Configuration examples
This section consists of the following configuration examples:
- Site-to-site IPv6 over IPv6 VPN example
- Site-to-site IPv6 over IPv4 VPN example
- Site-to-site IPv4 over IPv6 VPN example
Site-to-site IPv6 over IPv6 VPN example
In this example, computers on IPv6-addressed private networks communicate securely over public IPv6 infrastructure.
|
|
By default IPv6 configurations do not appear on the GUI. You need to enable the feature first. |
Example IPv6-over-IPv6 VPN topology
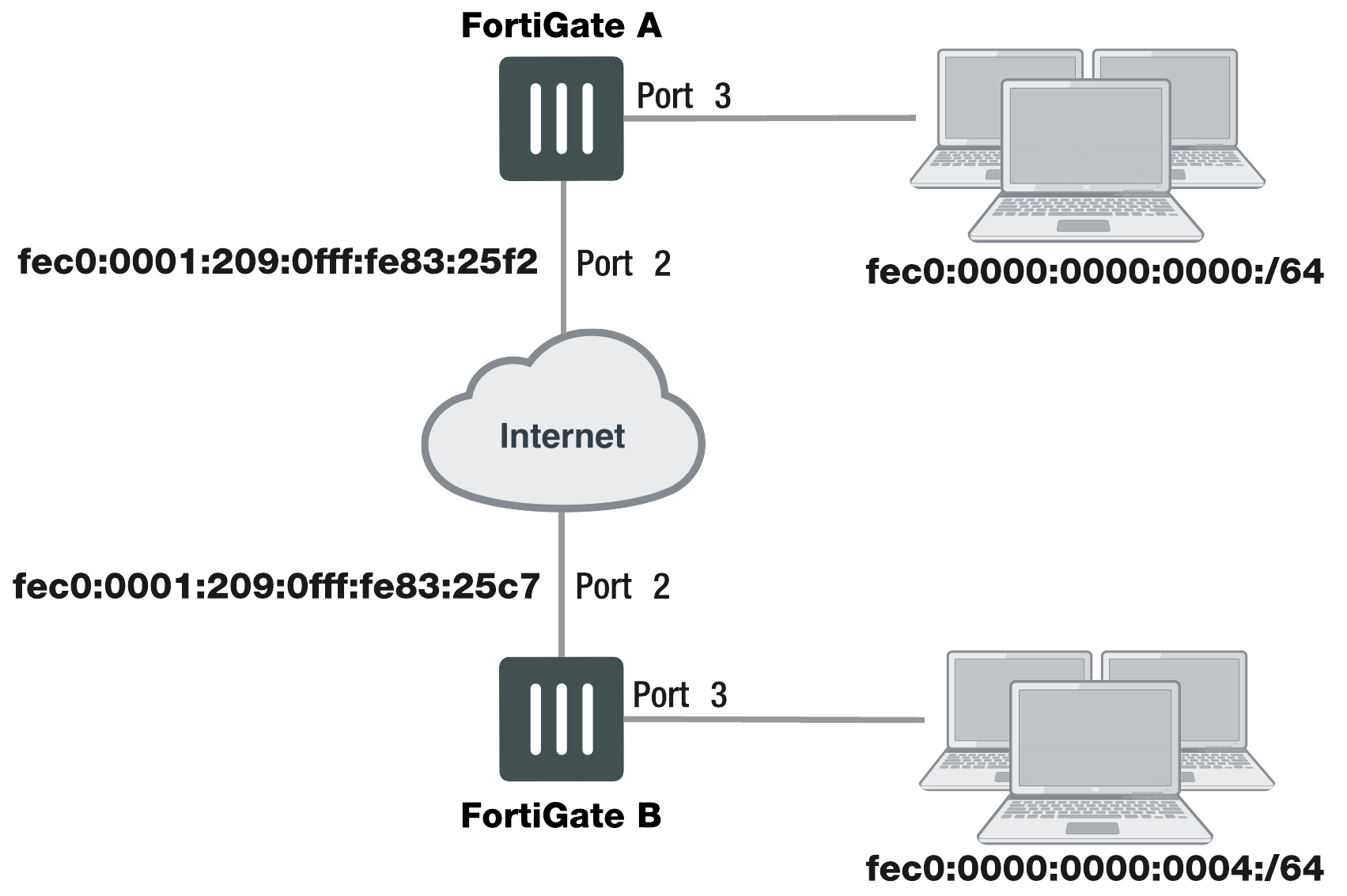
Configure FortiGate A interfaces
Port 2 connects to the public network and port 3 connects to the local network.
config system interface
edit port2
config ipv6
set ip6-address fec0::0001:209:0fff:fe83:25f2/64
end
next
edit port3
config ipv6
set ip6-address fec0::0000:209:0fff:fe83:25f3/64
end
next
end
Configure FortiGate A IPsec settings
The Phase 1 configuration creates a virtual IPsec interface on port 2 and sets the remote gateway to the public IP address FortiGate B. This configuration is the same as for an IPv4 route-based VPN, except that ip-version is set to 6 and the remote-gw6 keyword is used to specify an IPv6 remote gateway address.
config vpn ipsec phase1-interface
edit toB
set ip-version 6
set interface port2
set remote-gw6 fec0:0000:0000:0003:209:0fff:fe83:25c7
set dpd [disable | on-idle | on-demand]
set psksecret maryhadalittlelamb
set proposal 3des-md5 3des-sha1
end
By default, Phase 2 selectors are set to accept all subnet addresses for source and destination. The default setting for src-addr-type and dst-addr-type is subnet. The IPv6 equivalent is subnet6. The default subnet addresses are 0.0.0.0/0 for IPv4, ::/0 for IPv6.
config vpn ipsec phase2-interface
edit toB2
set phase1name toB
set proposal 3des-md5 3des-sha1
set pfs enable
set replay enable
set src-addr-type subnet6
set dst-addr-type subnet6
end
Configure FortiGate A security policies
Security policies are required to allow traffic between port3 and the IPsec interface toB in each direction. The address all6 must be defined using the firewall address6 command as ::/0.
config firewall policy6
edit 1
set srcintf port3
set dstintf toB
set srcaddr all6
set dstaddr all6
set action accept
set service ALL
set schedule always
next
edit 2
set srcintf toB
set dstintf port3
set srcaddr all6
set dstaddr all6
set action accept
set service ALL
set schedule always
end
Configure FortiGate A routing
This simple example requires just two static routes. Traffic to the protected network behind FortiGate B is routed via the virtual IPsec interface toB using an IPv4 static route. A default route sends all IPv6 traffic, including the IPv6 IPsec packets, out on port2.
config router static6
edit 1
set device port2
set dst 0::/0
next
end
config router static
edit 1
set device toB
set dst 192.168.3.0/24
next
end
Configure FortiGate B
The configuration of FortiGate B is very similar to that of FortiGate A. A virtual IPsec interface toA is configured on port2 and its remote gateway is the public IP address of FortiGate A. Security policies enable traffic to pass between the private network and the IPsec interface. Routing ensures traffic for the private network behind FortiGate A goes through the VPN and that all IPv6 packets are routed to the public network.
config system interface
edit port2
config ipv6
set ip6-address fec0::0003:209:0fff:fe83:25c7/64
end
next
edit port3
config ipv6
set ip6-address fec0::0004:209:0fff:fe83:2569/64
end
end
config vpn ipsec phase1-interface
edit toA
set ip-version 6
set interface port2
set remote-gw6 fec0:0000:0000:0001:209:0fff:fe83:25f2
set dpd [disable | on-idle | on-demand]
set psksecret maryhadalittlelamb
set proposal 3des-md5 3des-sha1
end
config vpn ipsec phase2-interface
edit toA2
set phase1name toA
set proposal 3des-md5 3des-sha1
set pfs enable
set replay enable
set src-addr-type subnet6
set dst-addr-type subnet6
end
config firewall policy6
edit 1
set srcintf port3
set dstintf toA
set srcaddr all6
set dstaddr all6
set action accept
set service ALL
set schedule always
next
edit 2
set srcintf toA
set dstintf port3
set srcaddr all6
set dstaddr all6
set action accept
set service ALL
set schedule always
end
config router static6
edit 1
set device port2
set dst 0::/0
next
edit 2
set device toA
set dst fec0:0000:0000:0000::/64
end
Site-to-site IPv6 over IPv4 VPN example
In this example, IPv6-addressed private networks communicate securely over IPv4 public infrastructure.
Example IPv6-over-IPv4 VPN topology
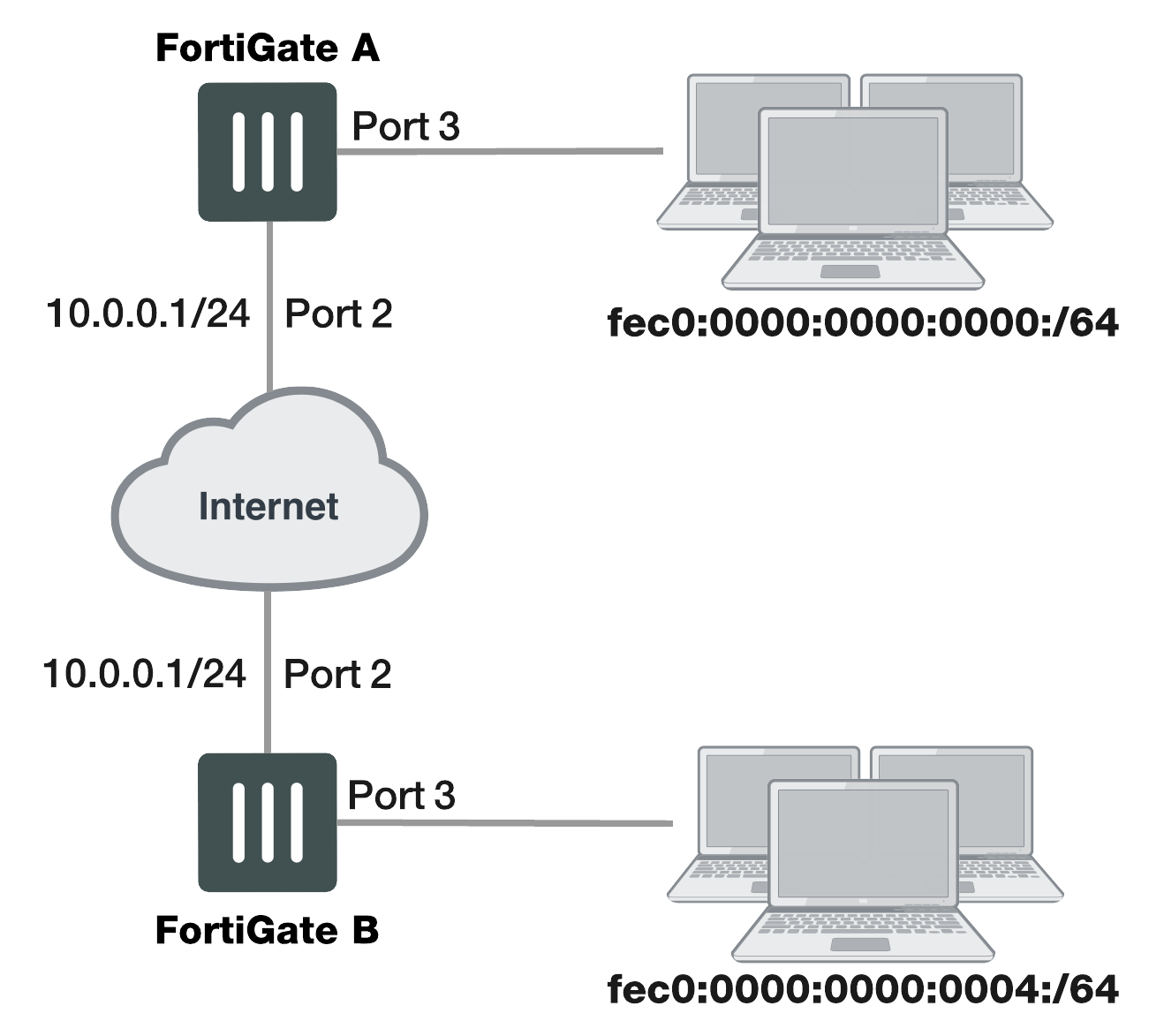
Configure FortiGate A interfaces
Port 2 connects to the IPv4 public network and port 3 connects to the IPv6 LAN.
config system interface
edit port2
set 10.0.0.1/24
next
edit port3
config ipv6
set ip6-address fec0::0001:209:0fff:fe83:25f3/64
end
Configure FortiGate A IPsec settings
The Phase 1 configuration uses IPv4 addressing.
config vpn ipsec phase1-interface
edit toB
set interface port2
set remote-gw 10.0.1.1
set dpd [disable | on-idle | on-demand]
set psksecret maryhadalittlelamb
set proposal 3des-md5 3des-sha1
end
The Phase 2 configuration uses IPv6 selectors. By default, Phase 2 selectors are set to accept all subnet addresses for source and destination. The default setting for sr-addr-type and dst-addr-type is subnet. The IPv6 equivalent is subnet6. The default subnet addresses are 0.0.0.0/0 for IPv4, ::/0 for IPv6.
config vpn ipsec phase2-interface
edit toB2
set phase1name toB
set proposal 3des-md5 3des-sha1
set pfs enable
set replay enable
set src-addr-type subnet6
set dst-addr-type subnet6
end
Configure FortiGate A security policies
IPv6 security policies are required to allow traffic between port3 and the IPsec interface toB in each direction. Define the address all6 using the firewall address6 command as ::/0.
config firewall policy6
edit 1
set srcintf port3
set dstintf toB
set srcaddr all6
set dstaddr all6
set action accept
set service ALL
set schedule always
next
edit 2
set srcintf toB
set dstintf port3
set srcaddr all6
set dstaddr all6
set action accept
set service ALL
set schedule always
end
Configure FortiGate A routing
This simple example requires just two static routes. Traffic to the protected network behind FortiGate B is routed via the virtual IPsec interface toB using an IPv6 static route. A default route sends all IPv4 traffic, including the IPv4 IPsec packets, out on port2.
config router static6
edit 1
set device toB
set dst fec0:0000:0000:0004::/64
next
end
config router static
edit 1
set device port2
set dst 0.0.0.0/0
set gateway 10.0.0.254
next
end
Configure FortiGate B
The configuration of FortiGate B is very similar to that of FortiGate A. A virtual IPsec interface toA is configured on port2 and its remote gateway is the IPv4 public IP address of FortiGate A. The IPsec Phase 2 configuration has IPv6 selectors.
IPv6 security policies enable traffic to pass between the private network and the IPsec interface. An IPv6 static route ensures traffic for the private network behind FortiGate A goes through the VPN and an IPv4 static route ensures that all IPv4 packets are routed to the public network.
config system interface
edit port2
set 10.0.1.1/24
next
edit port3
config ipv6
set ip6-address fec0::0004:209:0fff:fe83:2569/64
end
config vpn ipsec phase1-interface
edit toA
set interface port2
set remote-gw 10.0.0.1
set dpd [disable | on-idle | on-demand]
set psksecret maryhadalittlelamb
set proposal 3des-md5 3des-sha1
end
config vpn ipsec phase2-interface
edit toA2
set phase1name toA
set proposal 3des-md5 3des-sha1
set pfs enable
set replay enable
set src-addr-type subnet6
set dst-addr-type subnet6
end
config firewall policy6
edit 1
set srcintf port3
set dstintf toA
set srcaddr all6
set dstaddr all6
set action accept
set service ALL
set schedule always
next
edit 2
set srcintf toA
set dstintf port3
set srcaddr all6
set dstaddr all6
set action accept
set service ALL
set schedule always
end
config router static6
edit 1
set device toA
set dst fec0:0000:0000:0000::/64
end
config router static
edit 1
set device port2
set gateway 10.0.1.254
end
Site-to-site IPv4 over IPv6 VPN example
In this example, two private networks with IPv4 addressing communicate securely over IPv6 infrastructure.
Example IPv4-over-IPv6 VPN topology

Configure FortiGate A interfaces
Port 2 connects to the IPv6 public network and port 3 connects to the IPv4 LAN.
config system interface
edit port2
config ipv6
set ip6-address fec0::0001:209:0fff:fe83:25f2/64
end
next
edit port3
set 192.168.2.1/24
end
Configure FortiGate A IPsec settings
The Phase 1 configuration is the same as in the IPv6 over IPv6 example.
config vpn ipsec phase1-interface
edit toB
set ip-version 6
set interface port2
set remote-gw6 fec0:0000:0000:0003:209:0fff:fe83:25c7
set dpd [disable | on-idle | on-demand]
set psksecret maryhadalittlelamb
set proposal 3des-md5 3des-sha1
end
The Phase 2 configuration is the same as you would use for an IPv4 VPN. By default, Phase 2 selectors are set to accept all subnet addresses for source and destination.
config vpn ipsec phase2-interface
edit toB2
set phase1name toB
set proposal 3des-md5 3des-sha1
set pfs enable
set replay enable
end
Configure FortiGate A security policies
Security policies are required to allow traffic between port3 and the IPsec interface toB in each direction. These are IPv4 security policies.
config firewall policy
edit 1
set srcintf port3
set dstintf toB
set srcaddr all
set dstaddr all
set action accept
set service ALL
set schedule always
next
edit 2
set srcintf toB
set dstintf port3
set srcaddr all
set dstaddr all
set action accept
set service ALL
set schedule always
end
Configure FortiGate A routing
This simple example requires just two static routes. Traffic to the protected network behind FortiGate B is routed via the virtual IPsec interface toB using an IPv4 static route. A default route sends all IPv6 traffic, including the IPv6 IPsec packets, out on port2.
config router static6
edit 1
set device port2
set dst 0::/0
next
end
config router static
edit 2
set device toB
set dst 192.168.3.0/24
next
end
Configure FortiGate B
The configuration of FortiGate B is very similar to that of FortiGate A. A virtual IPsec interface toA is configured on port2 and its remote gateway is the public IP address of FortiGate A. The IPsec Phase 2 configuration has IPv4 selectors.
IPv4 security policies enable traffic to pass between the private network and the IPsec interface. An IPv4 static route ensures traffic for the private network behind FortiGate A goes through the VPN and an IPv6 static route ensures that all IPv6 packets are routed to the public network.
config system interface
edit port2
config ipv6
set ip6-address fec0::0003:fe83:25c7/64
end
next
edit port3
set 192.168.3.1/24
end
config vpn ipsec phase1-interface
edit toA
set ip-version 6
set interface port2
set remote-gw6 fec0:0000:0000:0001:209:0fff:fe83:25f2
set dpd [disable | on-idle | on-demand]
set psksecret maryhadalittlelamb
set proposal 3des-md5 3des-sha1
end
config vpn ipsec phase2-interface
edit toA2
set phase1name toA
set proposal 3des-md5 3des-sha1
set pfs enable
set replay enable
end
config firewall policy
edit 1
set srcintf port3
set dstintf toA
set srcaddr all
set dstaddr all
set action accept
set service ALL
set schedule always
next
edit 2
set srcintf toA
set dstintf port3
set srcaddr all
set dstaddr all
set action accept
set service ALL
set schedule always
end
config router static6
edit 1
set device port2
set dst 0::/0
next
edit 2
set device toA
set dst 192.168.2.0/24
end

