IPsec VPN for iOS 9
In this recipe, you will use the FortiGate IPsecVPN Wizard to set up an IPsec VPN between a FortiGate and a device running iOS 9. This configuration allows iPhone users to securely connect to an internal network.
The IPsec VPN is a pre-shared key configuration that also requires users to authenticate with their own credentials to be able to connect to the VPN.
This recipe assumes that a user (dbuchanan) and a user group (iphone-users) have already been created on the FortiGate.
An Apple iPhone SE running iOS 9.3.5 was used for this configuration.

1. Configuring the IPsec VPN using the IPsec VPN Wizard
On the FortiGate, go to VPN > IPsec Wizard.
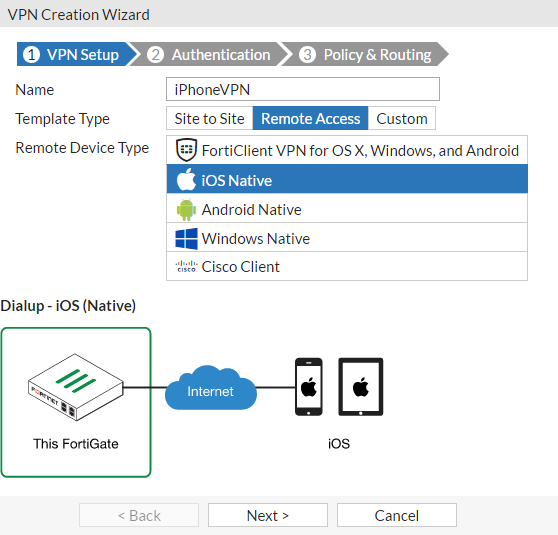
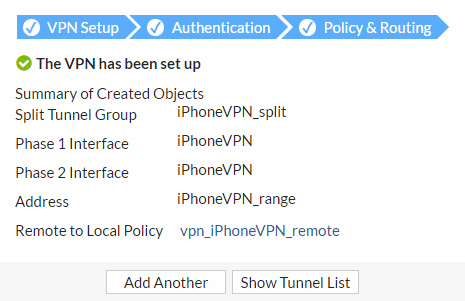
Name the VPN connection (iPhoneVPN).
Select the Remote Access template, select the iOS Native device type, and select Next.
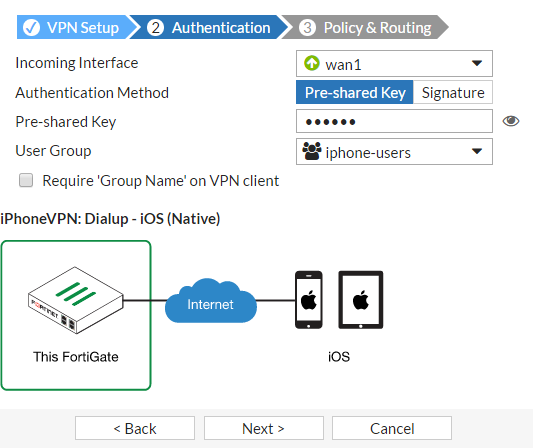
Set the Incoming Interface to the Internet-facing interface (wan1).
Select the Pre-shared Key authentication method and enter a pre-shared key.
Select the iphone-users user group and select Next.
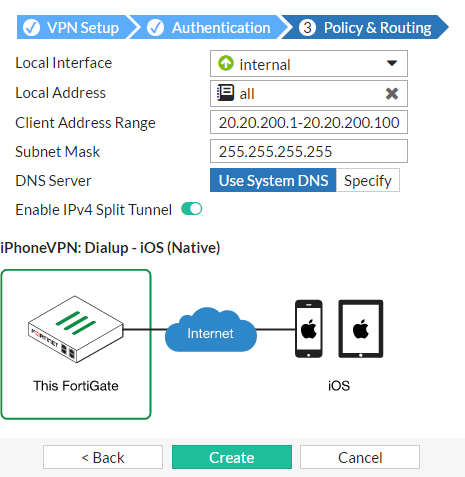
Set Local Interface to the internal interface and set Local Address to all.
Enter an IP address range for VPN users in the Client Address Range field, enter a Subnet Mask, and select Create.
Make sure no other interfaces on the FortiGate are using the same address range.
A summary page shows the wizard's configuration, including a remote-to-local access security policy.
2. Connecting to the IPsec VPN from iPhone
On the iPhone, go to Settings > General > VPN and select Add VPN Configuration.
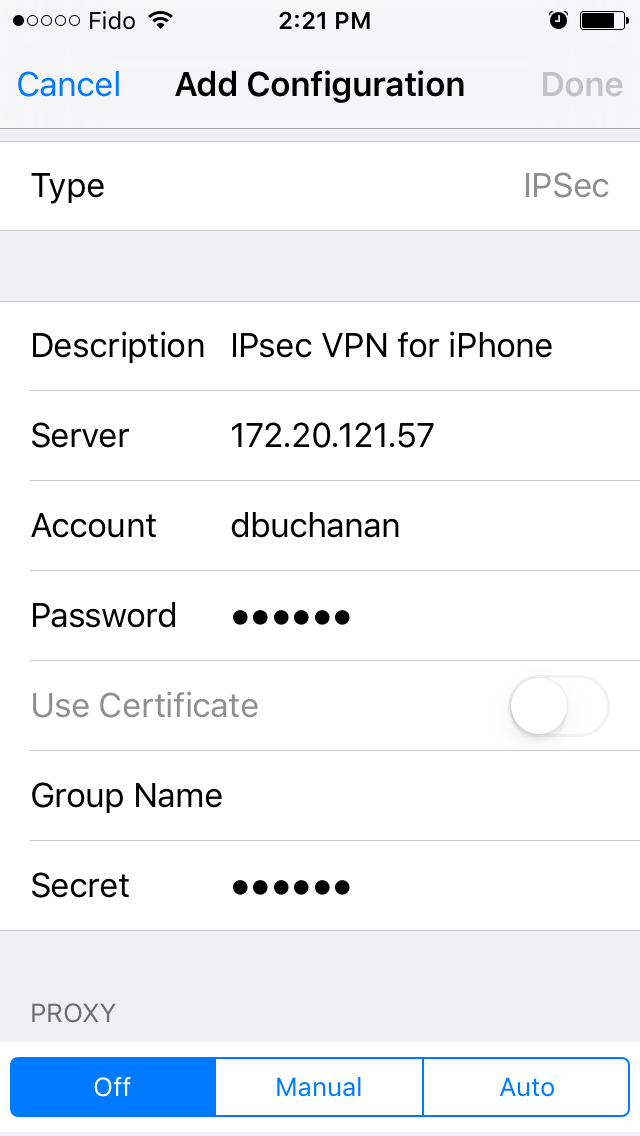
Set Type to IPsec and enter a Description (required).
Set Server to the FortiGate's Internet-facing interface, and enter the user's name in Account.
Enter the user's password, the pre-shared IPsec VPN secret, and select Done.
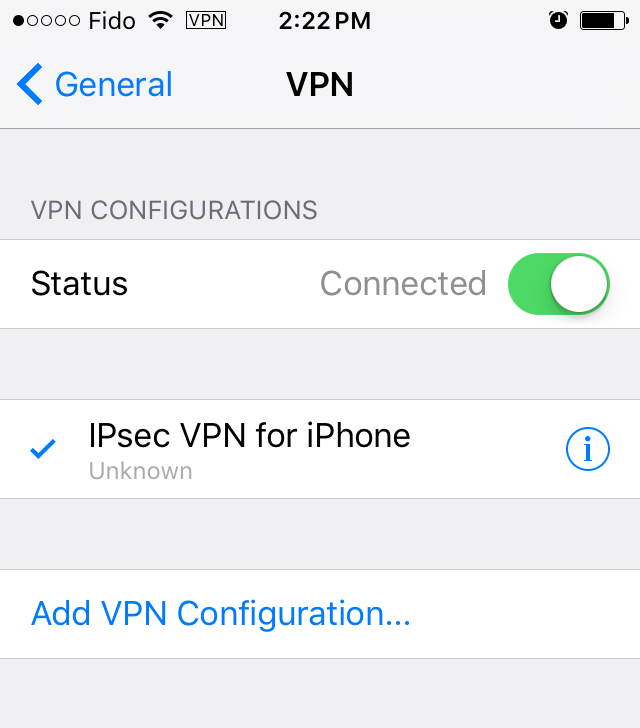
Make sure the IPsec VPN configuration is highlighted (indicated by the ✓ icon), and select the button next to Not Connected.

The IPsec VPN will connect with the user's credentials and secret. The status will change to Connected, and a VPN icon will appear at the top of the screen.
3. Results
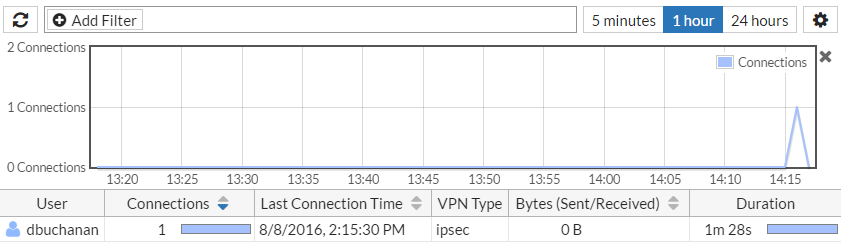
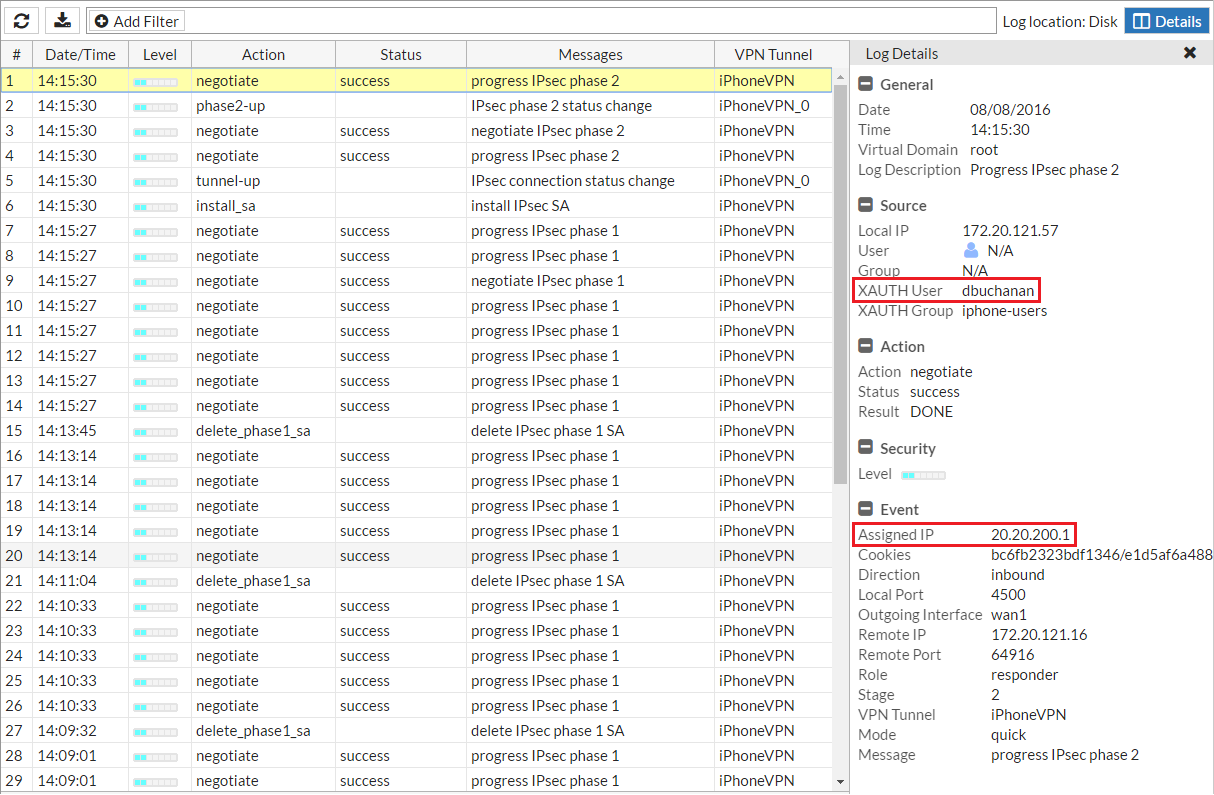
To verify the connection, on the FortiGate, go to Log & Report > VPN Events. The user has been assigned an IP from the client address range.
You may also verify the user's connection by going to FortiView > VPN.