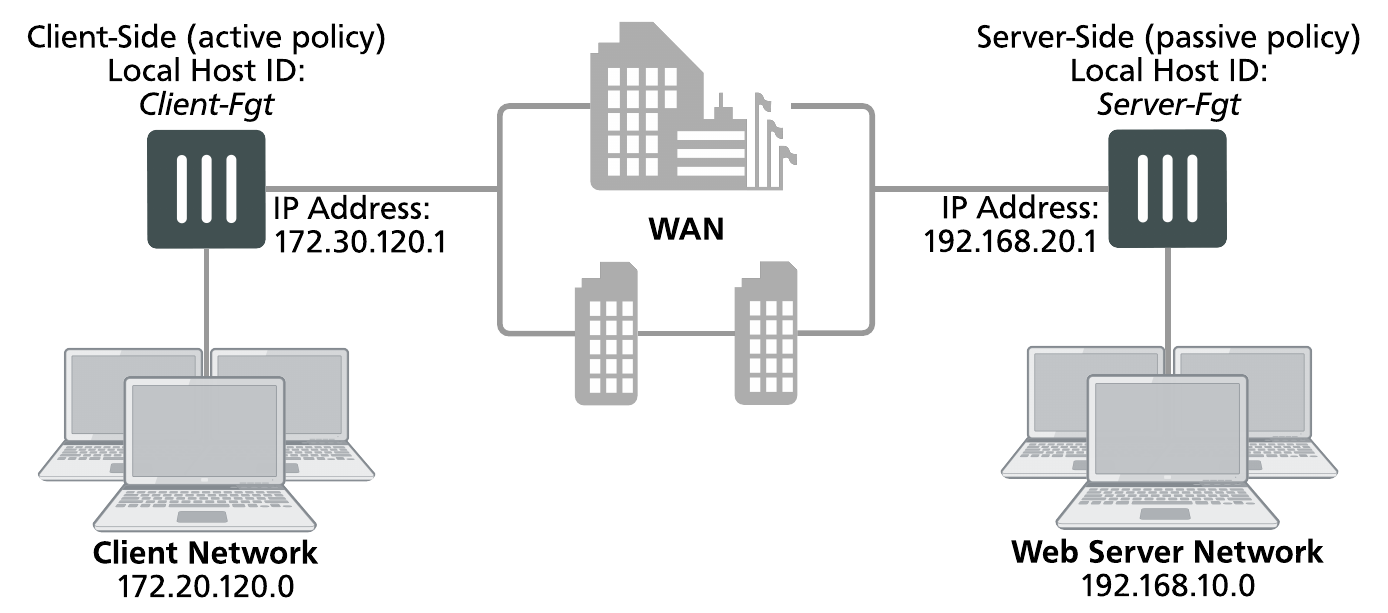
The authentication group is named Auth-Secure-Tunnel and the password for the pre-shared key is 2345678. The topology for this example is shown below. This example includes GUI configuration steps followed by equivalent CLI configuration steps. For information about secure tunneling, see .
Network topology and assumptions
This example configuration includes a client-side FortiGate unit called Client-net with a WAN IP address of 172.30.120.1.This unit is in front of a network with IP address 172.20.120.0. The server-side FortiGate unit is called Web-servers and has a WAN IP address of 192.168.20.1. This unit is in front of a web server network with IP address 192.168.10.0.
Example active-passive WAN optimization and secure tunneling topology
General configuration steps
This section breaks down the configuration for this example into smaller procedures. For best results, follow the procedures in the order given:
- Configure the client-side FortiGate unit:
- Add peers.
- Add an authentication group.
- Add an active WAN optimization policy.
- Configure the server-side FortiGate unit.
- Add peers.
- Add the same authentication group
- Add a passive WAN optimization policy that applies application control.
- Add a WAN optimization tunnel policy.
Note that if you perform any additional actions between procedures, your configuration may have different results.
Configuring WAN optimization with secure tunneling - GUI
Use the following steps to configure the example WAN optimization configuration from the client-side and server-side FortiGate unit GUI. (CLI steps follow.)
To configure the client-side FortiGate unit
- Go to WAN Opt. & Cache > Peersand enter a Local Host ID for the client-side FortiGate unit:
Local Host ID Client-Fgt - Select Apply to save your setting.
- Select Create New and add a Peer Host ID and the IP Address for the server-side FortiGate unit:
Peer Host ID Server-Fgt IP Address 192.168.20.1 - Select OK.
- Go to WAN Opt. & Cache > Authentication Groups and select Create New to add the authentication group to be used for secure tunneling:
Name Auth-Secure-Tunnel Authentication Method Pre-shared key Password 2345678 Peer Acceptance Accept Any Peer - Select OK.
- Go to WAN Opt. & Cache > Profiles and select Create New to add a WAN optimization profile that enables secure tunneling and includes the authentication group:
Name Secure-wan-op-pro Transparent Mode Select Authentication Group Auth-Secure-tunnel - Select the HTTP protocol, select Secure Tunneling and Byte Caching and set the Port to 80.
- Select OK.
- Go to Policy & Objects > Addresses and select Create New to add a firewall address for the client network.
Category Address Name Client-Net Type Subnet Subnet / IP Range 172.20.120.0/24 Interface port1 - Select Create New to add a firewall address for the web server network.
Category Address Address Name Web-Server-Net Type Subnet Subnet / IP Range 192.168.10.0/24 Interface port2 - Go to Policy & Objects > IPv4 Policy and select Create New to add an active WAN optimization security policy:
Incoming Interface port1 Source Address Client-Net Outgoing Interface port2 Destination Address Web-Server-Net Schedule always Service HTTP Action ACCEPT - Turn on WAN Optimization and configure the following settings:
WAN Optimization active Profile Secure-wan-opt-pro - Select OK.
To configure the server-side FortiGate unit
- Go to WAN Opt. & Cache > Peersand enter a Local Host ID for the server-side FortiGate unit:
- Select Apply to save your setting.
- Select Create New and add a Peer Host ID and the IP Address for the client-side FortiGate unit:
Peer Host ID Client-Fgt IP Address 172.30.120.1 - Select OK.
- Go to WAN Opt. & Cache > Authentication Groups and select Create New and add an authentication group to be used for secure tunneling:
Name Auth-Secure-Tunnel Authentication Method Pre-shared key Password 2345678 Peer Acceptance Accept Any Peer - Select OK.
- Go to Policy & Objects > Addresses and select Create New to add a firewall address for the client network.
Category Address Name Client-Net Type Subnet Subnet / IP Range 172.20.120.0/24 Interface port1 - Select Create New to add a firewall address for the web server network.
Category Address Address Name Web-Server-Net Type Subnet Subnet / IP Range 192.168.10.0/24 Interface port2 - Select OK.
- Select Create New to add a passive WAN optimization policy that applies application control.
Incoming Interface port2 Source Address Client-Net Outgoing Interface port1 Destination Address Web-Server-Net Schedule always Service ALL Action ACCEPT - Turn on WAN Optimization and configure the following settings:
WAN Optimization passive Passive Option default - Select OK.
- From the CLI enter the following command to add a WAN optimization tunnel explicit proxy policy.
configure firewall proxy-policy
edit 0
set proxy wanopt
set dstintf port1
set srcaddr all
set dstaddr all
set action accept
set schedule always
set service ALL
end
| Local Host ID | Server-Fgt |
Configuring WAN optimization with secure tunneling - CLI
Use the following steps to configure the example WAN optimization configuration from the client-side and server-side FortiGate unit CLI.
To the client-side FortiGate unit
- Add the Local Host ID to the client-side FortiGate configuration:
config wanopt settings
set host-id Client-Fgt
end
- Add the server-side Local Host ID to the client-side peer list:
config wanopt peer
edit Server-Fgt
set ip 192.168.20.1
end
- Add a new authentication group to be used for secure tunneling:
config wanopt auth-group
edit Auth-Secure-Tunnel
set auth-method psk
set psk 2345678
end
Leave
peer-acceptat its default value. - Add a WAN optimization profile that enables secure tunneling and includes the authentication group, enables HTTP protocol optimization, and enables secure tunneling and byte caching for HTTP traffic:
config wanopt profile
edit Secure-wan-op-pro
set auth-group Auth-Secure-Tunnel
config http
set status enable
set secure-tunnel enable
set byte-caching enable
set port 80
end
end
- Add a firewall address for the client network.
config firewall address
edit Client-Net
set type ipmask
set subnet 172.20.120.0 255.255.255.0
set associated-interface port1
end
- Add a firewall address for the web server network.
config firewall address
edit Web-Server-Net
set type ipmask
set subnet 192.168.10.0 255.255.255.0
set associated-interface port2
end
- Add an active WAN optimization security policy that includes the WAN optimization profile that enables secure tunneling and that applies virus scanning:
config firewall policy
edit 0
set srcintf port1
set dstintf port2
set srcaddr Client-Net
set dstaddr Web-Server-Net
set action accept
set service HTTP
set schedule always
set wanopt enable
set wanopt-detection active
set wanopt-profile Secure-wan-opt-pro
end
To configure the server-side FortiGate unit
- Add the Local Host ID to the server-side FortiGate configuration:
config wanopt settings
set host-id Server-Fgt
end
- Add the client-side Local Host ID to the server-side peer list:
config wanopt peer
edit Client-Fgt
set ip 172.20.120.1
end
- Add an authentication group to be used for secure tunneling:
config wanopt auth-group
edit Auth-Secure-Tunnel
set auth-method psk
set psk 2345678
end
Leave
peer-acceptat its default value. - Add a firewall address for the client network.
config firewall address
edit Client-Net
set type ipmask
set subnet 172.20.120.0 255.255.255.0
set associated-interface port1
end
- Add a firewall address for the web server network.
config firewall address
edit Web-Server-Net
set type ipmask
set subnet 192.168.10.0 255.255.255.0
set associated-interface port2
end
- Add a passive WAN optimization policy.
config firewall policy
edit 0
set srcintf port1
set dstintf port2
set srcaddr Client-Net
set dstaddr Web-Server-Net
set action accept
set service ALL
set schedule always
set wanopt enable
set wanopt-detection passive
set wanopt-passive-opt default
end
- Add a WAN optimization tunnel explicit proxy policy.
configure firewall proxy-policy
edit 0
set proxy wanopt
set dstintf port1
set srcaddr all
set dstaddr all
set action accept
set schedule always
set service ALL
end

